The Washington Post reports: Early last August, an envelope with extraordinary handling restrictions arrived at the White House. Sent by courier from the CIA, it carried “eyes only” instructions that its contents be shown to just four people: President Barack Obama and three senior aides.
Inside was an intelligence bombshell, a report drawn from sourcing deep inside the Russian government that detailed Russian President Vladimir Putin’s direct involvement in a cyber campaign to disrupt and discredit the U.S. presidential race.
But it went further. The intelligence captured Putin’s specific instructions on the operation’s audacious objectives — defeat or at least damage the Democratic nominee, Hillary Clinton, and help elect her opponent, Donald Trump.
At that point, the outlines of the Russian assault on the U.S. election were increasingly apparent. Hackers with ties to Russian intelligence services had been rummaging through Democratic Party computer networks, as well as some Republican systems, for more than a year. In July, the FBI had opened an investigation of contacts between Russian officials and Trump associates. And on July 22, nearly 20,000 emails stolen from the Democratic National Committee were dumped online by WikiLeaks. [Continue reading…]
Category Archives: WikiLeaks
We’re Seth Rich’s parents. Stop politicizing our son’s murder
Mary Rich and Joel Rich write: Imagine living in a nightmare that you can never wake up from. Imagine having to face every single day knowing that your son was murdered. Imagine you have no answers — that no one has been brought to justice and there are few clues leading to the killer or killers. Imagine that every single day, with every phone call you hope that it’s the police, calling to tell you that there has been a break in the case.
Imagine that instead, every call that comes in is a reporter asking what you think of a series of lies or conspiracies about the death. That nightmare is what our family goes through every day.
Our beloved son Seth Rich was gunned down in the early hours of July 10, 2016, in his Washington, D.C., neighborhood of Bloomingdale. On the day he was murdered, Seth was excited about a new job he had been offered on Hillary Clinton’s presidential campaign.
Seth had dedicated his life to public service, and he told us that he wanted to work on the campaign’s effort to expand voter participation because he loved our country dearly and believed deeply in the promise of democratic engagement. Seth had been walking around, calling friends, family and his girlfriend, pondering the broader picture of what the job change would mean. He wondered how he would pick up and move to New York City for four months, the strain that might put on his relationships, and how it would all affect the life he had built for himself in Washington.
The circumstances of what happened next are still unclear. We know that Seth was abruptly confronted on the street, that he had been on the phone and quickly ended the call. We also know that there were signs of a struggle, including a watchband torn when the assailants attempted to rip it off his wrist. Law-enforcement officials told us that Seth’s murder looked like a botched robbery attempt in which the assailants — after shooting our son — panicked, immediately ran and abandoned Seth’s personal belongings. We have seen no evidence, by any person at any time, that Seth’s murder had any connection to his job at the Democratic National Committee or his life in politics. Anyone who claims to have such evidence is either concealing it from us or lying.
Still, conservative news outlets and commentators continue, day after painful day, to peddle discredited conspiracy theories that Seth was killed after having provided WikiLeaks with emails from the DNC. Those theories, which some reporters have since retracted, are baseless, and they are unspeakably cruel.
We know that Seth’s personal email and his personal computer were both inspected by detectives early in the investigation and that the inspection revealed no evidence of any communications with anyone at WikiLeaks or anyone associated with WikiLeaks. Nor did that inspection reveal any evidence that Seth had leaked DNC emails to WikiLeaks or to anyone else. Indeed, those who have suggested that Seth’s role as a data analyst at the DNC gave him access to a wide trove of emails are simply incorrect — Seth’s job was to develop analytical models to encourage voters to turn out to vote. He didn’t have access to DNC emails, Democratic Congressional Campaign Committee emails, John Podesta’s emails or Hillary Clinton’s emails. That simply wasn’t his job. [Continue reading…]
Wikileaks: Inside the Farage-Assange-Trump connection
The Daily Beast reports: When Julian Assange sought refuge in 2011 at an embassy in the heart of London, only one of Britain’s political parties was willing to offer support to the exile in their midst.
