(Updated below)
In an interview on Bloomberg TV, Richard Falkenrath suggested that Israel is the most likely source of the Stuxnet malware which seems designed to cripple industrial facilities in Iran.
Falkenrath is currently the Deputy Commissioner of Counter-Terrorism for the NYPD and held several positions in the George W Bush White House including Deputy Assistant to the President and Deputy Homeland Security Advisor.
The Associated Press says that experts from Iran’s nuclear agency met this week to discuss how to combat the Stuxnet attack on Iranian facilities, according to the semi-official ISNA news agency.
Iran’s Mehr News Agency adds:
The director of the Information Technology Council of the Industries and Mines Ministry has announced that the IP addresses of 30,000 industrial computer systems infected by this malware have been detected, the Mehr New Agency reported on Saturday.
“An electronic war has been launched against Iran,” Mahmoud Liaii added.
“This computer worm is designed to transfer data about production lines from our industrial plants to (locations) outside of the country,” he said.
He also announced that a working group composed of representatives from the Communications and Information Technology Ministry, the Industries and Mines Ministry, and the Passive Defense Organization has been set up to find ways to combat the spyware.
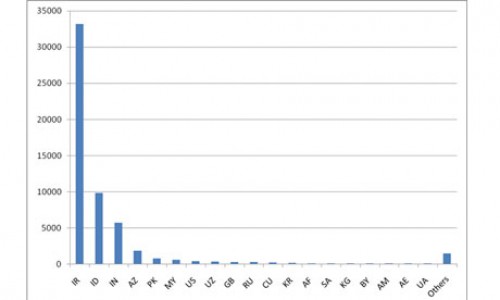
Graph shows concentration of Stuxnet-infected computers in Iran as of August. Source: Symantec
Eugene Kaspersky, co-founder and chief executive officer of Kaspersky Lab, says that the creation of Stuxnet marks the beginning of the new age of cyber-warfare.
Speaking at the Kaspersky Security Symposium with international journalists in Munich, Germany, Kaspersky described Stuxnet as the opening of “Pandora’s Box.”
“This malicious program was not designed to steal money, send spam, grab personal data, no, this piece of malware was designed to sabotage plants, to damage industrial systems,” he said.
“I am afraid this is the beginning of a new world. [The] 90’s were a decade of cyber-vandals, 2000’s were a decade of cybercriminals, I am afraid now it is a new era of cyber-wars and cyber-terrorism,” Kaspersky added.
Among industrial security experts who are convinced that Iran is the target of the Stuxnet attack, a debate has opened up around which facility the malware was designed to strike.
Frank Rieger, a German researcher with GSMK, a Berlin encryption firm, suggests that the Natanz enrichment facility looks like the most likely target. He laid out his reasoning to the Christian Science Monitor.
• Stuxnet had a halt date. Internal time signatures in Stuxnet appear to prevent it from spreading across computer systems after July 2009. That probably means the attack had to be conducted by then – though such time signatures are not certain.
• Stuxnet appears designed to take over centrifuges’ programmable logic controllers. Natanz has thousands of identical centrifuges and identical programmable logic controllers (PLCs), tiny computers for each centrifuge that oversee the centrifuge’s temperature, control valves, operating speed, and flow of cooling water. Stuxnet’s internal design would allow the malware to take over PLCs one after another, in a cookie-cutter fashion.
“It seems like the parts of Stuxnet dealing with PLCs have been designed to work on multiple nodes at once – which makes it fit well with a centrifuge plant like Natanz,” Rieger says. By contrast, Bushehr is a big central facility with many disparate PLCs performing many different functions. Stuxnet seems focused on replicating its intrusion across a lot of identical units in a single plant, he says.
Natanz also may have been hit by Stuxnet in mid-2009, Rieger says. He notes that “a serious, recent, nuclear accident” was reported at that time on WikiLeaks, the same organization that recently revealed US Afghanistan-war documents. About the same time, the BBC reported that the head of Iran’s nuclear agency had resigned.
Lending some credence to the notion that Stuxnet attacked more than a year ago, he says, is the International Atomic Energy Agency’s finding of a sudden 15 percent drop in the number of working centrifuges at the Natanz site.
