Category Archives: Five Eyes
U.S. intelligence mining data from nine U.S. Internet companies in broad secret program
The Washington Post reports: The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio, video, photographs, e-mails, documents and connection logs that enable analysts to track a person’s movements and contacts over time.
The highly classified program, code-named PRISM, has not been disclosed publicly before. Its establishment in 2007 and six years of exponential growth took place beneath the surface of a roiling debate over the boundaries of surveillance and privacy. Even late last year, when critics of the foreign intelligence statute argued for changes, the only members of Congress who knew about PRISM were bound by oaths of office to hold their tongues.
An internal presentation on the Silicon Valley operation, intended for senior analysts in the NSA’s Signals Intelligence Directorate, described the new tool as the most prolific contributor to the President’s Daily Brief, which cited PRISM data in 1,477 articles last year. According to the briefing slides, obtained by The Washington Post, “NSA reporting increasingly relies on PRISM” as its leading source of raw material, accounting for nearly 1 in 7 intelligence reports.
That is a remarkable figure in an agency that measures annual intake in the trillions of communications. It is all the more striking because the NSA, whose lawful mission is foreign intelligence, is reaching deep inside the machinery of American companies that host hundreds of millions of American-held accounts on American soil.
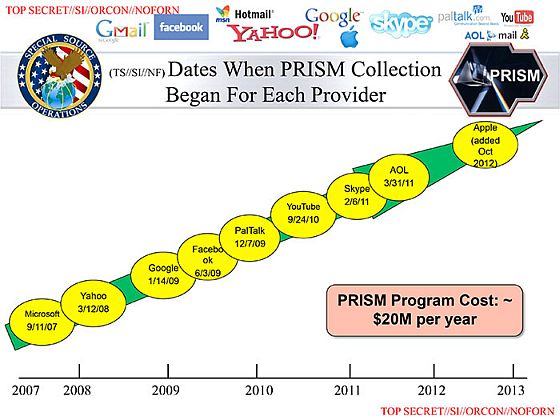
The technology companies, which participate knowingly in PRISM operations, include most of the dominant global players of Silicon Valley. They are listed on a roster that bears their logos in order of entry into the program: “Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.” PalTalk, although much smaller, has hosted significant traffic during the Arab Spring and in the ongoing Syrian civil war. [Continue reading…]
New York Times: The Obama ‘administration has now lost all credibility’
A New York Times editorial says: Within hours of the disclosure that the federal authorities routinely collect data on phone calls Americans make, regardless of whether they have any bearing on a counterterrorism investigation, the Obama administration issued the same platitude it has offered every time President Obama has been caught overreaching in the use of his powers: Terrorists are a real menace and you should just trust us to deal with them because we have internal mechanisms (that we are not going to tell you about) to make sure we do not violate your rights.
Those reassurances have never been persuasive — whether on secret warrants to scoop up a news agency’s phone records or secret orders to kill an American suspected of terrorism — especially coming from a president who once promised transparency and accountability.
The administration has now lost all credibility. Mr. Obama is proving the truism that the executive will use any power it is given and very likely abuse it. That is one reason we have long argued that the Patriot Act, enacted in the heat of fear after the 9/11 attacks by members of Congress who mostly had not even read it, was reckless in its assignment of unnecessary and overbroad surveillance powers. [Continue reading…]
Anger swells after NSA phone records collection revelations
The Guardian reports: The scale of America’s surveillance state was laid bare on Thursday as senior politicians revealed that the US counter-terrorism effort had swept up swaths of personal data from the phone calls of millions of citizens for years.
After the revelation by the Guardian of a sweeping secret court order that authorised the FBI to seize all call records from a subsidiary of Verizon, the Obama administration sought to defuse mounting anger over what critics described as the broadest surveillance ruling ever issued.
A White House spokesman said that laws governing such orders “are something that have been in place for a number of years now” and were vital for protecting national security. Dianne Feinstein, the Democratic chairwoman of the Senate intelligence committee, said the Verizon court order had been in place for seven years. “People want the homeland kept safe,” Feinstein said.
But as the implications of the blanket approval for obtaining phone data reverberated around Washington and beyond, anger grew among other politicians.
Intelligence committee member Mark Udall, who has previously warned in broad terms about the scale of government snooping, said: “This sort of widescale surveillance should concern all of us and is the kind of government overreach I’ve said Americans would find shocking.” Former vice-president Al Gore described the “secret blanket surveillance” as “obscenely outrageous”. [Continue reading…]
FBI places most Americans under surveillance
The National Security Agency at the request of the FBI is keeping a record of everywhere you go and everyone you talk to at all times.