Nigel Farage’s U.K. Independence Party, which seemed a fringe movement at the time but became the driving force behind Brexit, swung into action and campaigned against the demand that Assange be returned to Sweden for a police interview on allegations of rape.
Farage and his UKIP colleagues have spoken out publicly in support of Assange numerous times since 2011, but leaked emails seen by The Daily Beast reveal the true extent to which the party apparatus tried to assist the founder of WikiLeaks, which the head of the CIA has since described as a “hostile intelligence service” that cooperated with Russian agents.
The episode raises further questions about links between Farage, Assange and the Russian government. Farage, who is also a favored friend of U.S. President Donald Trump, was spotted emerging from a meeting with Assange at the Ecuadorian embassy in March. [Continue reading…]
The clever timing of the Macron data dump
An election whose outcome is widely perceived as a foregone conclusion, is an election sure to be met with widespread voter apathy. Combine that with the fact that many French voters have almost equal distaste for both candidates in Sunday’s election and the assumption that its outcome is certain becomes much more questionable.
Wikileaks/Julian Assange, posturing as an impartial observer, was quick to promote the #MacronLeaks hashtag and to focus on the timing of the “leak.”
#MacronLeaks assessment update: This massive leak is too late to shift the election. The intent behind the timing is curious.
— WikiLeaks (@wikileaks) May 5, 2017
Who is most likely behind #MacronLeaks which have been timed such that they are very unlikely to affect the vote?
— WikiLeaks (@wikileaks) May 5, 2017
Who benefits? Timing of alleged dump is too late to hit vote but will surely be used to boost hostility to Russia & intelligence spending.
— WikiLeaks (@wikileaks) May 5, 2017
The Wikileaks/Russian narrative is clear: don’t be misled by reports that reveal Russian involvement in this “massive leak.” It’s timing makes it clear that this is the handiwork of naive hackers who “don’t get timing.”
A stronger argument can be made, however, that the timing of this data dump, far from being curious or naive, was strategically chosen to be of maximum effect and that its intended effect, more than anything else, was to taint the election outcome. This has less to do with determining who becomes France’s next president than it has with poisoning the democratic process.
Think about it: A leak worthy of that label is by its nature revelatory. It brings to light information that was up until that moment, guarded in secrecy. That secrecy had been maintained purposefully to prevent the damaging effects of revelation.
The Macron data dump, however, was identified by its size rather than its content. The shorter the interval between its release and election day, the less time there would be to highlight its vacuity.
Moreover, in terms of political effect, the act and event of digital leaking has in this cynical era generally taken on more significance as a form of political theater than as an instrument of truth telling.
The leak makes the target look vulnerable and poorly equipped to handle the levers of state in a age that requires data security.
The hacker, like the terrorist, “wins” for no other reason than the fact that he couldn’t be stopped.
The cleverness of timing this attack on the French election minutes before political campaigning was legally required to end, was that #MacronLeaks would then be able to play out most freely in social media while France’s mainstream media would remain largely silent.
The overarching strategy here is one we’ve seen before: it’s about fabricating something out of nothing in order to foment and sustain a visceral mistrust that is immune to reason.
This hacking will have worked, like many before and many more to come, not because it raised awareness but because it can serve as an instrument for steering popular sentiment.
This is hacking as a form of advertising and thus its purpose is less to change the way people think than the way they feel.
In order to achieve its maximum effect, as Dominic Cummings, who ran Britain’s Vote Leave campaign, has noted, the crucial element in advertising is timing:
One of the few reliable things we know about advertising amid the all-pervasive charlatanry is that, unsurprisingly, adverts are more effective the closer to the decision moment they hit the brain.
In France, as has happened elsewhere, the war against democracy will continue to progress with or without spectacular victories, as citizens lose faith and lose interest in actively sustaining freedoms they have long taken for granted. #MacronLeaks advances that process.
U.S. far-right activists promote hacking attack against Macron
The New York Times reports: After months of trying to move the political needle in favor of Marine Le Pen in the French presidential election, American far-right activists on Saturday threw their weight behind a hacking attack against her rival, Emmanuel Macron, hoping to cast doubt on an election that is pivotal to France and the wider world.
