The Washington Post reports: The Pentagon is significantly growing the ranks of its cyberwarfare unit in an effort to deter and defend against foreign attacks on crucial U.S. networks, Defense Secretary Chuck Hagel said Friday.
In his first major speech on cyber policy, Hagel sought to project strength but also to tame perceptions of the United States as an aggressor in computer warfare, stressing that the government “does not seek to militarize cyberspace.”
His remarks, delivered at the retirement ceremony of Gen. Keith Alexander, the outgoing director of the National Security Agency and Cyber Command, come in advance of Hagel’s trip to China next week, his first as defense secretary. The issues of cyberwarfare and cyber-espionage have been persistent sources of tensions between Washington and Beijing.
Hagel said that the fighting force at U.S. Cyber Command will number more than 6,000 people by 2016, making it one of the largest such forces in the world. The force will help expand the president’s options for responding to a crisis with “full-spectrum cyber capabilities,” Hagel said, a reference to cyber operations that can include destroying, damaging or sabotaging an adversary’s computer systems and that can complement other military operations.
But, Hagel said, the military’s first purpose is “to prevent and de-escalate conflict.” The Pentagon will maintain “an approach of restraint to any cyber operations outside of U.S. government networks.”
Although some U.S. adversaries, notably China and Russia, which also have formidable cyber capabilities, may view his remarks with skepticism, Hagel said the Pentagon is making an effort to be “open and transparent” about its cyberforces and doctrine. The hope, senior officials said, is that transparency will lead to greater stability in cyberspace. [Continue reading…]
Category Archives: Cyber Issues
The Internet is broken: SEC probes threat from cyber attacks against Wall Street
Bloomberg reports: The U.S. Securities and Exchange Commission is examining the exposure of stock exchanges, brokerages and other Wall Street firms to cyber-attacks that have been called a threat to financial stability.
The SEC held a roundtable discussion of those risks in Washington today as it weighs a proposal to require stock exchanges to protect their critical technology and tell members about breaches of important systems. More than half of exchanges surveyed globally in 2012 said they experienced a cyber-attack, while 67 percent of U.S. exchanges said a hacker tried to penetrate their systems.
Dennis Fisher writes: Costin Raiu is a cautious man. He measures his words carefully and says exactly what he means, and is not given to hyperbole or exaggeration. Raiu is the driving force behind much of the intricate research into APTs and targeted attacks that Kaspersky Lab’s Global Research and Analysis Team has been doing for the last few years, and he has first-hand knowledge of the depth and breadth of the tactics that top-tier attackers are using.
So when Raiu says he conducts his online activities under the assumption that his movements are being monitored by government hackers, it is not meant as a scare tactic. It is a simple statement of fact.
“I operate under the principle that my computer is owned by at least three governments,” Raiu said during a presentation he gave to industry analysts at the company’s analyst summit here on Thursday.
The comment drew some chuckles from the audience, but Raiu was not joking. Security experts for years have been telling users — especially enterprise users — to assume that their network or PC is compromised. The reasoning is that if you assume you’re owned then you’ll be more cautious about what you do. It’s the technical equivalent of telling a child to behave as if his mother is watching everything he does. It doesn’t always work, but it can’t hurt.
Raiu and his fellow researchers around the world are obvious targets for highly skilled attackers of all stripes. They spend their days analyzing new attack techniques and working out methods for countering them. Intelligence agencies, APT groups and cybercrime gangs all would love to know what researchers know and how they get their information. Just about every researcher has a story about being attacked or compromised at some point. It’s an occupational hazard.
But one of the things that the events of the last year have made clear is that the kind of paranoia and caution that Raiu and others who draw the attention of attackers employ as a matter of course should now be the default setting for the rest of us, as well. As researcher Claudio Guarnieri recently detailed, the Internet itself is compromised. Not this bit or that bit. The entire network. [Continue reading…]
Last year, CSIS reported: After years of guesswork and innumerable attempts to quantify the costly effects of cybercrime on the U.S. and world economies, McAfee engaged one of the world’s preeminent international policy institutions for defense and security, the Center for Strategic and International Studies (CSIS) to build an economic model and methodology to accurately estimate these losses, which can be extended worldwide. “Estimating the Cost of Cybercrime and Cyber Espionage” posits a $100 billion annual loss to the U.S. economy and as many as 508,000 U.S. jobs lost as a result of malicious cyber activity.
