Here’s a telling insight into the operation of American intelligence.
How does the NSA spot a foreigner? It’s easy. Those are the people who use “foreign” languages.
The name X-Keyscore hadn’t appeared in the mainstream English-language media until today, but for Brazilians this news is close to a month old.
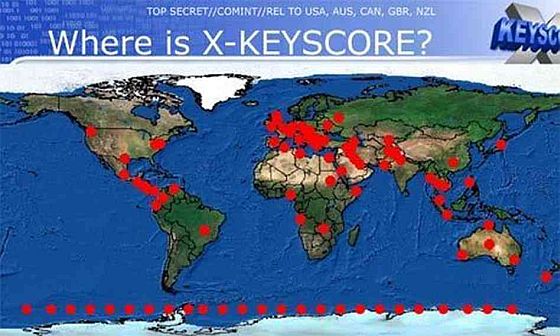
An article in Brazil’s O Globo newspaper published on July 9 co-authored by Glenn Greenwald included several of the X-Keyscore slides. A translation provided by Cryptome describing the slide (shown above) titled “Where is X-Keyscore?” says:
Map in 2008 shows Brazil among countries surveilled by the X-Keystore [sic] program, which details the presence of foreigners by the language used in emails and phone calls.
From this description it’s reasonable to deduce that the NSA — like many American bigots — figures it’s easy to identify foreigners, ’cos those are the folks that talk and write funny. And that probably explains why the NSA can boast no more than a 51 percent level of confidence in identifying their target’s “foreignness.”
The PowerPoint slides published today in The Guardian have been described as “training materials,” but I think Shane Harris’ description of this as a “marketing document” is closer the mark. In other words, this looks more like a presentation of a product’s claimed value as that would be promoted to a customer (such as the Department of Defense), rather than instructions on how to use the application.
A June 20 job posting by the major defense technology contractor SAIC for an “XKEYSCORE Systems Engineer” could indicate that SAIC itself created X-Keyscore and now provides its customers with support for its “fielded mission systems.”
Even if this application was created for the NSA, it appears to be accessible by multiple agencies and contractors.
CGI, a multinational information technology corporation which handles defense contracts for the U.S. Army, U.S. Navy and U.S. Marine Corps, has since July 19 been advertising a position for a Computer Network Operations (CNO) Analyst whose required skills include: “Familiarity using the following tools: Cadence, Surrey, TrafficThief, CNE Portal and X-Keyscore.” (If the name “TrafficThief” sounds familiar, that might be because it showed up on an earlier NSA slide: “PRISM Collection Dataflow.”)
Interestingly, such an analyst also requires: “Working knowledge of system and network exploitation, attack pathologies and intrusion techniques; denial of service attacks, man in the middle attacks, malicious code delivery techniques, fuzzing, automated network vulnerability and port scanning, botnets, password cracking, social engineering, network and system reconnaissance.”
This sounds like a position for an experienced hacker whose job is to defend the U.S. Army from other hackers. The analyst will: “Review threat data from various sources, including appropriate Intelligence databases, to establish the identity and modus operandi of hackers active in customer networks and posing potential threat to customer networks.” Accessing those appropriate intelligence databases presumably involves, among other things, the use of X-Keyscore.
That this is a widely used application is also evident from LinkedIn where numerous intelligence analysts proudly include use of X-Keyscore in their background experience:
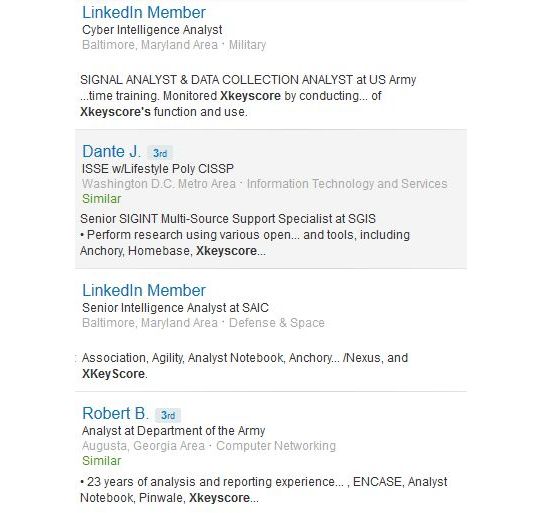
However secret the use of X-Keyscore might be, it’s certainly not so secret that anyone seems particularly nervous about mentioning its name.


Map in 2008 shows Brazil among countries surveilled by the X-Keystore [sic] program, which details the presence of foreigners by the language used in emails and phone calls.
“the N.S.A. has for years systematically tapped into the Brazilian telecommunications network and indiscriminately intercepted, collected and stored the mail and telephone records of millions of Brazilians.”
Brazilian- ‘O Globo’ article based on documents from Edward J. Snowden
Since 2008-hmmmm! thanks E.J.