The efforts were the culmination of a monthslong campaign against Mr. Macron after his candidacy began to gain steam earlier this year, with digital activists in the United States and elsewhere regularly sharing tactics, tips and tricks across the English- and French-speaking parts of the internet.
It is unclear whether the leaked documents, which some experts say may be connected to hackers linked to Russia, will affect the outcome of the election on Sunday between Ms. Le Pen, the far-right candidate from the National Front and Mr. Macron, an independent centrist. But the role of American far-right groups in promoting the breach online highlights their growing resolve to spread extremist messages beyond the United States.
“It’s the anti-globalists trying to go global,” said Ben Nimmo, a senior fellow of the digital forensics research lab at the Atlantic Council, a think tank, who has studied the far right’s recent efforts against Mr. Macron and others in France. “There’s a feeling of trying to export the revolution.” [Continue reading…]
Alex Jones will never stop being Alex Jones
Charlie Warzel reports: Jones has today found a place in a United States he helped create, led by a president he helped push into office. From the beginning, Donald Trump was a human distillation of Jones’ anti-establishment, anti-globalist, pro-libertarian, massively paranoid worldview; Jones, meanwhile, was an enthusiastic messenger for Trump’s campaign. There was Trump’s appearance on Jones’ show, in which he praised the host’s reputation as “amazing”; Infowars’ “Hillary for Prison” T-shirts, ubiquitous at campaign rallies; Jones’ championing of WikiLeaks’s emails dump and his characterization of Hillary Clinton as, among other things, “a complete wanton power-tripping self-worshipping devil worshipper”; and finally, in the earliest hours of November 9, a tearful Jones outlining Trump’s plan to “build a better world” while clinking champagne glasses with Trump adviser Roger Stone and listening to Frank Sinatra’s “My Way.”
After 15 years of obscurity, Jones has the audience and the influence he always wanted. And yet he is, somehow, off his game. He spent the first 100 days of the Trump administration — what should have been the honeymoon period — apologizing for his role in promoting the “Pizzagate” conspiracy theory, retracting his claims to stave off legal action, and, perhaps most unexpectedly, trying to convince a jury that some of his most salacious on-air diatribes were really just “performance art” all along.
Jones, an unwavering professional conspiracy theorist, is being interrogated about his true beliefs just as his golden age of conspiracy is ascendant. But conversations with 25 people in Jones’ orbit indicate that his troubles don’t stem from a split between the character and the human, but from the fact that Jones is eminently and unquestionably himself at all times. Jones has been this way since he was brawling among parked cars. It’s made him a fortune, but now that his moment is finally here, it could be his undoing. [Continue reading…]
Is Julian Assange an idiot who has outlived his usefulness?
Michael Weiss writes: There is no one more zealous than a convert.
CIA Director Mike Pompeo previously welcomed WikiLeaks’ disclosures about Hillary Clinton and the Democratic National Committee when these proved helpful to the Republican nominee. Now he has experienced a road-to-Damascus moment.
“WikiLeaks,” Pompeo said at a think tank event last week, “walks like a hostile intelligence service and talks like a hostile intelligence service.” Pompeo also regards Julian Assange, the publisher of WikiLeaks and the lonely maintainer of its hyper-active Twitter account, as a “fraud.”
In a rather folksy fly-over metaphor, the former Kansas representative likened the albinoid antipodean anarchist to the Wizard of Oz, perhaps forgetting that the man behind the curtain turned out to be an all-right guy in the end rather than a helpmeet of European dictatorship and a purveyor of conspiracy theories about the Rothschilds.
Pompeo isn’t the only one who’s changed his mind about the man holed up for five long years at the Ecuador embassy in London. The U.S. Justice Department, headed by Jeff Sessions—a man who conveniently forgot while testifying before Congress that he twice met with the Russian ambassador to the United States—now considers arresting Assange a “priority.” [Continue reading…]
Arresting Assange is a “priority” of an undisclosed magnitude — I’m doubtful that it can be particularly high.
No doubt at a time when this administration is going out of its way to create the appearance that it has no ties to Russia, a tough-on-Wikileaks stance might seem desirable.