Hackers sell exploits for Bitcoins in underground market
Bloomberg reports: Hackers from the U.S., Russia and Ukraine hawk computer exploits for as much as $300,000 on an underground market fueled by digital currencies like Bitcoin, a report by RAND Corp. and Juniper Networks Inc. shows.
The thriving trade in software, data or commands that takes advantage of computer bugs and glitches generates billions of dollars using digital storefronts that connect sellers with buyers or where mercenaries can be hired to do the job, according to the report released today.
“Anyone with an Internet connection can get involved,” Lillian Ablon, an information systems analyst at RAND and the study’s lead author, said in a phone interview. “If you can’t do something, you can find someone else to do it for you.”
One of the first comprehensive efforts to map out how criminal hackers operate using anonymous networks, encrypted communications and digital currencies, the 83-page report comes amid warnings by U.S. government and industry officials that digital attacks are becoming more sophisticated and dangerous. [Continue reading…]
After reports on NSA, China urges end to spying
The New York Times reports: The Chinese government called on the United States on Monday to explain its actions and halt the practice of cyberespionage after news reports said that the National Security Agency had hacked its way into the computer systems of China’s largest telecommunications company.
The reports, based on documents provided by the former security contractor Edward J. Snowden, related how the spy agency penetrated servers owned by the company, Huawei, and monitored communications by its senior executives in an effort to discover whether the executives had links to the Chinese military. The operation also sought to exploit the company’s technology and gain access to the communications of customers who use Huawei cellphones, fiber optic cables and network hubs.
American officials have been working to block Huawei from entering the American telecommunications market because of concerns that its equipment could provide Chinese hackers with a “back door” for stealing American corporate and government secrets.[Continue reading…]
U.S. notified 3,000 companies in 2013 about cyberattacks
The Washington Post reports: Federal agents notified more than 3,000 U.S. companies last year that their computer systems had been hacked, White House officials have told industry executives, marking the first time the government has revealed how often it tipped off the private sector to cyberintrusions.
The alerts went to firms large and small, from local banks to major defense contractors to national retailers such as Target, which suffered a breach last fall that led to the theft of tens of millions of Americans’ credit card and personal data, according to government and industry officials.
“Three thousand companies is astounding,” said James A. Lewis, a senior fellow and cyberpolicy expert at the Center for Strategic and International Studies. “The problem is as big or bigger than we thought.”
The number reflects only a fraction of the true scale of cyberintrusions into the private sector by criminal groups and foreign governments and their proxies, particularly in China and Eastern Europe. The estimated cost to U.S. companies and consumers is up to $100 billion annually, analysts say. [Continue reading…]
Inside the NSA’s secret efforts to hunt and hack system administrators
Ryan Gallagher and Peter Maass report: Across the world, people who work as system administrators keep computer networks in order – and this has turned them into unwitting targets of the National Security Agency for simply doing their jobs. According to a secret document provided by NSA whistleblower Edward Snowden, the agency tracks down the private email and Facebook accounts of system administrators (or sys admins, as they are often called), before hacking their computers to gain access to the networks they control.
The document consists of several posts – one of them is titled “I hunt sys admins” – that were published in 2012 on an internal discussion board hosted on the agency’s classified servers. They were written by an NSA official involved in the agency’s effort to break into foreign network routers, the devices that connect computer networks and transport data across the Internet. By infiltrating the computers of system administrators who work for foreign phone and Internet companies, the NSA can gain access to the calls and emails that flow over their networks.
The classified posts reveal how the NSA official aspired to create a database that would function as an international hit list of sys admins to potentially target. Yet the document makes clear that the admins are not suspected of any criminal activity – they are targeted only because they control access to networks the agency wants to infiltrate. “Who better to target than the person that already has the ‘keys to the kingdom’?” one of the posts says. [Continue reading…]
Syrian Electronic Army ‘leak’ of Microsoft billing promotes its own agenda
![]() Is Bashar al-Assad a defender of human rights? Does the Syrian Electronic Army respect free speech? No and no. But do either have an interest in exploiting the widespread fears of government surveillance? You bet!
