Kurt Marko writes: A new form of highly targeted cyber attack patently demonstrates the shift in malware sophistication and motivation. Annoying hacker pranks done for fun and sport have been supplanted by sophisticated, multi-stage software systems designed for espionage and profit. The new attack, discovered by TrapX, a developer of security software formerly known as CyberSense, is one of an increasingly common genre known as an Advanced Persistent Threat (APT) of the type that stole debit card numbers from Target or sensitive data and login credentials from any number of companies. What makes this recent attack noteworthy isn’t its basic design, operation or targets, but means of initial delivery: contaminated firmware on a type of industrial barcode scanner commonly used in the shipping and logistics industry. Similar to the technique used to introduce the infamous Stuxnet worm that took out Iranian centrifuges and managed to penetrate ostensibly highly secure networks via ordinary USB thumb drives, the so-called Zombie Zero worm invaded corporate data centers through a back door. [Continue reading…]
Category Archives: cyberattacks
Study: 97% of companies using network defenses get hacked anyway
Ars Technica: A security study drawing data from more than 1,600 networks over a six-month period found that 97 percent of the networks experienced some form of breach—despite the use of multiple layers of network and computer security software. The study, performed by analysts from security appliance vendor FireEye and its security consulting wing Mandiant, compared current network defenses to the Maginot Line, the infamous French fortress chain that the Germans bypassed during their May 1940 invasion.
The data collected from network and e-mail monitoring appliances from October 2013 to March 2014 also showed that three-quarters of the networks had command-and-control traffic indicating the presence of active security breaches connected to over 35,000 unique command-and-control servers. Higher-education networks were the biggest source of botnet traffic.
Ukraine crisis proves cyber conflict is a reality of modern warfare
Jarno Limnéll writes: A hundred years ago, World War I moved warfare into the skies. Today no nation regards its security as complete without an air force, and no serious future conflict will lack a cyber aspect, either.
Russia and Ukraine apparently traded cyber attacks during the referendum on Crimea. Media reports indicate NATO and Ukrainian media websites suffered DDoS (denial of service) assaults during the vote, and that servers in Moscow took apparently retaliatory – and bigger – strikes afterward.
Observers tend to miss, though, that these are relatively modest skirmishes in cyber space. They routinely break out among competing states, even without concurrent political or military hostilities. Angling to hobble an opponent’s web resources by clogging networks with junk traffic? Another day at the office.
I see three distinct levels or “rings” to contemporary cyber conflicts. Only the first is clearly apparent in the Ukraine crisis. Full-blown cyber war is not yet occurring. The prospect of escalation, however, is real and worrisome. The West should watch carefully, because developments in Ukraine offer a model for contemporary conflicts worldwide – which will henceforth have integral cyber elements for all but the least developed nations.
By observing Ukraine we can deduce not only the capabilities of cyber weapons, but the goals and policies behind their use. [Continue reading…]
FBI keeps internet flaws secret to defend against hackers
Bloomberg reports: The Obama administration is letting law enforcement keep computer-security flaws secret in order to further U.S. investigations of cyberspies and hackers.
The White House has carved out an exception for the Federal Bureau of Investigation and other agencies to keep information about software vulnerabilities from manufacturers and the public. Until now, most debate has focused on how the National Security Agency stockpiles and uses new-found Internet weaknesses, known as zero-day exploits, for offensive purposes, such as attacking the networks of adversaries.
The law enforcement operations expose a delicate and complicated balancing act when it comes to agencies using serious security flaws in investigations versus disclosing them to protect all Internet users, according to former government officials and privacy advocates. [Continue reading…]
Two major threats to the internet: The U.S. government and the Russian government
Ars Technica: Hector Xavier Monsegur, the hacker known as “Sabu,” became a confidential FBI informant following his 2011 arrest. But he continued to direct other hackers to attack more than 2,000 Internet domains in 2012, including sites operated by the Iranian, Syrian, and Brazilian governments.
Based on documents obtained by the New York Times, those attacks were carried out with the knowledge of the FBI agents supervising Monsegur. The Times report suggests that the data obtained in the attacks—including information on Syrian government sites—was passed to US intelligence agencies by the FBI.
Russian President Vladimir Putin clearly wants to exploit the climate of distrust that has been generated by the NSA and other branches of the U.S. government that have undermined internet security and sees in this the opportunity to push for a Russian internet — one in which the Russian government can exercise greater control over social media.