But let’s not forget that Assange himself has repeatedly claimed that he is willing to accept extradition to the United States.
So is it just a matter of time before the cable news networks will be able to feast on 24/7 coverage of the trial of the century?
Probably not.
Ignoring the question of whether the Justice Department can actually construct a legal case against Assange, I seriously doubt that the White House would welcome seeing him testifying in court. Indeed he might not even make it to his own trial if he sought and received immunity as an FBI witness.
The message that the U.S. wants to get its hands on Assange may have had less to do with challenging his ability to remain in refuge than it has with making sure he remains where he is. Likewise, he will probably remain a problem Moscow doesn’t need to solve so long as he stays put.
The irony is that if Assange had complied with Sweden’s request to question him in 2010, whatever the outcome of that interrogation, it is quite likely that by now he would be a free man. Instead he endures a self-imposed prison sentence for which there is no end in sight.
When Nigel Farage met Julian Assange
Carole Cadwalladr writes: On 9 March 2017, an ordinary Thursday morning, Ian Stubbings, a 35-year-old Londoner, was walking down the street near his office in South Kensington when he spotted a familiar face. He turned and saw a man entering the redbrick terrace which houses the Ecuadorian embassy, where the WikiLeaks founder Julian Assange has been holed up since 2012. And the familiar face? It was Nigel Farage, the man who spearheaded Britain’s exit from the European Union.
“I thought ‘hang on a moment’,” Stubbings says. “‘That looks a bit dodgy.’ I knew the building was the embassy because I often see camera crews outside. But there was no one else around. I was the only person who’d seen him. And I didn’t know what the significance was – and I still don’t actually – but I thought: that’s got to be worth telling and I was the only person who’d witnessed it.”
So, at 11.22am, he tweeted it. His handle is @custardgannet and he wrote: “Genuine scoop: just saw Nigel Farage enter the Ecuadorian embassy.” Moments later, a reporter from BuzzFeed, who happened to follow him on Twitter, picked it up and tweeted him back, and Stubbings told her: “No press or cameras around.”
No press or cameras around, that is, until BuzzFeed turned up just in time to catch Farage leaving, 40 minutes later. “Nigel Farage Just Visited the Ecuadorian Embassy in London,” the headline said. “Asked by BuzzFeed News if he’d been visiting Julian Assange, the former Ukip leader said he could not remember what he had been doing in the building.”
And that was how the world found out, by accident, that the founder of WikiLeaks, the organisation which published Hillary Clinton’s leaked emails – a decisive advantage for Donald Trump’s campaign – and Farage, a friend of Donald Trump, were mutually acquainted. [Continue reading…]
U.S. prepares charges to seek arrest of WikiLeaks’ Julian Assange
CNN reports: US authorities have prepared charges to seek the arrest of WikiLeaks founder Julian Assange, US officials familiar with the matter tell CNN.
The Justice Department investigation of Assange and WikiLeaks dates to at least 2010, when the site first gained wide attention for posting thousands of files stolen by the former US Army intelligence analyst now known as Chelsea Manning.
Prosecutors have struggled with whether the First Amendment precluded the prosecution of Assange, but now believe they have found a way to move forward.
During President Barack Obama’s administration, Attorney General Eric Holder and officials at the Justice Department determined it would be difficult to bring charges against Assange because WikiLeaks wasn’t alone in publishing documents stolen by Manning. Several newspapers, including The New York Times, did as well. The investigation continued, but any possible charges were put on hold, according to US officials involved in the process then.
The US view of WikiLeaks and Assange began to change after investigators found what they believe was proof that WikiLeaks played an active role in helping Edward Snowden, a former NSA analyst, disclose a massive cache of classified documents.
Assange remains holed up in the Ecuadorian embassy in London, seeking to avoid an arrest warrant on rape charges in Sweden. In recent months, US officials had focused on the possibility that a new government in Ecuador would expel Assange and he could be arrested. But the left-leaning presidential candidate who won the recent election in the South American nation has promised to continue to harbor Assange. [Continue reading…]
CIA chief Pompeo: Wikileaks ‘hostile intelligence service’
BBC News reports: The head of the CIA Mike Pompeo has described anti-secrecy organisation WikiLeaks as a “non-state hostile intelligence service” that is often abetted by states such as Russia.