Since, as The Guardian reports, the government is collecting this information from all Verizon customers, it’s reasonable to assume that it is also doing so with every other telecommunications carrier. In other words, there’s little doubt that every single individual in this country who uses any form of electronic communication is under 24-hour-a-day surveillance.
The White House is hiding behind the word “metadata” as it attempts to defend its actions — on the assumption that most people will overlook the loss of privacy if they believe that the content of their conversations is not being recorded.
In reality, metadata is the information that is of greatest interest to a security state. How so? Imagine the converse. Suppose the NSA was recording the content of all communications but not the metadata. Suppose it could only gain access to the metadata under a specific search warrant. The government would always know everything that was being said but have no idea who was talking to who. It couldn’t engage in data mining, constructing social networks and most of the other features of a mass surveillance enterprise. It couldn’t utterly abandon the principle that criminal investigation needs to be constrained by reasonable suspicion and probably cause.
People who think that screening procedures by TSA agents are unreasonably intrusive should be even more concerned about the handling of their metadata.
It’s not just metadata; it’s my data. And it’s turning into the equivalent of a citizens’ bar code used not only by governments but also corporations who understand that information is power and thus resist whatever constraints are imposed on their ability to gather personal information as extensively and in as great detail as they can.
The Guardian reports: The National Security Agency is currently collecting the telephone records of millions of US customers of Verizon, one of America’s largest telecoms providers, under a top secret court order issued in April.
The order, a copy of which has been obtained by the Guardian, requires Verizon on an “ongoing, daily basis” to give the NSA information on all telephone calls in its systems, both within the US and between the US and other countries.
The document shows for the first time that under the Obama administration the communication records of millions of US citizens are being collected indiscriminately and in bulk – regardless of whether they are suspected of any wrongdoing.
The secret Foreign Intelligence Surveillance Court (Fisa) granted the order to the FBI on April 25, giving the government unlimited authority to obtain the data for a specified three-month period ending on July 19.
Under the terms of the blanket order, the numbers of both parties on a call are handed over, as is location data, call duration, unique identifiers, and the time and duration of all calls. The contents of the conversation itself are not covered. [Continue reading…]
All telephone calls recorded and accessible to the U.S. government
Glenn Greenwald writes: The real capabilities and behavior of the US surveillance state are almost entirely unknown to the American public because, like most things of significance done by the US government, it operates behind an impenetrable wall of secrecy. But a seemingly spontaneous admission this week by a former FBI counterterrorism agent provides a rather startling acknowledgment of just how vast and invasive these surveillance activities are.
Over the past couple days, cable news tabloid shows such as CNN’s Out Front with Erin Burnett have been excitingly focused on the possible involvement in the Boston Marathon attack of Katherine Russell, the 24-year-old American widow of the deceased suspect, Tamerlan Tsarnaev. As part of their relentless stream of leaks uncritically disseminated by our Adversarial Press Corps, anonymous government officials are claiming that they are now focused on telephone calls between Russell and Tsarnaev that took place both before and after the attack to determine if she had prior knowledge of the plot or participated in any way.
On Wednesday night, Burnett interviewed Tim Clemente, a former FBI counterterrorism agent, about whether the FBI would be able to discover the contents of past telephone conversations between the two. He quite clearly insisted that they could: [Continue reading…]
Spying on America
Laura Poitras writes: It took me a few days to work up the nerve to phone William Binney. As someone already a “target” of the United States government, I found it difficult not to worry about the chain of unintended consequences I might unleash by calling Mr. Binney, a 32-year veteran of the National Security Agency turned whistle-blower. He picked up. I nervously explained I was a documentary filmmaker and wanted to speak to him. To my surprise he replied: “I’m tired of my government harassing me and violating the Constitution. Yes, I’ll talk to you.”
Two weeks later, driving past the headquarters of the N.S.A. in Maryland, outside Washington, Mr. Binney described details about Stellar Wind, the N.S.A.’s top-secret domestic spying program begun after 9/11, which was so controversial that it nearly caused top Justice Department officials to resign in protest, in 2004.
