National Journal reports: Backed up against a rapidly approaching do-or-die deadline, bipartisan lawmakers are poised to introduce legislation next week that would roll back the National Security Agency’s expansive surveillance powers.
The legislation could land as soon as Tuesday in the House, congressional aides and privacy advocates said, who would only speak on condition of anonymity because of the sensitivity of the negotiations.
The bill, known as the USA Freedom Act, would effectively end the NSA’s bulk collection of U.S. phone metadata — the numbers, time stamps, and duration of a call but not its actual content — by instead relying on phone companies to retain that data. The program is the first and one of the most controversial spying programs exposed by the Edward Snowden leaks that began nearly two years ago.
House Judiciary Committee Chairman Bob Goodlatte and Rep. John Conyers, the panel’s top Democrat, are expected to back the bill, as is Rep. Jim Sensenbrenner, the author of the original Freedom Act that first emerged in the fall of 2013, and Rep. Jerry Nadler. All four have been intensely involved in negotiations since the measure fell apart in Congress late last year.
But as the House barrels ahead, it remains unclear what strategy the bill’s advocates in the Senate, led chiefly by Sen. Patrick Leahy, intend to deploy. That question is complicated by the implications a fractious national security debate could have for the Republican caucus, whose three presidential aspirants — Sens. Ted Cruz, Rand Paul, and Marco Rubio — have adopted increasingly divergent positions on NSA surveillance. [Continue reading…]
Category Archives: NSA
As encryption spreads, U.S. grapples with clash between privacy, security
The Washington Post reports: For months, federal law enforcement agencies and industry have been deadlocked on a highly contentious issue: Should tech companies be obliged to guarantee government access to encrypted data on smartphones and other digital devices, and is that even possible without compromising the security of law-abiding customers?
Recently, the head of the National Security Agency provided a rare hint of what some U.S. officials think might be a technical solution. Why not, suggested Adm. Michael S. Rogers, require technology companies to create a digital key that could open any smartphone or other locked device to obtain text messages or photos, but divide the key into pieces so that no one person or agency alone could decide to use it?
“I don’t want a back door,” Rogers, the director of the nation’s top electronic spy agency, said during a speech at Princeton University, using a tech industry term for covert measures to bypass device security. “I want a front door. And I want the front door to have multiple locks. Big locks.”
Law enforcement and intelligence officials have been warning that the growing use of encryption could seriously hinder criminal and national security investigations. But the White House, which is preparing a report for President Obama on the issue, is still weighing a range of options, including whether authorities have other ways to get the data they need rather than compelling companies through regulatory or legislative action.
The task is not easy. Those taking part in the debate have polarized views, with advocates of default commercial encryption finding little common ground with government officials who see increasing peril as the technology becomes widespread on mobile phones and on text messaging apps. [Continue reading…]
John Oliver interviews Edward Snowden
NSA weighed ending mass phone surveillance program before Snowden leak
The Associated Press reports: The National Security Agency considered abandoning its secret program to collect and store American calling records in the months before leaker Edward Snowden revealed the practice, current and former intelligence officials say, because some officials believed the costs outweighed the meager counterterrorism benefits.
After the leak and the collective surprise around the world, NSA leaders strongly defended the phone records program to Congress and the public, but without disclosing the internal debate.
The proposal to kill the program was circulating among top managers but had not yet reached the desk of Gen. Keith Alexander, then the NSA director, according to current and former intelligence officials who would not be quoted because the details are sensitive. Two former senior NSA officials say they doubt Alexander would have approved it.
Still, the behind-the-scenes NSA concerns, which have not been reported previously, could be relevant as Congress decides whether to renew or modify the phone records collection when the law authorizing it expires in June.
The internal critics pointed out that the already high costs of vacuuming up and storing the “to and from” information from nearly every domestic landline call were rising, the system was not capturing most cellphone calls, and the program was not central to unraveling terrorist plots, the officials said. They worried about public outrage if the program ever was revealed. [Continue reading…]
To protect our privacy, make the FISA court act like a real court
Faiza Patel and Elizabeth Goitein write: The expiration of key surveillance authorities this spring will force Congress to grapple with the sprawling spying activities exposed by Edward Snowden. Defenders of the status quo sound a familiar refrain: The National Security Agency’s programs are lawful and already subject to robust oversight. After all, they have been blessed not just by Congress but by the judges of the Foreign Intelligence Surveillance Court, or FISA court.