Russian military intelligence used Wikileaks to distribute hacked material during the US election, he added.
Earlier this month Wikileaks published details of what it said were CIA hacking tools.
The FBI and CIA have launched a criminal investigation into the leak.
“WikiLeaks walks like a hostile intelligence service and talks like a hostile intelligence service,” Mr Pompeo said, speaking at a Washington think tank.
“It overwhelmingly focuses on the US, while seeking support from anti-democratic countries and organisations,” he added. [Continue reading…]
Leaked emails reveal Nigel Farage’s long-standing links to Julian Assange
Business Insider reports: There was much confusion Thursday [3/9] when Nigel Farage was spotted by BuzzFeed leaving the Ecuadorian Embassy in London — the residence of WikiLeaks founder Julian Assange.
Asked why he was there, Farage replied that he couldn’t remember what he was doing in the building, adding, “I never discuss where I go or who I see.”
Emails leaked to Business Insider, however, reveal that UKIP under Farage’s leadership had long-standing links to Assange. [Continue reading…]
Wikileaks-Russia link revealed: site hosted in Russia, hacking suspect named
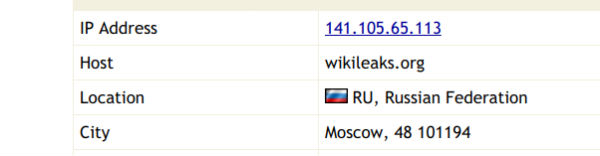
Inquisitr reports: The Wikileaks site is at least partly hosted on servers based in Russia — servers that it added just one week before the site released thousands of hacked emails from the account of John Podesta, chairman of the Hillary Clinton presidential campaign, in October of last year according to findings published in an online report on Sunday.
The Podesta emails, while containing no major revelations, revealed members of Clinton’s campaign speaking privately, in frank terms that proved embarrassing and likely damaging to her campaign for president against Donald Trump. United States intelligence agencies, according to a report issued by the Director of National Intelligence in January, concluded that a Russian government-sponsored hacking effort was behind the Podesta leak and other cyber-attacks — which were designed to help throw the election to Donald Trump.
Sunday’s online report, authored by freelance journalist Laurelai Bailey, examined a list of internet IP addresses used by Wikileaks to host its site, which houses numerous large troves of leaked and hacked documents, and found two addresses of servers in Russia and hosted by a company run by an individual named Peter Chayanov.
“Now the actual owner of the IP addresses is a man by the name of Peter Chayanov, whose IP addresses have hosted spammers and hackers, according to my sources, who work in internet backbone companies,” Bailey wrote. “Chayanov’s IP space is a virtual equivalent of a bad neighborhood that makes you lock your car doors when you drive through it. So this further implies a connection to Wikileaks and Russian hackers.”
To read the full report by Bailey, click on this link. [Continue reading…]
Patribotics reports: The internet is tightly controlled in Russia. Cyber criminals have to answer to Putin. Mr. Chayanov is the head of a firm called Hostkey, which hosts mail spammers and other malware and hacking tools, despite offering web space to Wikileaks. Wikileaks chose to use a Russian hacker to host their site – and they knew that he was connected to Vladimir Putin and operated with the blessing of Putin’s government.
Putin and Assange are thus already linked.
But it is much worse for Wikileaks – and the internet in general – even than it looks. In order not to bury the lede, I will report what appear to be the conclusions of the web developers and hackers on Twitter discussing Laurelai’s story, and then report on how they appeared to have arrived there.