Even though Natanz would seem like a logical target to choose if the objective of the attackers was to disrupt Iran’s nuclear program, Rieger’s inference — that the halt date preventing Stuxnet spreading means the attack had to take place before July 2009 — is questionable, for at least two reasons.
Firstly, given that the designers had a very specific target, their aim is likely to have been to penetrate that target while trying to limit the proliferation of the malware and thus reduce the risks of the operation’s exposure.
Secondly, code for one of the four zero-day vulnerabilities that the worm exploits was only added in March 2010 — well after the halt date. The fact that the code was being modified at that time suggests that it had yet to perform its function.
As previously reported, another German industrial security expert, Ralph Langner, has speculated that the Bushehr nuclear reactor is the most likely target. He bases this theory on various pieces of circumstantial evidence.
Firstly, it is known that Bushehr uses the Siemens SCADA systems that Stuxnet targets and that access to these systems available to Russian contractors working on the facility would allow the malware to be installed through USB memory sticks.
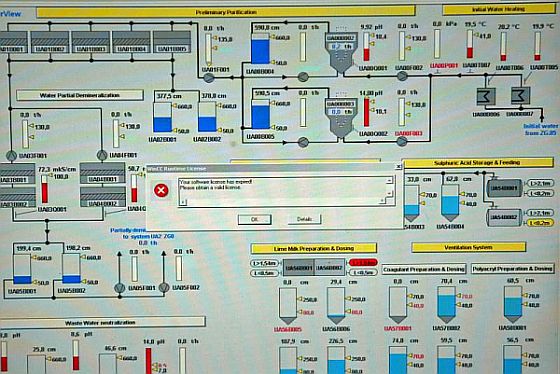
Secondly, photographic evidence shows that the facility had very weak cyber security.
A journalist’s photo from inside the Bushehr plant in early 2009, which Langner found on a public news website, shows a computer-screen schematic diagram of a process control system – but also a small dialog box on the screen with a red warning symbol. Langner says the image on the computer screen is of a Siemens supervisory control and data acquisition (SCADA) industrial software control system called Simatic WinCC – and the little warning box reveals that the software was not installed or configured correctly, and was not licensed. That photo was a red flag that the nuclear plant was vulnerable to a cyberattack, he says.
“Bushehr has all kinds of missiles around it to protect it from an airstrike,” Langner says. “But this little screen showed anyone that understood what that picture meant … that these guys were just simply begging to be [cyber]attacked.”
The picture was reportedly taken on Feb. 25, 2009, by which time the reactor should have had its cybersystems up and running and bulletproof, Langner says. The photo strongly suggests that they were not, he says. That increases the likelihood that Russian contractors unwittingly spread Stuxnet via their USB drives to Bushehr, he says.
“The attackers realized they could not get to the target simply through the Internet – a nuclear plant is not reachable that way,” he says. “But the engineers who commission such plants work very much with USBs like those Stuxnet exploited to spread itself. They’re using notebook computers and using the USBs to connect to one machine, then maybe going 20 yards away to another machine.”
Langner also cites international concern about the Bushehr reactor becoming operational.
This is a somewhat weaker strand of his argument. After all, the existence of this Russian-fueled reactor was widely seen as a demonstration of the fact that Iran could, it it chooses, have a civilian nuclear energy program without any need for a uranium enrichment program.
There is however another argument that can be made in which Bushehr becomes the target of cyberwarfare, even if it might not be a vital node in Iran’s nuclear program. In this scenario, Stuxnet would not be designed to perform its function until the reactor becomes fully operational. At that point, the malware would not simply stop the reactor working — it would trigger a Chernobyl-type nuclear meltdown.
Why would the attackers want to precipitate such a catastrophic event?
- In the hope that such an “accident” would make the Iranian government look unfit to safely operate any kind of nuclear program.
- To undermine Iranian domestic support for the program.
- To alienate Iran from its Gulf neighbors who would be exposed to the fallout.
When John Bolton was last month melodramatically counting the days left for Israel to launch a missile strike on Bushehr, it was ostensibly because once the plant was fueled the Israelis would no longer be willing to risk the lives of so many in the region. With Gulf shipping lanes also closed down for an indeterminate period after an Israeli strike, the global economic impact would be severe.