Vesti.ru reports (translation):
“The Internet emerged as a special project of the CIA USA, and continues to be developed as such,” said Putin [at the conference Mediaforum in St. Petersburg today]. Moreover, the president noted that the national search engine Yandex and the social network VKontakte are trying to develop business, mathematical and informational programming in Russia. “Our companies didn’t have resources free for such capital investments, but now they have appeared,” said the head of state. Putin expressed the hope that the Russian Internet would develop rather intensively and rapidly and will secure the interests of the Russian Federation.”
Meanwhile, ITAR-TASS reports:
Russia’s popular bloggers will now have to brace for considerable restrictions of their rights. The State Duma has just adopted a law introducing new rules they will have to abide by. The document incorporates a package of bills for effective struggle against terrorism and extremism. Earlier, the bill drew a mixed response from society, including sharp criticism from human rights activists.
The law introduces a new term: “Internet user called blogger.” Bloggers will be obliged to declare their family name and initials and e-mail address. Those authors whose personal website or page in social networks has 3,000 visitors or more a day must have themselves registered on a special list and abide by restrictions applicable to the mass media. In other words, registration requires the blogger should check the authenticity of published information and also mention age restrictions for users. Also, bloggers will have to follow mass media laws concerning electioneering, resistance to extremism and the publication of information about people’s private lives. An abuse of these requirements will be punishable with a fine of 10,000 to 30,000 roubles (roughly 300 dollars to 1,000 dollars) for individuals and 300,000 roubles (10,000 roubles) for legal entities. A second violation will be punishable with the website’s suspension for one month.
The Russian investigative journalists Andrei Soldatov and Irina Borogan write:
The NSA scandal made a perfect excuse for the Russian authorities to launch a campaign to bring global web platforms such as Gmail and Facebook under Russian law—either requiring them to be accessible in Russia by the domain extension .ru, or obliging them to be hosted on Russian territory. Under Russian control, these companies and their Russian users could protect their data from U.S. government surveillance and, most importantly, be completely transparent for Russian secret services.
Russia wants to shift supervision and control of the Internet from global companies to local or national authorities, allowing the FSB more authority and latitude to thwart penetration from outside. At December’s International Telecommunications Union (ITU) conference in Dubai, Moscow tried to win over other countries to its plan for a new system of control. The key to the project is to hand off the functions of managing distribution of domain names/IP-addresses from the U.S.-based organization ICANN to an international organization such as the ITU, where Russia can play a central role. Russia also proposed limiting the right of access to the Internet in such cases where “telecommunication services are used for the purpose of interfering in the internal affairs or undermining the sovereignty, national security, territorial integrity, and public safety of other states, or to divulge information of a sensitive nature.” Some 89 countries voted for the Russian proposals, but not the United States, United Kingdom, Western Europe, Australia, or Canada. The result is a stalemate.
Web services would be required to build backdoors for the Russian secret services to access what’s stored there. Prominent Russian MP Sergei Zheleznyak, a member of the ruling United Russia party, has called on Russia to reclaim its “digital sovereignty” and wean its citizens off foreign websites. He said he would introduce legislation this fall to create a “national server,” which analysts say would require foreign websites to register on Russian territory, thus giving the Kremlin’s own security services the access they have long been seeking. Of course, building such a national system would defeat the global value of the Internet.
Shane Harris writes:
When U.S. officials warn of the threat foreign cyber spies pose to American companies and government agencies, they usually focus on China, which has long been home to the world’s most relentless and aggressive hackers. But new information shows that Russian and Eastern European hackers, who have historically focused their energies on crime and fraud, now account for a large and growing percentage of all cyber espionage, most of which is directed at the United States.
Individuals and groups in Eastern Europe, and particularly in Russia and Russian-speaking countries, are responsible for a fifth of all cyber spying incidents in the world, according to a global study of data breaches conducted by Verizon, published this week. The spies are targeting a range of companies as varied as the global economy itself, and are stealing manufacturing designs, proprietary technology and confidential business plans. The cyber spies steal information on behalf of their governments in order to manufacture cheaper versions of technologies or weapons systems, or to give their home country’s corporations a leg up on their foreign competitors.
The Internet is broken: SEC probes threat from cyber attacks against Wall Street
Bloomberg reports: The U.S. Securities and Exchange Commission is examining the exposure of stock exchanges, brokerages and other Wall Street firms to cyber-attacks that have been called a threat to financial stability.