Is Bashar al-Assad a defender of human rights? Does the Syrian Electronic Army respect free speech? No and no. But do either have an interest in exploiting the widespread fears of government surveillance? You bet!
If the leaking of Microsoft documents revealing the charges it makes for complying with FBI requests, serves the public interest (which it probably does), no one should conclude on that basis that the Syrian Electronic Army having facilitated this leak, had any interests in mind other than its own and the government it supports.
Daily Dot reports: Microsoft often charges the FBI’s most secretive division hundreds of thousands of dollars a month to legally view customer information, according to documents allegedly hacked by the Syrian Electronic Army.
The SEA, a hacker group loyal to Syrian President Bashar al-Assad, is best known for hijacking Western media companies’ social media accounts. (These companies include the Associated Press, CNN, NPR, and even the Daily Dot.) The SEA agreed to let the Daily Dot analyze the documents with experts before the group published them in full.
The documents consist of what appear to be invoices and emails between Microsoft’s Global Criminal Compliance team and the FBI’s Digital Intercept Technology Unit (DITU), and purport to show exactly how much money Microsoft charges DITU, in terms of compliance costs, when DITU provides warrants and court orders for customers’ data.
In December 2012, for instance, Microsoft emailed DITU a PDF invoice for $145,100, broken down to $100 per request for information, the documents appear to show. In August 2013, Microsoft allegedly emailed a similar invoice, this time for $352,200, at a rate of $200 per request. The latest invoice provided, from November 2013, is for $281,000.
None of the technologists or lawyers consulted for this story thought that Microsoft would be in the wrong to charge the FBI for compliance, especially considering it’s well within the company’s legal right to charge “reasonable expenses.” Instead, they said, the documents are more of an indication of just how frequently the government wants information on customers. Some of the DITU invoices show hundreds of requests per month.
For ACLU Principal Technologist Christopher Soghoian, the documents reiterated his stance that charging a small fee is a positive, in part because it creates more of a record of government tracking. In 2010, Soghoian actually chided Microsoft for not charging the Drug Enforcement Agency for turning over user records when instructed to by courts, noting that companies like Google and Yahoo did.
Nate Cardozo, a staff attorney for the Electronic Frontier Foundation, agreed, and told the Daily Dot the government should be transparent about how much it pays. [Continue reading…]
Can we trust an Internet that’s become a weapon of governments?
MIT Technology Review: Security experts have been warning for some time that computer networks are not secure from intruders. But in 2013, we learned that the mayhem has become strategic. Governments now write computer viruses. And if they can’t, they can purchase them. A half-dozen boutique R&D houses, like Italy’s Hacking Team, develop computer vulnerabilities and openly market them to government attackers.
Criminals use common computer weaknesses to infect as many machines as possible. But governments assemble large research teams and spend millions patiently pursuing narrow objectives. Costin Raiu, who investigates such “advanced persistent threats” as director of research and analysis for anti-virus company Kaspersky Lab, says he logs on to his computer assuming he is not alone. “I operate under the principle that my computer is owned by at least three governments,” he says.
That is a threat mainstream technology companies are grappling with. The U.S. government circumvented Google’s security measures and secretly collected customer data. British spies scooped up millions of webcam images from Yahoo. In December, on Microsoft’s official blog, the company’s top lawyer, Brad Smith, said he had reason to view surreptitious “government snooping” as no different from criminal malware. Microsoft, along with Google and Yahoo, has responded by greatly widening its use of encryption (see “The Year of Encryption”).