When it comes to the NSA’s mass surveillance programs, however, the FISA court is not acting like a court at all. Originally created to provide a check on the executive branch, the court today behaves more like an adjunct to the intelligence establishment, giving its blanket blessing to mammoth covert programs. The court’s changed role undermines its constitutional underpinnings and raises questions about its ability to exercise meaningful oversight.
The FISA court was born of the spying scandals of the 1970s. After the Church Committee lifted the curtain on decades of abusive FBI and CIA spying on Americans, Congress enacted reforms, including the Foreign Intelligence Surveillance Act of 1978. The law established a special court to review government applications to intercept communications between Americans and foreigners overseas for the purpose of acquiring information about foreign threats. [Continue reading…]
Most Americans approve of mass surveillance
Gregory Ferenstein writes: Years after the world learned that the United States has a vast surveillance apparatus, Americans have generally come to support these programs. In fact, a new report from Pew shows that not only do most Americans approve of mass surveillance, they believe it’s acceptable for the government to engage in more aggressive practices than it probably already does.
Depending on the wording of the question, several polls have found that a majority, or near majority, of Americans believe that the U.S. government should prioritize investigating terrorist threats over protecting privacy. Broadly speaking, 56 percent believe that the National Security Agency’s phone and Internet spying program is an “acceptable way for the government to investigate terrorism.”
But Pew’s latest poll shows just how much spying Americans believe is acceptable. “The public generally believes it is acceptable for the government to monitor many others, including foreign citizens, foreign leaders, and American leaders,” the Pew Report concludes. [Continue reading…]
The NSA’s secret malware domains
Wired reports: The names suggest a parade of a C-list websites. There was NewJunk4U.com and Monster-Ads.net, CoffeeHausBlog.com and SuddenPlot.com. But, these sad-sounding domains actually were artful creations of the National Security Agency: They were fronts for distributing and controlling government malware around the world.
Those domains and 109 others came to light last month as part of the “Equation Group” report from anti-virus vendor Kaspersky. Researchers at Kaspersky identified 300 such domains, and published 113 of them.
The NSA’s malware domains always have been a closely guarded secret—it’s the kind of direct, actionable information that can expose even old cyber espionage operations. Now the agency is in an awkward position: What should it do with these domains now that their covers have been blown? The domains were chosen to look legitimate, which means the US government is effectively cyber squatting on a sizable portfolio of names like newjunk4u.com and businessdealsblog.com that are no longer useful for espionage, but potentially valuable for business. [Continue reading…]
Russian researchers expose breakthrough U.S. spying program
Reuters reports: The U.S. National Security Agency has figured out how to hide spying software deep within hard drives made by Western Digital, Seagate, Toshiba and other top manufacturers, giving the agency the means to eavesdrop on the majority of the world’s computers, according to cyber researchers and former operatives.
That long-sought and closely guarded ability was part of a cluster of spying programs discovered by Kaspersky Lab, the Moscow-based security software maker that has exposed a series of Western cyberespionage operations.
Kaspersky said it found personal computers in 30 countries infected with one or more of the spying programs, with the most infections seen in Iran, followed by Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. The targets included government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists, Kaspersky said. (reut.rs/1L5knm0)
The firm declined to publicly name the country behind the spying campaign, but said it was closely linked to Stuxnet, the NSA-led cyberweapon that was used to attack Iran’s uranium enrichment facility. The NSA is the agency responsible for gathering electronic intelligence on behalf of the United States.
A former NSA employee told Reuters that Kaspersky’s analysis was correct, and that people still in the intelligence agency valued these spying programs as highly as Stuxnet. Another former intelligence operative confirmed that the NSA had developed the prized technique of concealing spyware in hard drives, but said he did not know which spy efforts relied on it. [Continue reading…]
Snowden supporters can’t handle complexity
If Glenn Greenwald had more interest in investigation and less interest in being a celebrity, he could find no better tutor than Steven Aftergood — someone who most of Greenwald’s followers have most likely never heard of. Even so, Greenwald certainly understand what plays well with a large audience: a simple story.
Aftergood writes: For some of Edward Snowden’s partisans and supporters…, the possibility that his leaks had negative as well as positive consequences involves more complexity than they can tolerate. If Snowden intended to defend constitutional values, as he insists, then how dare anyone suggest that he may have also aided America’s enemies, even indirectly?
This sort of complexity does not arise in Laura Poitras’s award-winning film Citizenfour about Snowden, as its few critical reviewers have noted.