* Wikileaks has handed Chayanov access to everything stored on its site and servers
* The Russian hacker and spammer can ‘monitor traffic’
* He can tell who is reading anything on the Wikileaks site anywhere in the world
* The Russian hacker has access to all documents that have been sent to Wikileaks
* He can probably bust the anonymity of any computer or user who thought they were anonymously donating to Wikileaks
* It is not reasonable to suggest that this hacker is other than linked with Russia’s GRU – if he has it, they have it
* Through Julian Assange and his website, it appears that the Russian hacker and his government can track any readers of the Wikileaks site and any donors of material to it, thus allowing Russia to ‘blackmail’ anyone who ‘sent secrets’ to Wikileaks as a ‘whistleblower’. [Continue reading…]
Authorities question CIA contractors in connection with WikiLeaks dump
The Wall Street Journal reports: Investigators probing who may have provided WikiLeaks with classified information about the Central Intelligence Agency’s purported computer-hacking techniques are zeroing in on a small number of contractors who have worked for the agency and may have been disgruntled over recent job losses, according to people familiar with the investigation.
Authorities on Thursday questioned a handful of contractors working in at least two locations in the Virginia suburbs of Washington, D.C., these people said. Law-enforcement officials said no arrests had been made, but one person familiar with the investigation said it was “rapidly unfolding.”
This person added that a digital trail has pointed authorities, at least initially, to a team of software developers working with the CIA’s Engineering Development Group. The group designs tools that, according to the documents released this week by WikiLeaks, the CIA uses to break into smartphones, personal computers and televisions connected to the internet. The more than 8,000 pages of documents that WikiLeaks disclosed appear to have been taken last December from a server that the Engineering Development Group uses, this person said, and that “only a few contractors would have access to.”
More than a dozen companies work for the CIA on hacking projects, the bulk of them at a facility near Chantilly, Va. It wasn’t clear which companies the people who were questioned worked for. In recent months, there has been talk of “bad blood” in the small world of CIA contractors who are vital to the agency’s hacking projects, the people familiar with the probe said. One group of contractors recently had been working for the CIA overseas and expected to be given new jobs with the agency in the U.S., but their positions were later eliminated, one person said. [Continue reading…]
The truth about the WikiLeaks CIA cache
Zeynep Tufekci writes: On Tuesday morning, WikiLeaks released an enormous cache of documents that it claimed detailed “C.I.A. hacking tools.” Immediately afterward, it posted two startling tweets asserting that “C.I.A. hacker malware” posed a threat to journalists and others who require secure communication by infecting iPhone and Android devices and “bypassing” encrypted message apps such as Signal and WhatsApp.
This appeared to be a bombshell. Signal is considered the gold standard for secure communication. WhatsApp has a billion users. The C.I.A., it seemed, had the capacity to conduct sweeping surveillance on what we had previously assumed were our safest and most private digital conversations.
In their haste to post articles about the release, almost all the leading news organizations took the WikiLeaks tweets at face value. Their initial accounts mentioned Signal, WhatsApp and other encrypted apps by name, and described them as “bypassed” or otherwise compromised by the C.I.A.’s cyberspying tools.
Yet on closer inspection, this turned out to be misleading. Neither Signal nor WhatsApp, for example, appears by name in any of the alleged C.I.A. files in the cache. (Using automated tools to search the whole database, as security researchers subsequently did, turned up no hits.) More important, the hacking methods described in the documents do not, in fact, include the ability to bypass such encrypted apps — at least not in the sense of “bypass” that had seemed so alarming. Indeed, if anything, the C.I.A. documents in the cache confirm the strength of encryption technologies. [Continue reading…]
How the CIA’s hacking hoard makes everyone less secure
Andy Greenberg writes: When Wikileaks yesterday released a trove of documents purporting to show how the CIA hacks everything from smartphones to PCs to smart televisions, the agency’s already shadowy reputation gained a new dimension. But if you’re an average American, rather than Edward Snowden or an ISIS jihadi, the real danger clarified by that leak wasn’t that someone in Langley is watching you through your hotel room’s TV. It’s the rest of the hacker world that the CIA has inadvertently empowered.
As security researchers and policy analysts dig through the latest WikiLeaks documents, the sheer number of hacking tools the CIA has apparently hoarded for exploiting zero-day vulnerabilities—secret inroads that tech firms haven’t patched—stands out most. If the US intelligence community knows about them, that leaves open the possibility that criminal and foreign state hackers do as well.