“The decision must have been made in September 2001,” Mr. Binney told me and the cinematographer Kirsten Johnson. “That’s when the equipment started coming in.” In this Op-Doc, Mr. Binney explains how the program he created for foreign intelligence gathering was turned inward on this country. He resigned over this in 2001 and began speaking out publicly in the last year. He is among a group of N.S.A. whistle-blowers, including Thomas A. Drake, who have each risked everything — their freedom, livelihoods and personal relationships — to warn Americans about the dangers of N.S.A. domestic spying.
To those who understand state surveillance as an abstraction, I will try to describe a little about how it has affected me. The United States apparently placed me on a “watch-list” in 2006 after I completed a film about the Iraq war. I have been detained at the border more than 40 times. Once, in 2011, when I was stopped at John F. Kennedy International Airport in New York and asserted my First Amendment right not to answer questions about my work, the border agent replied, “If you don’t answer our questions, we’ll find our answers on your electronics.”’ As a filmmaker and journalist entrusted to protect the people who share information with me, it is becoming increasingly difficult for me to work in the United States. Although I take every effort to secure my material, I know the N.S.A. has technical abilities that are nearly impossible to defend against if you are targeted. [Continue reading…]
The Surveillance State of America
Shane Harris writes: March 2002, John M. Poindexter, a former national security adviser to President Ronald Reagan, sat down with Gen. Michael V. Hayden, the director of the National Security Agency. Mr. Poindexter sketched out a new Pentagon program called Total Information Awareness, that proposed to scan the world’s electronic information — including phone calls, e-mails and financial and travel records — looking for transactions associated with terrorist plots. The N.S.A., the government’s chief eavesdropper, routinely collected and analyzed such signals, so Mr. Poindexter thought the agency was an obvious place to test his ideas.
He never had much of a chance. When T.I.A.’s existence became public, it was denounced as the height of post-9/11 excess and ridiculed for its creepy name. Mr. Poindexter’s notorious role in the Iran-contra affair became a central focus of the debate. He resigned from government, and T.I.A. was dismantled in 2003.
But what Mr. Poindexter didn’t know was that the N.S.A. was already pursuing its own version of the program, and on a scale that he had only imagined. A decade later, the legacy of T.I.A. is quietly thriving at the N.S.A. It is more pervasive than most people think, and it operates with little accountability or restraint.
The foundations of this surveillance apparatus were laid soon after 9/11, when President George W. Bush authorized the N.S.A. to monitor the communications records of Americans who analysts suspected had a “nexus to terrorism.” Acting on dubious legal authority, and without warrants, the N.S.A. began intercepting huge amounts of information.
But the N.S.A. came up with more dead ends than viable leads and put a premium on collecting information rather than making sense of it. The N.S.A. created what one senior Bush administration official later described as a “mirror” of AT&T’s databases, which allowed ready access to the personal communications moving over much of the country’s telecom infrastructure. The N.S.A. fed its bounty into software that created a dizzying social-network diagram of interconnected points and lines. The agency’s software geeks called it “the BAG,” which stood for “big ass graph.”
Today, this global surveillance system continues to grow. It now collects so much digital detritus — e-mails, calls, text messages, cellphone location data and a catalog of computer viruses — that the N.S.A. is building a 1-million-square-foot facility in the Utah desert to store and process it. [Continue reading…]
Former NSA official disputes claims by NSA chief
Wired reports: A former NSA official has accused the NSA’s director of deception during a speech he gave at the DefCon hacker conference on Friday when he asserted that the agency does not collect files on Americans.
William Binney, a former technical director at the NSA, said during a panel discussion that NSA Director Gen. Keith Alexander was playing a “word game” and that the NSA was indeed collecting e-mails, Twitter writings, internet searches and other data belonging to Americans and indexing it.
“Unfortunately, once the software takes in data, it will build profiles on everyone in that data,” he said. “You can simply call it up by the attributes of anyone you want and it’s in place for people to look at.”
He said the NSA began building its data collection system to spy on Americans prior to 9/11, and then used the terrorist attacks that occurred that year as the excuse to launch the data collection project.
“It started in February 2001 when they started asking telecoms for data,” Binney said. “That to me tells me that the real plan was to spy on Americans from the beginning.”
Binney is referring to assertions that former Qwest CEO James Nacchio made in court documents in 2007 that the NSA had asked Qwest, AT&T, Verizon and Bellsouth in early 2001 for customer calling records and that all of the other companies complied with the request, but Nacchio declined to participate until served with a proper legal order.