The SEC held a roundtable discussion of those risks in Washington today as it weighs a proposal to require stock exchanges to protect their critical technology and tell members about breaches of important systems. More than half of exchanges surveyed globally in 2012 said they experienced a cyber-attack, while 67 percent of U.S. exchanges said a hacker tried to penetrate their systems.
Dennis Fisher writes: Costin Raiu is a cautious man. He measures his words carefully and says exactly what he means, and is not given to hyperbole or exaggeration. Raiu is the driving force behind much of the intricate research into APTs and targeted attacks that Kaspersky Lab’s Global Research and Analysis Team has been doing for the last few years, and he has first-hand knowledge of the depth and breadth of the tactics that top-tier attackers are using.
So when Raiu says he conducts his online activities under the assumption that his movements are being monitored by government hackers, it is not meant as a scare tactic. It is a simple statement of fact.
“I operate under the principle that my computer is owned by at least three governments,” Raiu said during a presentation he gave to industry analysts at the company’s analyst summit here on Thursday.
The comment drew some chuckles from the audience, but Raiu was not joking. Security experts for years have been telling users — especially enterprise users — to assume that their network or PC is compromised. The reasoning is that if you assume you’re owned then you’ll be more cautious about what you do. It’s the technical equivalent of telling a child to behave as if his mother is watching everything he does. It doesn’t always work, but it can’t hurt.
Raiu and his fellow researchers around the world are obvious targets for highly skilled attackers of all stripes. They spend their days analyzing new attack techniques and working out methods for countering them. Intelligence agencies, APT groups and cybercrime gangs all would love to know what researchers know and how they get their information. Just about every researcher has a story about being attacked or compromised at some point. It’s an occupational hazard.
But one of the things that the events of the last year have made clear is that the kind of paranoia and caution that Raiu and others who draw the attention of attackers employ as a matter of course should now be the default setting for the rest of us, as well. As researcher Claudio Guarnieri recently detailed, the Internet itself is compromised. Not this bit or that bit. The entire network. [Continue reading…]
Last year, CSIS reported: After years of guesswork and innumerable attempts to quantify the costly effects of cybercrime on the U.S. and world economies, McAfee engaged one of the world’s preeminent international policy institutions for defense and security, the Center for Strategic and International Studies (CSIS) to build an economic model and methodology to accurately estimate these losses, which can be extended worldwide. “Estimating the Cost of Cybercrime and Cyber Espionage” posits a $100 billion annual loss to the U.S. economy and as many as 508,000 U.S. jobs lost as a result of malicious cyber activity.
U.S. notified 3,000 companies in 2013 about cyberattacks
The Washington Post reports: Federal agents notified more than 3,000 U.S. companies last year that their computer systems had been hacked, White House officials have told industry executives, marking the first time the government has revealed how often it tipped off the private sector to cyberintrusions.
The alerts went to firms large and small, from local banks to major defense contractors to national retailers such as Target, which suffered a breach last fall that led to the theft of tens of millions of Americans’ credit card and personal data, according to government and industry officials.
“Three thousand companies is astounding,” said James A. Lewis, a senior fellow and cyberpolicy expert at the Center for Strategic and International Studies. “The problem is as big or bigger than we thought.”
The number reflects only a fraction of the true scale of cyberintrusions into the private sector by criminal groups and foreign governments and their proxies, particularly in China and Eastern Europe. The estimated cost to U.S. companies and consumers is up to $100 billion annually, analysts say. [Continue reading…]
Can we trust an Internet that’s become a weapon of governments?
MIT Technology Review: Security experts have been warning for some time that computer networks are not secure from intruders. But in 2013, we learned that the mayhem has become strategic. Governments now write computer viruses. And if they can’t, they can purchase them. A half-dozen boutique R&D houses, like Italy’s Hacking Team, develop computer vulnerabilities and openly market them to government attackers.
Criminals use common computer weaknesses to infect as many machines as possible. But governments assemble large research teams and spend millions patiently pursuing narrow objectives. Costin Raiu, who investigates such “advanced persistent threats” as director of research and analysis for anti-virus company Kaspersky Lab, says he logs on to his computer assuming he is not alone. “I operate under the principle that my computer is owned by at least three governments,” he says.