Its broad zero-day stash, then, strongly suggests that the CIA—along with other intelligence agencies—has long allowed Americans to remain vulnerable to those same attacks. Now that those hacking secrets are public, potentially along with enough details to replicate them, the danger of the feds leaving major security flaws unfixed only escalates.
“If the CIA can use it, so can the Russians, or the Chinese or organized crime,” says Kevin Bankston, the director of the New America Foundation’s Open Technology Institute. “The lesson here, first off, is that stockpiling a bunch of vulnerabilities is bad for cybersecurity. And two, it means they’re likely going to get leaked by someone.”
It’s no surprise, of course, that one of America’s most well-resourced spy agencies can hack its foreign adversaries. The shock, says Johns Hopkins cryptographer Matt Green, comes instead from the sudden spill of those hacking tools onto the web. “In the same way the military would probably have one technique for killing every single tank in an enemy’s arsenal, you would expect the CIA to collect the same thing,” says Green. “What’s different is that we’re seeing them out in public.”
In fact, WikiLeaks wrote in a note accompanying its Tuesday release that “the archive appears to have been circulated among former US government hackers and contractors in an unauthorized manner.” That raises the possibility the full document set, along with actual exploit details or code, may have fallen into the hands of hackers long before it was published in part by WikiLeaks. [Continue reading…]
Wikileaks files show the CIA repurposing hacking code to save time, not to frame Russia
The Intercept reports: Attributing hacking attacks to the correct perpetrators is notoriously difficult. Even the U.S. government, for all its technical resources and expertise, took warranted criticism for trying to pin a high-profile 2014 cyberattack on North Korea, and more recently faced skepticism when it blamed Russia for hacks against top Democrats during the 2016 election.
In those cases, government officials said they based their attribution in part on software tools the hackers employed, which had been used in other cyberattacks linked to North Korea and Russia. But that sort of evidence is not conclusive; hackers have been known to intentionally use or leave behind software and other distinctive material linked to other groups as part of so-called false flag operations intended to falsely implicate other parties. Researchers at Russian digital security firm Kaspersky Lab have documented such cases.
On Tuesday, Wikileaks published a large cache of CIA documents that it said showed the agency had equipped itself to run its own false-flag hacking operations. The documents describe an internal CIA group called UMBRAGE that Wikileaks said was stealing the techniques of other nation-state hackers to trick forensic investigators into falsely attributing CIA attacks to those actors. According to Wikileaks, among those from whom the CIA has stolen techniques is the Russian Federation, suggesting the CIA is conducting attacks to intentionally mislead investigators into attributing them to Vladimir Putin.
“With UMBRAGE and related projects, the CIA can not only increase its total number of attack types, but also misdirect attribution by leaving behind the ‘fingerprints’ of the groups that the attack techniques were stolen from,” Wikileaks writes in a summary of its CIA document dump
It’s a claim that seems intended to shed doubt on the U.S. government’s attribution of Russia in the DNC hack; the Russian Federation was the only nation specifically named by Wikileaks as a potential victim of misdirected attribution. It’s also a claim that some media outlets have accepted and repeated without question.
“WikiLeaks said there’s an entire department within the CIA whose job it is to ‘misdirect attribution by leaving behind the fingerprints’ of others, such as hackers in Russia,” CNN reported without caveats.
It would be possible to leave such fingerprints if the CIA were re-using unique source code written by other actors to intentionally implicate them in CIA hacks, but the published CIA documents don’t say this. Instead they indicate the UMBRAGE group is doing something much less nefarious.
They say UMBRAGE is borrowing hacking “techniques” developed or used by other actors to use in CIA hacking projects. This is intended to save the CIA time and energy by copying methods already proven successful. If the CIA were actually re-using source code unique to a specific hacking group this could lead forensic investigators to mis-attribute CIA attacks to the original creators of the code. But the documents appear to say the UMBRAGE group is writing snippets of code that mimic the functionality of other hacking tools and placing it in a library for CIA developers to draw on when designing custom CIA tools. [Continue reading…]
Russia turns Wikileaks CIA dump into disinformation
Kevin Poulsen reports: For the second time in a matter of months, U.S. intelligence agencies have suffered a devastating breach of their hacking secrets.