Many of the documents Snowden disclosed “go far beyond exposures of spying on Americans,” wrote Fred Kaplan in a review of the film in Slate. “If Snowden and company wanted to take down an intelligence agency, they should say so. But that has nothing to do with whistleblowing or constitutional rights.”
Likewise, wrote George Packer in The New Yorker, “Among the leaked documents are details of foreign-intelligence gathering that do not fall under the heading of unlawful threats to American democracy–what Snowden described as his only concern. [Former NSA official William] Binney, generally a fervent Snowden supporter, told USA Today that Snowden’s references to ‘hacking into China’ went too far: ‘So he is transitioning from whistle-blower to a traitor’.”
And from Michael Cohen in The Daily Beast: “What is left out of Poitras’s highly sympathetic portrayal of Snowden is so much of what we still don’t know about him. For example, why did he steal so many documents that have nothing to do with domestic surveillance but rather overseas–and legal–intelligence-gathering operations?”
But for a discussion of Citizenfour that presents no such dissonant, skeptical notes or troublesome opposing views, see the late David Carr’s final interview with Snowden, Poitras and Glenn Greenwald.
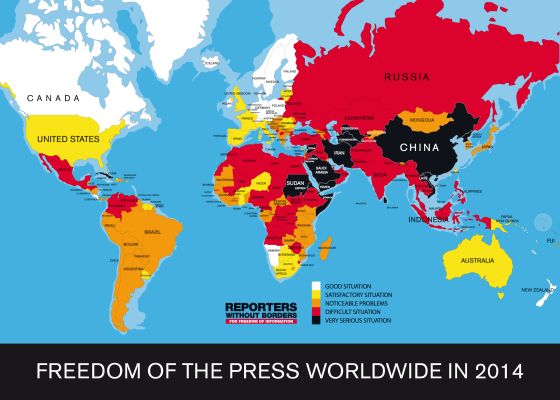
For me, one of the most memorable moments in that interview came when the participants scoffed at the United State’s poor ranking in the latest Borders Without Borders World Press Freedom Index.
At 46, the U.S. falls below countries such as Botswana — proximity which for Greenwald appeared to insult America’s reputation much more than it complimented Botswana.
While enjoying the freedom to speak from a stage in New York City (Greenwald’s fear of getting arrested in the U.S. seemed to disappear as soon as he got a Pulitzer and published his book), no mention was made of the fact that the country where Snowden resides ranks 148, while Greenwald’s home country of Brazil ranks 111.
No doubt, for as long as the U.S. retains the conceit of being “the leader of the free world,” it has little excuse for failing to rank number one in press freedom. At the same time, those who choose to characterize the U.S. government as the preeminent threat to personal freedom in the world, are either willfully ignoring or simply ignorant of much more egregious threats to freedom that can be seen in China, the Middle East, Russia and elsewhere.
Obama orders minor changes to surveillance on Americans and foreigners
The New York Times reports: A year after President Obama ordered modest changes in how the nation’s intelligence agencies collect and hold data on Americans and foreigners, the administration will announce new rules requiring intelligence analysts to delete private information they may incidentally collect about Americans that has no intelligence purpose, and to delete similar information about foreigners within five years.
The new rules to be announced Tuesday will also institutionalize a regular White House-led review of the National Security Agency’s monitoring of foreign leaders. Until the disclosures in the early summer of 2013 by Edward J. Snowden, the former N.S.A. contractor whose trove of intelligence documents is still leaking into public view, there was no continuing White House assessment of whether the intelligence garnered from listening to scores of leaders around the world was worth the potential embarrassment if the programs became public.
Mr. Obama publicly ordered the end of the monitoring of Chancellor Angela Merkel of Germany, saying he had known nothing about the effort — an admission that revealed the White House was not reviewing N.S.A. activities the way, for example, it annually reviews covert actions around the world by the C.I.A. The timing of the announcement about the new review process comes the week before Ms. Merkel is scheduled to visit the White House, where a long-debated arrangement for greater intelligence sharing between the countries is expected to be discussed.
Mr. Obama has never said whom, beyond Ms. Merkel, he took off the list of foreign leaders whose conversations are monitored, but it appeared that programs in Mexico and Brazil continued, while several dozen leaders have been removed. [Continue reading…]
NSA: Where more finds less
Mattathias Schwartz writes: Almost every major terrorist attack on Western soil in the past fifteen years has been committed by people who were already known to law enforcement. One of the gunmen in the attack on Charlie Hebdo, in Paris, had been sent to prison for recruiting jihadist fighters. The other had reportedly studied in Yemen with Umar Farouk Abdulmutallab, the underwear bomber, who was arrested and interrogated by the F.B.I. in 2009. The leader of the 7/7 London suicide bombings, in 2005, had been observed by British intelligence meeting with a suspected terrorist, though MI5 later said that the bombers were “not on our radar.” The men who planned the Mumbai attacks, in 2008, were under electronic surveillance by the United States, the United Kingdom, and India, and one had been an informant for the Drug Enforcement Administration. One of the brothers accused of bombing the Boston Marathon was the subject of an F.B.I. threat assessment and a warning from Russian intelligence.
