 An AFP report earlier today reveals that the Stuxnet malware has been found at Iran’s nuclear power plant at Bushehr. (All the blockquotes below are from the AFP report.)
An AFP report earlier today reveals that the Stuxnet malware has been found at Iran’s nuclear power plant at Bushehr. (All the blockquotes below are from the AFP report.)
Iranian officials confirm that 30,000 industrial computers in Iran have been hit by Stuxnet yet deny that Bushehr was among those infected.
That might be what Iranian officials believe, but whether it’s a belief based on fact is another matter.
As we get further into this report, it becomes apparent there is a high probability both that Bushehr has been penetrated and that the malware may still be active.
Siemens said its software has not been installed at the plant, and an Iranian official denied the malware may have infected nuclear facilities.
Siemens might not know that its software was installed at the plant, but thanks to a UPI photograph, we know that Bushehr control systems do indeed run on Siemens’ WinCC SCADA system. The warning shown below says: “WinCC Runtime License: Your software license has expired. Please obtain a valid license.”
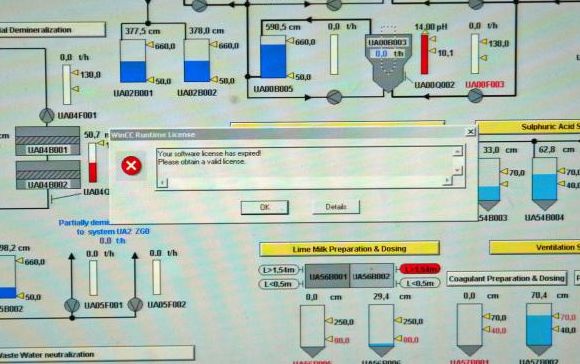
This is what Ralph Langner, a German industrial security expert, saw as a red flag indicating that the plant is vulnerable to a cyber attack.
“This virus has not caused any damage to the main systems of the Bushehr power plant,” Bushehr project manager Mahmoud Jafari said on Iran’s Arabic-language Al-Alam television network.
“All computer programmes in the plant are working normally and have not crashed due to Stuxnet,” said Jafari, adding there was no problem with the plant’s fuel supply.
The official IRNA news agency meanwhile quoted him as saying the worm had infected some “personal computers of the plant’s personnel.”
And no infected personal computers have been hooked into the plants control system?
As indicated in this photograph showing Russian contractors inside Bushehr, the path from a personal computer to the plant’s control system is short and direct.

As for the fact that Bushehr’s control system has not crashed, the fact that the project manager cites this as evidence that the system is malware-free suggests that he does not understand how Stuxnet is designed. Stuxnet monitors process conditions and until those conditions have been met, everything should work fine. This is not like a virus that slows down an operating system.
Given the inside knowledge that Stuxnet’s creators required, it seems quite likely that the moment they would want it to kick into action — assuming that Bushehr was the intended target — would be a moment at which a catastrophic system failure could be attributed to a flaw in the facility’s construction, design or operation. A failure, for instance, as the plant approaches its intended full operational generation capacity. The 1000 megawatt plant is expected to have reached only 40% capacity by the end of December.
Telecommunications minister Reza Taqipour said “the worm has not been able to penetrate or cause serious damage to government systems.”
Again, this statement suggests a lack of understanding about Stuxnet’s highly targeted design and the fact that it is designed not to cause damage elsewhere.
Mahmoud Liayi, head of the information technology council at the ministry of industries said:
…industries were currently receiving systems to combat Stuxnet, while stressing Iran had decided not to use anti-virus software developed by Siemens because “they could be carrying a new version of the malware.”
“When Stuxnet is activated, the industrial automation systems start transmitting data about production lines to a main designated destination by the virus,” Liayi said.
“There, the data is processed by the worm’s architects and then engineer plots to attack the country.”
If this is the official consensus, Iranian facilities such as Bushehr are as vulnerable now as they were before anyone knew about Stuxnet. Liayi’s statement suggests that Stuxnet is being viewed as a tool of espionage designed to facilitate rather than execute sabotage.


I believed initially that this was more hype than attack. I still think that is more likely. However, knowing next to nothing about computers, viruses and worms, I have to take your analysis seriously.
If it is true that the Israelis intended to cause an Iranian Chernobyl, they are truly too clever by half. Now that this out in the open and reported on internationally, any problems with Bushehr will be at their doorstep. Even if the accident is due to other causes. Any accident at Busheher or Natanz or anywhere else in Iran will have everyone in Iran suspecting Israel. World leaders in Europe, Russia and China will also have their suspicions. Since it is a Russian designed plant, they will have an incentive in blaming Israel too.
The Israelis are playing with fire. Shielded so long from the consequences of their actions, they do not seem to understand what will happen if they earn the undying enmity of 70 million Iranians. They don’t know how hot that fire will burn. Were I them, I would be hoping the Iranians figure out a way to stop this worm before it does permanent damage.
The screenshot refers to ‘sulphuric acid’ and ‘lime mill’. Dis information is more likely to be from a uranium extraction plant than a nuclear power plant.
Egbert is right that there’s no real proof that the screen shot came from Bushehr.
Lysander is also right that if a nuclear accident does happen, it will be put at Israel’s door, even if it were a real accident. Israel doesn’t care about dropping nuclear weapons on people, so they wouldn’t understand what an effect it would have on other people round the world, who do care about nuclear weapons.