“We’re living in a very interesting time, where companies are becoming unwilling pawns in cyberwarfare,” says Menny Barzilay, a former Israeli intelligence officer now working in IT security for the Bank Hapoalim Group, in Tel Aviv. In this new context, nobody can say where the responsibilities of a company may end and those of a nation might begin. Should a commercial bank be expected to expend resources to defend itself when its attacker is a country? “This is not a ‘maybe’ situation. This is happening right now,” says Barzilay. “And this is just the beginning.” [Continue reading…]
How Target stood by as 40 million credit card numbers were stolen
Bloomberg Businessweek reports: The biggest retail hack in U.S. history wasn’t particularly inventive, nor did it appear destined for success. In the days prior to Thanksgiving 2013, someone installed malware in Target’s security and payments system designed to steal every credit card used at the company’s 1,797 U.S. stores. At the critical moment — when the Christmas gifts had been scanned and bagged and the cashier asked for a swipe — the malware would step in, capture the shopper’s credit card number, and store it on a Target server commandeered by the hackers.
It’s a measure of how common these crimes have become, and how conventional the hackers’ approach in this case, that Target was prepared for such an attack. Six months earlier the company began installing a $1.6 million malware detection tool made by the computer security firm FireEye, whose customers also include the CIA and the Pentagon. Target had a team of security specialists in Bangalore to monitor its computers around the clock. If Bangalore noticed anything suspicious, Target’s security operations center in Minneapolis would be notified.
On Saturday, Nov. 30, the hackers had set their traps and had just one thing to do before starting the attack: plan the data’s escape route. As they uploaded exfiltration malware to move stolen credit card numbers — first to staging points spread around the U.S. to cover their tracks, then into their computers in Russia — FireEye spotted them. Bangalore got an alert and flagged the security team in Minneapolis. And then …
Nothing happened.
For some reason, Minneapolis didn’t react to the sirens. Bloomberg Businessweek spoke to more than 10 former Target employees familiar with the company’s data security operation, as well as eight people with specific knowledge of the hack and its aftermath, including former employees, security researchers, and law enforcement officials. The story they tell is of an alert system, installed to protect the bond between retailer and customer, that worked beautifully. But then, Target stood by as 40 million credit card numbers — and 70 million addresses, phone numbers, and other pieces of personal information — gushed out of its mainframes. [Continue reading…]
Top daily DDoS attacks worldwide
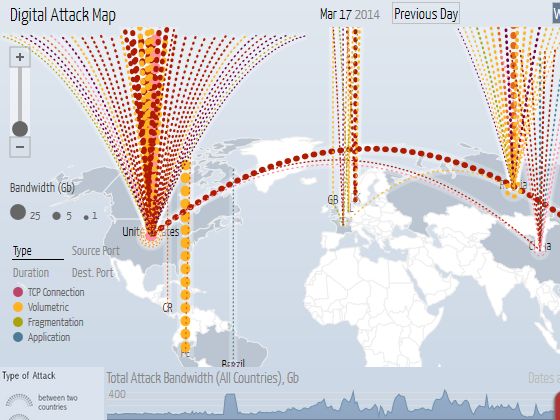
More information at Digital Attack Map, a live data visualization of DDoS attacks around the globe, built through a collaboration between Google Ideas and Arbor Networks.
Cyber-war: In deed and desire, Iran emerging as a major power
Christian Science Monitor reports: As high-level international talks in Vienna over Iran’s nuclear program edged closer to a deal last fall, something curious happened – massive cyber-attacks that had hammered Wall Street bank websites repeatedly for about a year slowed to a near stop.
While banking industry officials were relieved, others wondered why those Iran-linked “distributed denial of service” attacks that had so regularly flooded bank websites with bogus Internet traffic were shut off like a faucet. One likely reason, say US experts on cyber-conflict: to reduce friction, at least temporarily, at the Vienna nuclear talks.
Yet, even as the “distributed denial of service” attacks abated for apparently diplomatic reasons, overall Iranian cyber-spying on US military and energy corporation networks has surged, these experts say.
Iran was fingered last fall, for instance, for infiltrating the US Navy Marine Corps Intranet. It then took the Navy nearly four months to root out the Iranian hackers infesting its largest unclassified computer network, the Wall Street Journal reported in February.
This litany of Iranian activity is evidence, say experts, that after years as a cyber also-ran, Iran is morphing swiftly into a major threat in the rapidly evolving era of cyber-conflict. [Continue reading…]
How the NSA plans to infect ‘millions’ of computers with malware
Ryan Gallagher and Glenn Greenwald report: Top-secret documents reveal that the National Security Agency is dramatically expanding its ability to covertly hack into computers on a mass scale by using automated systems that reduce the level of human oversight in the process.