“The reason I left the NSA was because they started spying on everybody in the country. That’s the reason I left,” said Binney, who resigned from the agency in late 2001. [Continue reading…]
NSA: It would violate your privacy to say if we spied on you
Danger Room reports: The surveillance experts at the National Security Agency won’t tell two powerful United States Senators how many Americans have had their communications picked up by the agency as part of its sweeping new counterterrorism powers. The reason: it would violate your privacy to say so.
That claim comes in a short letter sent Monday to civil libertarian Senators Ron Wyden and Mark Udall. The two members of the Senate’s intelligence oversight committee asked the NSA a simple question last month: under the broad powers granted in 2008′s expansion of the Foreign Intelligence Surveillance Act, how many persons inside the United States have been spied upon by the NSA?
The query bounced around the intelligence bureaucracy until it reached I. Charles McCullough, the Inspector General of the Office of the Director of National Intelligence, the nominal head of the 16 U.S. spy agencies. In a letter acquired by Danger Room, McCullough told the senators that the NSA inspector general “and NSA leadership agreed that an IG review of the sort suggested would itself violate the privacy of U.S. persons,” McCullough wrote.
“All that Senator Udall and I are asking for is a ballpark estimate of how many Americans have been monitored under this law, and it is disappointing that the Inspectors General cannot provide it,” Wyden told Danger Room on Monday. “If no one will even estimate how many Americans have had their communications collected under this law then it is all the more important that Congress act to close the ‘back door searches’ loophole, to keep the government from searching for Americans’ phone calls and emails without a warrant.”
What’s more, McCullough argued, giving such a figure of how many Americans were spied on was “beyond the capacity” of the NSA’s in-house watchdog — and to rectify it would require “imped[ing]” the very spy missions that concern Wyden and Udall. “I defer to [the NSA inspector general’s] conclusion that obtaining such an estimate was beyond the capacity of his office and dedicating sufficient additional resources would likely impede the NSA’s mission,” McCullough wrote. [Continue reading…]
Google pretends to warn Gmail users about state-sponsored email hacking
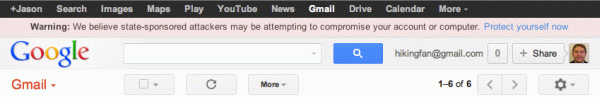
CNET reports: Google hasn’t been shy about wagging its finger at China recently. And in what appears to be another veiled snipe at Chinese authorities, the tech company says it is now warning users if state-sponsored phishing or malware attacks appear to have targeted their Gmail accounts.
“We are constantly on the lookout for malicious activity on our systems, in particular attempts by third parties to log into users’ accounts unauthorized,” Eric Grosse, vice president of security engineering at Google, wrote in a blog post today. “When we have specific intelligence — either directly from users or from our own monitoring efforts — we show clear warning signs and put in place extra roadblocks to thwart these bad actors.”
In such cases, a notice will appear at the top of the Gmail page that says “Warning: We believe state-sponsored attackers may be attempting to compromise your account or computer.”
If that warning appears, it doesn’t mean the account was successfully hijacked. It just means that the account appears to have been a target, and that Google is urging the account holder to change the password and set up additional security precautions.
Most people who use Google are confused about what Google is — they think it’s a search engine. It’s not. It’s a digital platform that connects advertisers to consumers. Access to consumers is the ‘product’ that Google sells. So when the company introduces a new security feature such as this new hacking warning, we should keep in mind that rather than this simply being some public spirited effort to protect the interests of Google’s users, more likely it’s also been conceived as a gambit intended to serve Google’s commercial interests. It will serve those interests by fostering a sense among users and potential users, that gmail is more secure than it probably is.
If, as will be the case for the vast majority of people who check their gmail accounts, no warning message appears about state-sponsored hacking, does that imply that ones account is secure? I don’t think so. It might not currently be subject to phishing or malware attacks from the Chinese or any other foreign government, but does that also mean that the prying eyes of the NSA are being kept out? Not according to NSA whistleblower William Binney.
NSA unchained (infographic)
ACLU: In November 2001, the National Security Agency began illegally intercepting Americans’ phone calls and emails without warrants or suspicion of wrongdoing. In 2008, Congress amended the Foreign Intelligence Surveillance Act (FISA), rubber-stamping this warrantless wiretapping program and giving the NSA power to conduct dragnet surveillance of Americans’ international communications. Continue reading
Video: NSA whistleblower interview — part two
(See part one here.)