On the other hand, in the event that Israel struck but did not fire a single missile and could not be shown to be responsible, the results of its own cost-benefit analysis — vastly different from that of the US — might make a devastating cyber attack on Bushehr seem well worth the risk.
In an analysis of Israel’s expanding cyberwarfare capabilities, Scott Borg, director of the US Cyber Consequences Unit, which advises various Washington agencies on cyber security, told Reuters last year that an Israeli attack on an Iranian nuclear facility could employ “malware loitering unseen and awaiting an external trigger, or pre-set to strike automatically when the infected facility reaches a more critical level of activity.”
The decision by Iranian authorities to announce that they have an ongoing investigation on how to thwart Stuxnet, suggests that they may now also be reassessing the risks of bringing Bushehr online as a fully operational facility.
Postscript: Even though discussion on the whole subject of Stuxnet’s purpose and origin is at this point highly speculative, some readers may view my suggestion that the goal is to cause a Chernobyl-type disaster to be a particularly wild conjecture. Maybe it is, but here’s a little more of my thinking on why that would be a plausible objective.
There is little reason to doubt that Israeli leaders from across the political spectrum are serious in their stated objections to Iran’s nuclear program. (Whether those objections correspond with Iran’s genuine nuclear ambitions is another question, as is the question of whether a nuclear-armed Iran would actually pose an existential threat to Israel.)
Among analysts inside and outside Israel there is a broad consensus that military action aimed at crippling Iran’s nuclear facilities would accomplish no more than cause a setback of a few years in the program. The same applies to sabotage.
Given the broad national support the nuclear program has, there is also reason to doubt that regime change would necessarily result in Iran’s enrichment program being scrapped.
What those who fear a nuclear-armed Iran hope to see is a credible political shift as a result of which Iran’s nuclear intentions are no longer in doubt and are demonstrably peaceful. (Which is to say, an ideal end-state similar to the one adopted by South Africa when it chose to abandon nuclear weapons — an ironic comparison of course, given that it was Israel that helped South Africa become a nuclear-armed state.)
For that reason, coercion (through sanctions) and military force are both potentially counterproductive in that pressure generally produces resistance.
On the other hand, the desired outcome might be reached if the Iranians through their own volition came to the conclusion that the costs of nuclear development outweighed the benefits. A catastrophic “accident” might be instrumental in bringing about a change of perspective through which for Iran as a nation, nuclear power lost most of its appeal.
Needless to say, if such an accident was exposed to be the result of an Israeli cyber attack, the plan would dangerously backfire.
Do intelligence agencies come up with such reckless plans? All the time.
Inveterate gamers will no doubt see another possibility here — that Stuxnet is part of a psy-ops plan designed to provoke a greater fear of catastrophic damage than it can actually cause. Possibly, but to identify and then exploit four Windows vulnerabilities suggests that the creators of this malware were willing to employ every possible resource at their disposal. In other words, they were seriously intent on doing damage — not just provoking fear.



Re: “In this scenario, Stuxnet would not be designed to perform its function until the reactor becomes fully operational. At that point, the malware would not simply stop the reactor working — it would trigger a Chernobyl-type nuclear meltdown. ” – Woodward
MY COMMENT: Has the anointed prophet, John Hagee, predicted something like this based upon his “interpretations” of the scripture? “Enqiring minds want to know?” Of course, I imagine the Israelis are smart enough not to have clued a ‘loose cannon’ like him in on the Stuxnet project.
FROM THE JERUSALEM POST, 03/09/10: …the San Antonio, Texas-based Hagee also warned the crowd about the threat of a nuclear Iran and labeled that country’s president, Mahmoud Ahmadinejad, the “Hitler of the Middle East.”
SOURCE – http://www.jpost.com/IranianThreat/News/Article.aspx?id=170528
They say that in a fight, never throw your knife at the opponent . If the throw does not stop them, you have just armed your enemy. Whoever created this malware has just given our enemies a template for attacking our infrastructure. This is VERY serious, they can learn things from this software they could never have learned on their own. They have the knife now, too bad.
let’s not candy coat this
-it is an act of war-
do we need some
updated geneva
conventions ?