The classified files – provided previously by NSA whistleblower Edward Snowden – contain new details about groundbreaking surveillance technology the agency has developed to infect potentially millions of computers worldwide with malware “implants.” The clandestine initiative enables the NSA to break into targeted computers and to siphon out data from foreign Internet and phone networks.
The covert infrastructure that supports the hacking efforts operates from the agency’s headquarters in Fort Meade, Maryland, and from eavesdropping bases in the United Kingdom and Japan. GCHQ, the British intelligence agency, appears to have played an integral role in helping to develop the implants tactic.
In some cases the NSA has masqueraded as a fake Facebook server, using the social media site as a launching pad to infect a target’s computer and exfiltrate files from a hard drive. In others, it has sent out spam emails laced with the malware, which can be tailored to covertly record audio from a computer’s microphone and take snapshots with its webcam. The hacking systems have also enabled the NSA to launch cyberattacks by corrupting and disrupting file downloads or denying access to websites.
The implants being deployed were once reserved for a few hundred hard-to-reach targets, whose communications could not be monitored through traditional wiretaps. But the documents analyzed by The Intercept show how the NSA has aggressively accelerated its hacking initiatives in the past decade by computerizing some processes previously handled by humans. The automated system – codenamed TURBINE – is designed to “allow the current implant network to scale to large size (millions of implants) by creating a system that does automated control implants by groups instead of individually.” [Continue reading…]
‘What does ISP mean?’ — how government officials are flunking security challenges
The Guardian reports: One of the world’s leading cyberwarfare experts has warned of the damaging lack of government literacy in cybersecurity issues, pointing out that some senior officials don’t know how to use email, and that one US representative about to negotiate cybersecurity with China asked him what an “ISP” was.
Speaking at the SXSW festival, Dr Peter W Singer, director of the Center for 21st Century Security & Intelligence, cited a 2014 poll by the Pew research institute that found Americans are more afraid of cyberattack than attack by Iran or North Korea, climate change, the rise of China or authoritarian Russia.
Sketching out the scale of technology in our lives, Singer said that 40 trillion emails are sent a year, that 30 trillion websites now exist and that 9 new pieces of malware are discovered every second. He claimed that 97% of Fortune 500 companies have admitted they’ve been hacked – the other 3% just aren’t ready to admit it yet.
The consequent rise in cybercrime and state-sponsored attacks has not gone unnoticed. 100 nations now have cyber command, and the Pentagon’s own briefings, which contained the word ‘cyber’ 12 times during 2012, have already mentioned it 147 times so far this year.
Yet former head of US homeland security Janet Napolitano once told Singer. “Don’t laugh, but I just don’t use email at all,” Singer recalled. “It wasn’t a fear of privacy or security – it’s because she just didn’t think it was useful. A supreme court justice also told me ‘I haven’t got round to email yet’ – and this is someone who will get to vote on everything from net neutrality to the NSA negotiations.” [Continue reading…]
Snowden told me the NSA set fire to the web. Silicon Valley needs to put it out
Christopher Soghoian writes: “You are the firefighters,” National Security Agency whistleblower Edward Snowden told a tech savvy audience here yesterday, during my conversation with him at the SXSW festival. “The people in Austin are the ones who can protect our rights through technical standards.”
Ed’s comments were a call to arms for the tech community to protect its users from indiscriminate mass surveillance by the NSA and the insecurity it creates. Despite the talk from Washington DC regarding cybersecurity threats – and you’ll hear more of it today during a confirmation hearing for the would-be next head of the NSA – it is now clear that the NSA’s mass surveillance efforts are not meant for good. Whether it’s systematically undermining global encryption standards, hacking communications companies’ servers and data links or exploiting so-called zero-day vulnerabilities, the nation’s cyberspies are focused on attacking online privacy and weakening the security of systems that we all trust.