Videos: Obama’s state surveillance system
National Security Agency whistleblower William Binney reveals he believes domestic surveillance has become more expansive under President Obama than President George W. Bush. He estimates the NSA has assembled 20 trillion “transactions” — phone calls, emails and other forms of data — from Americans.
Jacob Appelbaum, a computer researcher who has faced a stream of interrogations and electronic surveillance since he volunteered with the whistleblowing website, WikiLeaks, describes being detained more than a dozen times at the airport and interrogated by federal agents who asked about his political views and confiscated his cell phone and laptop.
Shady companies with ties to Israel wiretap the U.S. for the NSA
James Bamford writes: Army General Keith Alexander, the director of the NSA, is having a busy year — hopping around the country, cutting ribbons at secret bases and bringing to life the agency’s greatly expanded eavesdropping network.
In January he dedicated the new $358 million CAPT Joseph J. Rochefort Building at NSA Hawaii, and in March he unveiled the 604,000-square-foot John Whitelaw Building at NSA Georgia.
Designed to house about 4,000 earphone-clad intercept operators, analysts and other specialists, many of them employed by private contractors, it will have a 2,800-square-foot fitness center open 24/7, 47 conference rooms and VTCs, and “22 caves,” according to an NSA brochure from the event. No television news cameras were allowed within two miles of the ceremony.
Overseas, Menwith Hill, the NSA’s giant satellite listening post in Yorkshire, England that sports 33 giant dome-covered eavesdropping dishes, is also undergoing a multi-million-dollar expansion, with $68 million alone being spent on a generator plant to provide power for new supercomputers. And the number of people employed on the base, many of them employees of Lockheed Martin and Northrop Grumman, is due to increase from 1,800 to 2,500 in 2015, according to a study done in Britain. Closer to home, in May, Fort Meade will close its 27-hole golf course to make room for a massive $2 billion, 1.8-million-square-foot expansion of the NSA’s headquarters, including a cybercommand complex and a new supercomputer center expected to cost nearly $1 billion.
The climax, however, will be the opening next year of the NSA’s mammoth 1-million-square-foot, $2 billion Utah Data Center. The centerpiece in the agency’s decade-long building boom, it will be the “cloud” where the trillions of millions of intercepted phone calls, e-mails, and data trails will reside, to be scrutinized by distant analysts over highly encrypted fiber-optic links.
Despite the post-9/11 warrantless wiretapping of Americans, the NSA says that citizens should trust it not to abuse its growing power and that it takes the Constitution and the nation’s privacy laws seriously.
But one of the agency’s biggest secrets is just how careless it is with that ocean of very private and very personal communications, much of it to and from Americans. Increasingly, obscure and questionable contractors — not government employees — install the taps, run the agency’s eavesdropping infrastructure, and do the listening and analysis.
And with some of the key companies building the U.S.’s surveillance infrastructure for the digital age employing unstable employees, crooked executives, and having troubling ties to foreign intelligence services, it’s not clear that Americans should trust the secretive agency, even if its current agency chief claims he doesn’t approve of extrajudicial spying on Americans. His predecessor, General Michael V. Hayden, made similar claims while secretly conducting the warrantless wiretapping program.
Until now, the actual mechanics of how the agency constructed its highly secret U.S. eavesdropping net, code-named Stellar Wind, has never been revealed. But in the weeks following 9/11, as the agency and the White House agreed to secretly ignore U.S. privacy laws and bypass the Foreign Intelligence Surveillance Court, J. Kirk Wiebe noticed something odd. A senior analyst, he was serving as chief of staff for the agency’s Signals Intelligence Automation Research Center (SARC), a sort of skunkworks within the agency where bureaucratic rules were broken, red tape was cut, and innovation was expected.
“One day I notice out in the hallway, stacks and stacks of new servers in boxes just lined up,” he said.
Passing by the piles of new Dell 1750 servers, Wiebe, as he often did, headed for the Situation Room, which dealt with threat warnings. It was located within the SARC’s Lab, on the third floor of Operations Building 2B, a few floors directly below the director’s office. “I walk in and I almost get thrown out by a guy that we knew named Ben Gunn,” he said. It was the launch of Stellar Wind and only a handful of agency officials were let in on the secret.