The main problem with cyber-warfare as I see it is that in such a case like this even the best virus’s can be removed. Siemens has already found a way to remove two of the components and will likely have the other two closed off within a few days.
At the end of the day even a hugely complex virus like this one has coding with can be looked at to see how it operates and what it does. Thus why the German analysts have been able to just look at its source code to find out how to stop it.
Another problem with cyber warfare is that they needed to use a USB stick to infect the system. So there is still a human component. Likely once Bushehr is fully operational and there is not Russian IT guys and construction workers all around the site will become a lot harder to infiltrate with a USB containing a virus.
I’m guessing this is probably, as said, another part of the psy-ops against Iran. Could be the makers knew the chances were it would be removed by Siemens or Iran’s IT ministry and just did it to further terrorise/threaten the country.
One invariably wonders if the biggest “capture” of Israel is not Iran’s software by America’s democracy and rule of laws, not men. A reactive 9/11 attack against America because of our behaving on Israel’s behalf as “the far enemy” to Jihadis which opened the floodgates and let to our exsanguination in war on Iraq and now near war on Iran. All this was run by a Pentagon gone rogue with neocon cover against any President Bush interference. We are at a crossroad where America’s survival is at stake and the “worm” that put us there is Israel…Israel’s “worm” is not meant just to screw-up Iran’s nuclear plants but as just another step in attempted domination of the United States. We are now a nation at risk and Israel&neocons are holding the smoking gun. Far too many American Jews share this view for the standard “anti-Semite” slander to be applicable to me. And of course the Freudianism that American Jews are “self-hating Jews” lest they move to Israel is another of the psychotic turns the Middle East issue is taking. Meanwhile, China and Russia are watching and laughing. Will these people go so far as to push America into a Germany circa 1930s state in their short-sightedness, hoping that this will force American Jews to involuntarily in fear populate their ever expanding Israel?
CORRECTED
One invariably wonders if the biggest “capture” by Israel is not Iran’s software but America’s democracy and rule of laws, not men—both at risk since GW Bush began his “War on Terror.” A reactive 9/11 attack against America because of our behaving on Israel’s behalf as “the far enemy” to Jihadis which opened the floodgates and let to our exsanguination in war on Iraq and now near war on Iran. All this was run by a Pentagon gone rogue with neocon cover against any President Bush interference. We are at a crossroad where America’s survival is at stake and the “worm” that put us there is Israel…Israel’s “worm” is not meant just to screw-up Iran’s nuclear plants but as just another step in attempted domination of the United States. We are now a nation at risk and Israel&neocons are holding the smoking gun. Far too many American Jews share this view for the standard “anti-Semite” slander to be applicable to me. And of course the Freudianism that American Jews are “self-hating Jews” lest they move to Israel is another of the psychotic turns the Middle East issue is taking. Meanwhile, China and Russia are watching and laughing. Will these people go so far as to push America into a Germany circa 1930s state in their short-sightedness, hoping that this will force American Jews to involuntarily in fear populate their ever expanding Israel?
Very good information. Was happy you put up the Kaspersky information. This man from Bush Admin who also appears to be a co-worker of Chertoff: It is kind of strange because Chertoff and that whole crew of people are Israel supporters and firsters.
So why is he boldly insinuating it all onto Israel? People up on Israel and U.S. government should know by now that they are basically one and same. Or is something going on inside the U.S. government we are not aware of? Like maybe this group is splintering and siding up as the 9/11 issue continues to heat up and one can almost smell the fear in these people if the truth finally comes out?
Obama is clearly in the Israel camp (although it is growing apparent that he is being pulled by the more moderate people involved in the wars and Israel)…..
But I’ve noticed that the intelligence services (see Ray McGovern or Philip Giraldi…or even Veteranstoday.com) are coming out very Non-supportive of Israel more and more.
This is getting intriguing but also scary. As exposure to the filth and rot escalates we are all in more danger as the powerful elites are coming undone at the seams.
Also check out an interview from guns and butter about Cass Sunstein, Obama’s Internet Czar: Cass Sunstein’s Cognitive Infiltration
http://www.kpfa.org/archive/id/67100
that is another related issue to this growing cyber warfare game.