Forget all the government rhetoric on cybersecurity: the NSA simply isn’t here to make the Internet more secure. But that doesn’t mean the agency has to win. The global tech community can fight back, if developers ramp up efforts to build privacy and security into their products. By zeroing in on practical steps Ed and I discussed in our conversation here, we can build a more open, free and secure Internet. [Continue reading…]
Experian lapse allowed ID theft service access to 200 million consumer records
Brian Krebs reports: In October 2013, KrebsOnSecurity published an exclusive story detailing how a Vietnamese man running an online identity theft service bought personal and financial records on Americans directly from a company owned by Experian, one of the three major U.S. credit bureaus. Today’s story looks deeper at the damage wrought in this colossal misstep by one of the nation’s largest data brokers.
Last week, Hieu Minh Ngo, a 24-year-old Vietnamese national, pleaded guilty to running an identity theft service out of his home in Vietnam. Ngo was arrested last year in Guam by U.S. Secret Service agents after he was lured into visiting the U.S. territory to consummate a business deal with a man he believed could deliver huge volumes of consumers’ personal and financial data for resale.
But according to prosecutors, Ngo had already struck deals with one of the world’s biggest data brokers: Experian. Court records just released last week show that Ngo tricked an Experian subsidiary into giving him direct access to personal and financial data on more than 200 million Americans. [Continue reading…]
Watch: Edward Snowden at SXSW (via planet Mars)
The Guardian reports: Encryptions tools must be simplified and made accessible for the mainstream, Pulitzer-winning journalist Barton Gellman said on Monday, calling on the tech industry to have the courage and ingenuity to help address the disparity of power between the people and their government.
Addressing the SXSW festival shortly before Edward Snowden’s live speech by video, Gellman said we are a long way off simple, transparent encryption tools. He cited Pew research which found that 88% of Americans say they have taken steps to protect their privacy in some form.
“With all the user interface brains out there we could get easier tools,” he said. “But it’s not just the ability to encrypt, it’s a frame of mind, a workflow and a discipline that is alien to most people, and that is the opposite to the open nature of the consumer internet. You could use Tor to access a site a hundred times, but the 101st time you forget, you may as well not have used Tor.”
“There are people at this conference who have taken very considerable risk to protect the privacy of their customers and have put themselves at the edge of the door to jail and it will take courage as well as ingenuity to change the way things work.” [Continue reading…]
Note: The audio quality of Snowden’s feed renders him virtually unintelligible, but Christopher Soghoian, the American Civil Liberties Union’s principal technologist, comes through loud and clear.
Hacking Team’s foreign espionage infrastructure located in U.S.
Threat Post reports: Milan-based Hacking Team relies on servers in the United States and hosted by American companies to support its clients’ state-sponsored surveillance operations in some of the world’s most repressive regimes.
Hacking Team is an Italian security firm that develops surveillance equipment and sells it to foreign governments that allegedly turn around and use that equipment to spy on various targets. According to a new report from the University of Toronto’s Citizen Lab, in at least 12 cases, U.S.-based data centers contain servers that have some nexus in the infrastructure of foreign espionage.
The specific tool sold by Hacking Team is known as Remote Control System (RCS). According to the report, RCS has the capacity to spy on Skype conversations, email communications, and instant messaging services in addition to siphoning off passwords and local computer files. [Continue reading…]
The culture of hacking in China
The New York Times reported last May: Name a target anywhere in China, an official at a state-owned company boasted recently, and his crack staff will break into that person’s computer, download the contents of the hard drive, record the keystrokes and monitor cellphone communications, too.
Pitches like that, from a salesman for Nanjing Xhunter Software, were not uncommon at a crowded trade show this month that brought together Chinese law enforcement officials and entrepreneurs eager to win government contracts for police equipment and services.
“We can physically locate anyone who spreads a rumor on the Internet,” said the salesman, whose company’s services include monitoring online postings and pinpointing who has been saying what about whom.
The culture of hacking in China is not confined to top-secret military compounds where hackers carry out orders to pilfer data from foreign governments and corporations. Hacking thrives across official, corporate and criminal worlds. Whether it is used to break into private networks, track online dissent back to its source or steal trade secrets, hacking is openly discussed and even promoted at trade shows, inside university classrooms and on Internet forums. [Continue reading…]