“He was the one who organized it,” said Bill Binney of Gunn. A former founder and co-director of SARC, Binney was the agency official responsible for automating much of the NSA’s worldwide monitoring networks. Troubled by the unconstitutional nature of tapping into the vast domestic communications system without a warrant, he decided to quit the agency in late 2001 after nearly forty years.
Gunn, said Binney, was a Scotsman and naturalized U.S. citizen who had formerly worked for GCHQ, Britain’s equivalent of the NSA, and later become a senior analyst at the NSA. The NSA declined Wired’s request to interview Gunn, saying that, as policy, it doesn’t confirm or deny if a person is employed by the agency.
Shortly after the secret meeting, the racks of Dell servers were moved to a room down the hall, behind a door with a red seal indicating only those specially cleared for the highly compartmented project could enter. But rather than having NSA employees putting the hardware and software together and setting up walls of monitors showing suspected terrorism threats and their U.S. communications, the spying room was filled with a half-dozen employees of a tiny mom-and-pop company with a bizarre and troubling history.
“It was Technology Development Corporation,” said Binney.
The agency went to TDC, he says, because the company had helped him set up a similar network in SARC — albeit one that was focused on foreign and international communications — the kind of spying the NSA is chartered to undertake.
“They needed to have somebody who knew how the code works to set it up,” he said. “And then it was just a matter of feeding in the attributes [U.S. phone numbers, e-mail addresses and personal data] and any of the content you want.” Those “attributes” came from secret rooms established in large telecom switches around the country. “I think there’s 10 to 20 of them,” Binney says.
Formed in April 1984, TDC was owned by two brothers, Randall and Paul Jacobson, and largely run out of Randall’s Clarkesville, Maryland house, with his wife acting as bookkeeper. But its listed address is a post office box in Annapolis Junction, across the Baltimore-Washington Parkway from the NSA, and the company’s phone number in various business directories is actually an NSA number in Binney’s old office.
The company’s troubles began in June 1992 when Paul lost his security clearance. “If you ever met this guy, you would know he’s a really strange guy,” Binney said of Paul. “He did crazy stuff. I think they thought he was unstable.” At the time, Paul was working on a contract at the NSA alongside a rival contractor, Unisys Corporation. He later blamed Unisys for his security problems and sued it, claiming that Unisys employees complained about him to his NSA supervisors. According to the suit, Unisys employees referred to him as “weird” and that he “acted like a robot,” “never wore decent clothes,” and was mentally and emotionally unstable. About that time, he also began changing his name, first to Jimmy Carter, and later to Alfred Olympus von Ronsdorf.
With “von Ronsdorf’s” clearance gone and no longer able to work at the NSA, Randy Jacobson ran the company alone, though he kept his brother and fellow shareholder employed in the company, which led to additional problems.
“What happened was Randy still let him have access to the funds of the company and he squandered them,” according to Binney. “It was so bad, Randy couldn’t pay the people who were working for him.” According to court records, Ronsdorf allegedly withdrew about $100,000 in unauthorized payments. But Jacobson had troubles of his own, having failed to file any income tax statements for three years in the 1990s, according to tax court records. Then in March 2002, around the time the company was completing Stellar Wind, Jacobson fired his brother for improper billing and conversion of company funds. That led to years of suits and countersuits over mismanagement and company ownership.
Despite that drama, Jacobson and his people appeared to have serious misgivings about the NSA’s program once they discovered its true nature, according to Binney. “They came and said, ‘Do you realize what these people are doing?’” he said. “‘They’re feeding us other stuff [U.S.] in there.’ I mean they knew it was unconstitutional right away.” Binney added that once the job was finished, the NSA turned to still another contractor to run the tapping operation. “They made it pretty well known, so after they got it up and running they [the NSA] brought in the SAIC people to run it after that.” Jacobsen was then shifted to other work at the NSA, where he and his company are still employed.
Randall Jacobsen answered his phone inside the NSA but asked for time to respond. He never called back.
In addition to constructing the Stellar Wind center, and then running the operation, secretive contractors with questionable histories and little oversight were also used to do the actual bugging of the entire U.S. telecommunications network.
According to a former Verizon employee briefed on the program, Verint, owned by Comverse Technology, taps the communication lines at Verizon, which I first reported in my book The Shadow Factory in 2008. Verint did not return a call seeking comment, while Verizon said it does not comment on such matters.
At AT&T the wiretapping rooms are powered by software and hardware from Narus, now owned by Boeing, a discovery made by AT&T whistleblower Mark Klein in 2004. Narus did not return a call seeking comment.