There is still no smoking gun for the virus, which targets Siemens SCADA software and which has appeared in 155 countries (but mainly Iran, Indonesia, and India). We don’t know if the appearance of the virus was accidental (USB shipments to “I” countries) or intended mainly for Iran. If it was intended to target Iran, we don’t know for a fact that it was intended for one of its nuclear facilities. And if it was intended for one of its nuclear facilities, we don’t know if it was the Israelis or the US who was responsible.
In short, this is still at the stage of conjecture heaped upon conjecture heaped upon more conjecture.
Paul, I don’t know if anyone has pointed out that Israel in fact needs a nuclear threat from Iran in order to justify its own nuclear armaments. Without such a threat Israel’s nuclear WMD are just the manifestation of their ultimate menace to their relatively unarmed neighbours. At present Israel is not threatened by any nuclear armed country. In other words, if a nuclear armed Israel used these WMD to attack a non-nuclear adversary it would be a war crime under present circumstances, but if Iran or another adversary country to the Zionist state possessed nuclear weapons Israel could claim they have these weapons for “strategic defence”. At the moment the Israelis and there nukes can only be seen as “offensive” in their stance, and thereby despite the bought votes at the IAEA last week Israel is the major and maybe the only cause preventing a non-nuclear armed Middle East and equally will be the cause of any proliferation.
Therefore disarming Israel should be not only the Middle Easern countries’ but also the west’s priority, rather than pandering to Zionist ambitions of American style regional domination. Personally I think the prostration of the IAEA to Zionist and American designs under its new head, Yukiya Amano, is far more important and a threat to world security than this cyber attack on the nuclear facilities.
For Ian:
Totally incorrect sir, Little Satan’s new clear ambiguity has it’s place in prevention of conventional warfare. Indeed – what brave leaders of Arab League would dare launch conscript infantry, panzers or combat jets against Little Satan in open warfare? It has kept the peace betwixt nation states in the ME since before Soviet Union gave up the ghost.
Any ideas of stripping it away are quite risible. It would start a war or series of wars that would result in an uberNakbah – most likely with Little Satan winning turf from Nile to Euphrates – and probably not inclined to give it back.
Disarming Little Satan is a dangerous idea, anti democratic and a ‘priority’ only for warmongers. She enjoys a tolerant, egalitarian society with a penchant for periodic transparent elections, a free uncensored media, a military under civie command, an independent judiciary under elected gov oversight and a nat’l treasury open to public scrutiny.
Ian,
While I see you’re point that Israel benefits (marginally) from having a nuclear Iran as an excuse, it benefits much MUCH more from having a nuclear monopoly. Far from pressing Israel to declare its arsenal and disarm, the US and the west are running interference, pretending that the nukes don’t even exist. The only reason there is any pressure at all on Israel in that regard is because of Iran’s program and the obvious hypocrisy of the Western position. If Iran halted enrichment today, you would see even this minimal pressure on Israel evaporate.
Also, I would add that I honestly don’t believe Iran will ever actually build nukes. It *will* assemble everything it needs to build them on short notice. That would be especially delicate for Israel, as it offers a counter-example of a responsible potential nuclear state, while at the same time blunting Israel’s nuclear monopoly. The world will have less tolerance for threats on Iran if they think it will just provoke them to “turn the screw” and become fully nuclear.
Do you have a problem with women, courtney109? Your reference to a disgusting little rogue State devoid of any moral compass as “she” is a gross insult to women. You might care to ask Arab Israelis or Palestinians about the “tolerant egalitarian society”, the “independent judiciary” and the “civic command which controls the military”. Suggest also, that the uncritical support, money and technology transfer from the US, and the refusal of this sponsor to reign-in the monster that it has helped create, has as much to do with the current situation in the Middle East as the possession of nuclear weapons.
Hi Paul, I see nothing credible in your blog post that substantiates the speculative claims that Bushehr utilizes a Siemens SCADA system. The reasons are as follows.
Concerning the UPI image of a control panel with a MS look window superimposed that says..”“WinCC Runtime License: Your software license has expired. Please obtain a valid license”, well it doesn’t prove a thing.
First of all, the WinCC window could so easily be a photo- shopped overlay on the image of a process control panel.
Secondly, the Control Panel image is typical of process control panels everywhere and even if the WinCC window was not photo-shopped, what has that got to do with Bushehr. There is nothing else in the image to provide any information whatsoever about the local environment to provide any context as to its locality or purpose.
Thirdly, UPI does not provide a source for anyone claiming that the UPI Photo by Mohammad Kheirkhah is actually Bushehr, they just provide a narrative to imply that it is.
Fourthly, Ralph Lagner is not claiming the UPI image is actually genuine or that it is of Bushehr, he merely prefaces his speculative theory with ” If the picture is authentic, which I have no means of verifying,….”.
It seems it is only you Paul who make the claim,…”Siemens might not know that its software was installed at the plant, but thanks to a UPI photograph, we know that Bushehr control systems do indeed run on Siemens’ WinCC SCADA system.”
BTW, since you use ‘we’ in that statement, who also beside you are claiming to really KNOW for sure?
Also BTW, the Siemens spokesperson not only claimed that Siemens left Iran 30 years ago and that they have had not had any involvement in the reconstruction nor provided any of their hardware or software since, he also noted for the record that “that according to global security standards, Microsoft software may not be used to operate critical processes in plants”.