In each of these cases, the authorities were not wanting for data. What they failed to do was appreciate the significance of the data they already had. [Continue reading…]
NSA on and off the trail of the Sony hackers
After cybersleuth Barack Obama saw the evidence pointing at North Korea’s responsibility for the cyberattacks against Sony, “he had no doubt,” the New York Times melodramatically reports.
He had no doubt about what? That his intelligence analysts knew what they were talking about? Or that he too when presented with the same evidence was forced to reach the same conclusion?
I have no doubt that had Obama been told by those same advisers that North Korea was not behind the attacks, he would have accepted that conclusion. In other words, on matters about which he lacks the expertise to reach any conclusion, he relies on the expertise of others.
A journalist who tells us about the president having “no doubt” in such as situation is merely dressing up his narrative with some Hollywood-style commander-in-chief gravitas.
When one of the reporters in this case, David Sanger, is someone whose cozy ties to government extend to being “an old friend of many, many years” of Ashton Carter, whose nomination as the next Secretary of Defense is almost certain to be approved, you have to wonder whose interests he really serves. Those of his readership or those of the government?
Since Obama and the FBI went out on a limb by asserting that they had no doubt about North Korea’s role in the attacks, they have been under considerable pressure to provide some compelling evidence to back up their claim.
That evidence now comes courtesy of anonymous officials briefing the New York Times and another document from the Snowden trove of NSA documents.
Maybe the evidence really is conclusive, but there are still important unanswered questions.
For instance, as Arik Hesseldahl asks:
why, if the NSA had so fully penetrated North Korea’s cyber operations, did it not warn Sony that an attack of this magnitude was underway, one that apparently began as early as September.
Officials with the NSA and the White House did not immediately respond to requests for comment about the report. A Sony spokeswoman had no comment.
On the one hand we’re being told that the U.S. knew exactly who was behind the Sony attacks because the hackers were under close surveillance by the NSA, and yet at the same time we’re being told that although the NSA was watching the hackers it didn’t figure out what they were doing.
If Hollywood everyone decides to create a satire out of this, they’ll need to come up with a modern-day reworking of the kind of scene that would come straight out of Get Smart — the kind where Maxwell Smart, Agent 86, would be eavesdropping on conversation between his North Korean counterparts, the only problem being, that he doesn’t understand Korean.
The Times report refers to the North Korean hackers using an “attack base” in Shenyang, in north east China. This has been widely reported with the somewhat less cyber-sexy name of the Chilbosan Hotel whose use for these purposes has been known since 2004.
If the attackers wanted to avoid detection, it’s hard to understand why they would have operated out of a location that had been known about for that long and that could so easily be linked to North Korea.
It’s also hard to fathom that having developed its cyberattack capabilities over such an extended period, North Korea would want to risk so much just to try and prevent the release of The Interview.
Michael Daly claims that the regime “recognizes that Hollywood and American popular culture in general constitute a dire threat” — a threat that has apparently penetrated the Hermit Kingdom in the “especially popular” form of Desperate Housewives.
Daly goes on to assert:
a glimpse of Wisteria Lane is enough to give lie to the regime’s propaganda that North Koreans live in a worker’s paradise while its enemies suffer in grinding poverty, driven by envy to plot against Dear Leader.
Of course, as every American who has watched the show knows, Wisteria Lane represents anytown America and the cast could blend in unnoticed at any Walmart or shopping mall.
OK. I won’t deny that American propaganda is much more sophisticated than North Korea’s, but when an American journalist implies that Desperate Housewives offers ordinary North Koreans a glimpse into the lives of ordinary Americans, you have to ask: which population has been more perfectly been brainwashed?
In reality, the dire threat to the North Korean regime in terms of social impact comes not from American popular culture but from much closer: South Korean soap operas.
Backlash in Berlin over NSA spying recedes as threat from ISIS rises
The Washington Post reports: In a crescendo of anger over American espionage, Germany expelled the CIA’s top operative, launched an investigation of the vast U.S. surveillance programs exposed by Edward Snowden and extracted an apology from President Obama for the years that U.S. spies had reportedly spent monitoring German Chancellor Angela Merkel’s cellphone.