What is especially troubling is that both companies have had extensive ties to Israel, as well as links to that country’s intelligence service, a country with a long and aggressive history of spying on the U.S. [Continue reading…]
NSA chief denies domestic spying but whistleblowers say otherwise
James Bamford writes: In a rare break from the NSA’s tradition of listening but not speaking, NSA chief General Keith Alexander was grilled Tuesday on the topic of eavesdropping on Americans in front of a House subcommittee.
The questioning from Rep. Hank Johnson (D-Georgia) was prompted by Wired’s cover story this month on the NSA’s growing reach and capabilities, but leaves Americans with as many questions about the reach of spy agency’s powers as they had before Alexander spoke.
Alexander denied, in carefully parsed words, that the NSA has the power to monitor Americans’ communications without getting a court warrant.
But Alexander’s comments fly in the face of people who actually helped create the agency’s eavesdropping and data mining infrastructure. Few people know that system as well as William Binney, who served as the technical director for the agency’s M Group, which stood for World Geopolitical Military Analysis and Reporting, the giant 6,000-person organization responsible for eavesdropping on most of the world.
He was also the founder and co-director of the agency’s Signals Intelligence Automation Research Center, which helped automate that eavesdropping network. Binney decided to leave after a long career rather than be involved in the agency warrantless eavesdropping program, a program he said involves secret monitoring facilities in ten to twenty large telecom switches around the country, such as the one discovered in San Francisco’s AT&T installation a few years ago.
Historically, the NSA’s initial response has always been to either deny or evade when confronted with issues involving eavesdropping on Americans. For decades the agency secretly hid from Congress the fact that it was copying, without a warrant, virtually every telegram traveling through the United States, a program known as Project Shamrock. Then it hid from Congress the fact that it was illegally targeting the phone calls of anti-war protesters during the Vietnam War, known as Project Minaret.
More recently, President Bush said falsely that no American had been wiretapped without a warrant at the same time the agency was eavesdropping on thousands of Americans without a warrant as part of the later revealed Operation Stellar Wind. The Congress then passed a bill granting immunity from prosecution and law suits to the telecom companies involved in the illegal program.
Also, in the same way that General Alexander carefully parsed his words, the agency has always maintained its own secret definition of words in a document known as United States Signals Intelligence Directive 18, a document classified above top secret.
For example, NSA can intercept millions of domestic communications and store them in a data center like Bluffdale and still be able to say it has not “intercepted” any domestic communications. This is because of its definition of the word. “Intercept,” in NSA’s lexicon, only takes place when the communications are “processed” “into an intelligible form intended for human inspection,” not as they pass through NSA listening posts and transferred to data warehouses. [Continue reading…]
The NSA is building the country’s biggest spy center targeting all communication everywhere
James Bamford writes: Under construction by contractors with top-secret clearances, the blandly named Utah Data Center is being built for the National Security Agency. A project of immense secrecy, it is the final piece in a complex puzzle assembled over the past decade. Its purpose: to intercept, decipher, analyze, and store vast swaths of the world’s communications as they zap down from satellites and zip through the underground and undersea cables of international, foreign, and domestic networks. The heavily fortified $2 billion center should be up and running in September 2013. Flowing through its servers and routers and stored in near-bottomless databases will be all forms of communication, including the complete contents of private emails, cell phone calls, and Google searches, as well as all sorts of personal data trails—parking receipts, travel itineraries, bookstore purchases, and other digital “pocket litter.” It is, in some measure, the realization of the “total information awareness” program created during the first term of the Bush administration—an effort that was killed by Congress in 2003 after it caused an outcry over its potential for invading Americans’ privacy.
But “this is more than just a data center,” says one senior intelligence official who until recently was involved with the program. The mammoth Bluffdale center will have another important and far more secret role that until now has gone unrevealed. It is also critical, he says, for breaking codes. And code-breaking is crucial, because much of the data that the center will handle—financial information, stock transactions, business deals, foreign military and diplomatic secrets, legal documents, confidential personal communications—will be heavily encrypted. According to another top official also involved with the program, the NSA made an enormous breakthrough several years ago in its ability to cryptanalyze, or break, unfathomably complex encryption systems employed by not only governments around the world but also many average computer users in the US. The upshot, according to this official: “Everybody’s a target; everybody with communication is a target.”