That is a threat mainstream technology companies are grappling with. The U.S. government circumvented Google’s security measures and secretly collected customer data. British spies scooped up millions of webcam images from Yahoo. In December, on Microsoft’s official blog, the company’s top lawyer, Brad Smith, said he had reason to view surreptitious “government snooping” as no different from criminal malware. Microsoft, along with Google and Yahoo, has responded by greatly widening its use of encryption (see “The Year of Encryption”).
“We’re living in a very interesting time, where companies are becoming unwilling pawns in cyberwarfare,” says Menny Barzilay, a former Israeli intelligence officer now working in IT security for the Bank Hapoalim Group, in Tel Aviv. In this new context, nobody can say where the responsibilities of a company may end and those of a nation might begin. Should a commercial bank be expected to expend resources to defend itself when its attacker is a country? “This is not a ‘maybe’ situation. This is happening right now,” says Barzilay. “And this is just the beginning.” [Continue reading…]
Top daily DDoS attacks worldwide
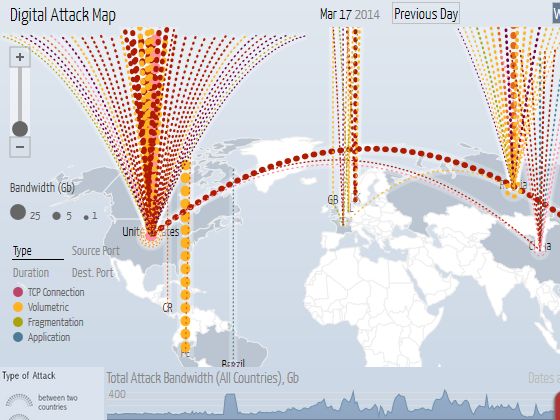
More information at Digital Attack Map, a live data visualization of DDoS attacks around the globe, built through a collaboration between Google Ideas and Arbor Networks.
Cyber-war: In deed and desire, Iran emerging as a major power
Christian Science Monitor reports: As high-level international talks in Vienna over Iran’s nuclear program edged closer to a deal last fall, something curious happened – massive cyber-attacks that had hammered Wall Street bank websites repeatedly for about a year slowed to a near stop.
While banking industry officials were relieved, others wondered why those Iran-linked “distributed denial of service” attacks that had so regularly flooded bank websites with bogus Internet traffic were shut off like a faucet. One likely reason, say US experts on cyber-conflict: to reduce friction, at least temporarily, at the Vienna nuclear talks.
Yet, even as the “distributed denial of service” attacks abated for apparently diplomatic reasons, overall Iranian cyber-spying on US military and energy corporation networks has surged, these experts say.
Iran was fingered last fall, for instance, for infiltrating the US Navy Marine Corps Intranet. It then took the Navy nearly four months to root out the Iranian hackers infesting its largest unclassified computer network, the Wall Street Journal reported in February.
This litany of Iranian activity is evidence, say experts, that after years as a cyber also-ran, Iran is morphing swiftly into a major threat in the rapidly evolving era of cyber-conflict. [Continue reading…]
‘What does ISP mean?’ — how government officials are flunking security challenges
The Guardian reports: One of the world’s leading cyberwarfare experts has warned of the damaging lack of government literacy in cybersecurity issues, pointing out that some senior officials don’t know how to use email, and that one US representative about to negotiate cybersecurity with China asked him what an “ISP” was.
Speaking at the SXSW festival, Dr Peter W Singer, director of the Center for 21st Century Security & Intelligence, cited a 2014 poll by the Pew research institute that found Americans are more afraid of cyberattack than attack by Iran or North Korea, climate change, the rise of China or authoritarian Russia.
Sketching out the scale of technology in our lives, Singer said that 40 trillion emails are sent a year, that 30 trillion websites now exist and that 9 new pieces of malware are discovered every second. He claimed that 97% of Fortune 500 companies have admitted they’ve been hacked – the other 3% just aren’t ready to admit it yet.
The consequent rise in cybercrime and state-sponsored attacks has not gone unnoticed. 100 nations now have cyber command, and the Pentagon’s own briefings, which contained the word ‘cyber’ 12 times during 2012, have already mentioned it 147 times so far this year.
Yet former head of US homeland security Janet Napolitano once told Singer. “Don’t laugh, but I just don’t use email at all,” Singer recalled. “It wasn’t a fear of privacy or security – it’s because she just didn’t think it was useful. A supreme court justice also told me ‘I haven’t got round to email yet’ – and this is someone who will get to vote on everything from net neutrality to the NSA negotiations.” [Continue reading…]