But unlike the last breach in August, an American Central Intelligence Agency worker, not Russian hackers, is the most likely source of a new tranche of documents detailing the methods and tools used by the CIA to steal secrets from foreign governments and terror groups — though some experts have seen signs that Russia is working overtime to take advantage of the disclosure.
Tuesday’s document dump, titled “Vault 7, Year Zero” by WikiLeaks, details the capabilities and culture within the CIA’s secretive Center for Cyber Intelligence in Langley, Virginia. The leak portrays a robust, if not unique, computer-intrusion capability inside the CIA, accented by a few James Bond novelties, like special snooping software intended to be carried into an adversary’s lair on a thumb drive, where a CIA asset plugs it into a USB port. Another program, code-named Weeping Angel, turns a Samsung smart TV into a covert listening device.
The leak follows an incident last August when a mysterious group or individual called the Shadow Brokers began publishing hacking tools stockpiled by the NSA’s elite Tailored Access Operations group, including dozens of backdoor programs and 10 exploits. Experts suspected the Shadow Brokers were a shot across the bow by Russia’s intelligence services.
But the CIA leak could be worse for U.S. intelligence, because it includes code from the agency’s malware development frameworks. Using that code, security experts and counterintelligence agents could sniff out a variety of CIA malware. “For the CIA this is huge loss,” said Jake Williams, founder of Rendition Infosec. “For incident responders like me, this is a treasure trove.” [Continue reading…]
Wikileaks and the CIA’s hacking arsenal
CIA's job includes spying on targets who might have various electronics. This is exactly the sort of toolkit you’d expect them to have.
— matt blaze (@mattblaze) March 8, 2017
Julian Sanchez writes: It’s a cliche of political scandals that “the coverup is worse than the crime”: Attempts to conceal misconduct, because they’re easier to prove and provide otherwise elusive evidence of a guilty mind, often end up being more politically damaging than the underlying misconduct would have been. In the case of the latest Wikileaks document dump, the first in a planned series from a cache the site has dubbed “Vault 7,” we have an apparent reversal of the formula: The un-coverup—the fact of the leak itself—is probably more significant than the substance of what has thus far been revealed.
There are, of course, some points of real interest in the archive of documents, mostly concerning an array of hacking tools and software exploits developed or used by the Central Intelligence Agency’s Engineering Development Group — and it’s likely more will emerge as reporters and analysts churn through more than 8,000 files and documents. We’ve confirmed that the CIA has hung onto and exploited at least a handful of undisclosed “zero day” vulnerabilities in widely-used software platforms, including Apple’s iOS and Google’s Android, the operating systems on which nearly all modern smartphones run.
We also learn that — as many of us expected — the obstacles to conventional wiretapping posed by the growing prevalence of encryption have spurred intelligence agencies to hunt for alternative means of collection, which include not only compromising communications endpoints such as smartphones, but also seeking to repurpose networked appliances on the Internet of Things as surveillance devices. The latter goal has even spawned its own research department, the Embedded Development Branch.
Still, in light of what we already knew about the National Security Agency’s own efforts along similar lines, thanks to Edward Snowden’s disclosures about the agency’s Tailored Access Operations division, this is—at least from a policy perspective—not so much revelation as confirmation. Moreover, there’s little here to suggest surveillance that’s either aimed at Americans or indiscriminate, the features that made Snowden’s leaks about NSA surveillance so politically explosive. One of the more widely-reported projects in Vault 7, for instance, has been the Doctor Who — referencing “Weeping Angel” implant, which can turn Samsung televisions into surveillance microphones even when they appear to be turned off. Yet, at least at the time the documentation in the Wikileaks release was written, Weeping Angel appeared to require physical access to be installed—which makes it essentially a fancy and less detectable method of bugging a particular room once a CIA agent has managed to get inside. This is all fascinating to surveillance nerds, to be sure, but without evidence that these tools have been deployed either against inappropriate targets or on a mass scale, it’s not intrinsically all that controversial. Finding clever ways to spy on people is what spy agencies are supposed to do. [Continue reading…]