For the NSA, overflowing with tens of billions of dollars in post-9/11 budget awards, the cryptanalysis breakthrough came at a time of explosive growth, in size as well as in power. Established as an arm of the Department of Defense following Pearl Harbor, with the primary purpose of preventing another surprise assault, the NSA suffered a series of humiliations in the post-Cold War years. Caught offguard by an escalating series of terrorist attacks—the first World Trade Center bombing, the blowing up of US embassies in East Africa, the attack on the USS Cole in Yemen, and finally the devastation of 9/11—some began questioning the agency’s very reason for being. In response, the NSA has quietly been reborn. And while there is little indication that its actual effectiveness has improved—after all, despite numerous pieces of evidence and intelligence-gathering opportunities, it missed the near-disastrous attempted attacks by the underwear bomber on a flight to Detroit in 2009 and by the car bomber in Times Square in 2010—there is no doubt that it has transformed itself into the largest, most covert, and potentially most intrusive intelligence agency ever created.
In the process—and for the first time since Watergate and the other scandals of the Nixon administration—the NSA has turned its surveillance apparatus on the US and its citizens. It has established listening posts throughout the nation to collect and sift through billions of email messages and phone calls, whether they originate within the country or overseas. It has created a supercomputer of almost unimaginable speed to look for patterns and unscramble codes. Finally, the agency has begun building a place to store all the trillions of words and thoughts and whispers captured in its electronic net. And, of course, it’s all being done in secret. To those on the inside, the old adage that NSA stands for Never Say Anything applies more than ever. [Continue reading…]
9/11: the tapping point
David Rose writes: One morning in June 2001, three months before the 9/11 attacks on the United States, I happened to be interviewing a senior official from the British Secret Intelligence Service, M.I.6. His current focus was the war on drugs, not international terrorism, but he shared a piece of information that united the two subjects.
A short time earlier, the official told me, the U.S. National Security Agency had intercepted a call between two satellite-telephone users in Afghanistan—the al-Qaeda leader Osama bin Laden and the Taliban leader Mullah Mohammed Omar. They had been discussing the Taliban’s ban on growing opium poppies, imposed the previous summer—a remarkably effective edict that had shrunk production in areas they controlled almost to zero.
According to the M.I.6 official, bin Laden sounded unhappy. “Why stop growing opium?” he asked. “Heroin only weakens our enemies.” There was no need to worry, Mullah Omar replied. The ban was merely a tactic. “There has been a glut, and the price is too low. Once the world price has risen, the farmers can start growing it again.”
The real lesson of this overheard conversation was not its specific content but the fact that it could be heard at all. Electronic eavesdropping clearly had potential in Taliban-controlled Afghanistan. But in the years before 9/11, when bin Laden’s terror plot was first being discussed, that potential remained limited. The reason was simple: Afghanistan had no cell phones, no Internet, and only a rudimentary landline network, which did not work at all outside the country’s largest cities. This could be remedied, however. Indeed, by the end of 1999, the Taliban government had embraced a full-fledged American scheme to install a modern cell-phone-and-Internet system in Afghanistan. It could have been up and running within months. The Taliban had already granted an exclusive license to a U.S.-owned firm, the Afghan Wireless Communications Company.
More to the point, electronic modifications concealed within the circuitry would have allowed every call and every e-mail emanating from Afghanistan to be relayed without interference to N.S.A. headquarters in Fort Meade, Maryland. “This project was a dream,” says one former senior F.B.I. counterterrorism specialist who knew about the scheme at the time. “To be able to wire up a country from ground level up—you don’t get too many opportunities like that.” No, you don’t. But at the critical moment, the Clinton administration put the project on hold, while rival U.S. agencies—the F.B.I., the N.S.A., and the C.I.A.—bickered over who should control it.
In the decade since 9/11, investigations by journalists and government commissions have explored the many missed opportunities to prevent bin Laden’s attacks. Overall, it is the story of a catastrophic failure to connect the dots. One can argue—and many have—that the connections emerge more visibly in retrospect than they ever did as events themselves unfolded. But the affair of the Afghan cell-phone network—put on hold until time ran out—falls into a category by itself. It was a course of action whose value and urgency were acknowledged by everyone, but it was impeded nonetheless. The cell-phone plan “was one tool we could have put in Afghanistan that could have made a difference,” a former C.I.A. official says. “Why didn’t we put it in? Because we couldn’t fucking agree.”