In an address to Parliament last year, Merkel warned that U.S.-German cooperation would be curtailed and declared that “trust needs to be rebuilt.”
But the cooperation never really stopped. The public backlash over Snowden often obscured a more complicated reality for Germany and other aggrieved U.S. allies. They may be dismayed by the omnivorous nature of the intelligence apparatus the United States has built since the Sept. 11, 2001, attacks, but they are also deeply dependent on it.
Over the past year, Germany has secretly provided detailed information to U.S. spy services on hundreds of German citizens and legal residents suspected of having joined insurgent groups in Syria and Iraq, U.S. and German officials said.
Germany has done so reluctantly to enlist U.S. help in tracking departed fighters, determining whether they have joined al-Qaeda or the Islamic State and, perhaps most importantly, whether they might seek to bring those groups’ violent agendas back to Germany.
The stream of information includes names, cellphone numbers, e-mail addresses and other sensitive data that German security services — ever mindful of the abuses by the Nazi and Stasi secret police — have been reluctant even to collect, let alone turn over to a suspect ally. [Continue reading…]
Intelligence, defense whistleblowers remain mired in broken system
McClatchy reports: When Ilana Greenstein blew the whistle on mismanagement at the CIA, she tried to follow all the proper procedures.
First, she told her supervisors that she believed the agency had bungled its spying operations in Baghdad. Then, she wrote a letter to the director of the agency.
But the reaction from the intelligence agency she trusted was to suspend her clearance and order her to turn over her personal computers. The CIA then tried to get the Justice Department to open a criminal investigation of her.
Meanwhile, the agency’s inspector general, which is supposed to investigate whistleblower retaliation, never responded to her complaint about the treatment.
Based on her experience in 2007, Greenstein is not surprised that many CIA employees did little to raise alarms when the nation’s premier spy agency was torturing terrorism suspects and detaining them without legal justification. She and other whistleblowers say the reason is obvious.
“No one can trust the system,” said Greenstein, now a Washington attorney. “I trusted it and I was naive.”
Since 9/11, defense and intelligence whistleblowers such as Greenstein have served as America’s conscience in the war on terrorism. Their assertions go to the heart of government waste, misconduct and overreach: defective military equipment, prisoner abuse at Abu Ghraib, surveillance of Americans.
Yet the legal system that was set up to protect these employees has repeatedly failed those with the highest-profile claims. Many of them say they aren’t thanked but instead are punished for speaking out. [Continue reading…]
A dubious history of targeted killings in Afghanistan
Der Spiegel reports: Death is circling above Helmand Province on the morning of Feb. 7, 2011, in the form of a British Apache combat helicopter named “Ugly 50.” Its crew is searching for an Afghan named Mullah Niaz Mohammed. The pilot has orders to kill him.
The Afghan, who has been given the code name “Doody,” is a “mid-level commander” in the Taliban, according to a secret NATO list. The document lists enemy combatants the alliance has approved for targeted killings. “Doody” is number 3,673 on the list and NATO has assigned him a priority level of three on a scale of one to four. In other words, he isn’t particularly important within the Taliban leadership structure.
The operations center identified “Doody” at 10:17 a.m. But visibility is poor and the helicopter is forced to circle another time. Then the gunner fires a “Hellfire” missile. But he has lost sight of the mullah during the maneuver, and the missile strikes a man and his child instead. The boy is killed instantly and the father is severely wounded. When the pilot realizes that the wrong man has been targeted, he fires 100 rounds at “Doody” with his 30-mm gun, critically injuring the mullah.
The child and his father are two of the many victims of the dirty secret operations that NATO conducted for years in Afghanistan. Their fate is described in secret documents to which SPIEGEL was given access. Some of the documents concerning the International Security Assistance Force (ISAF) and the NSA and GCHQ intelligence services are from the archive of whistleblower Edward Snowden. Included is the first known complete list of the Western alliance’s “targeted killings” in Afghanistan. The documents show that the deadly missions were not just viewed as a last resort to prevent attacks, but were in fact part of everyday life in the guerilla war in Afghanistan. [Continue reading…]
In 2008 Mumbai attacks, piles of spy data, but an uncompleted puzzle
Sebastian Rotella, James Glanz and David E. Sanger report: In the fall of 2008, a 30-year-old computer expert named Zarrar Shah roamed from outposts in the northern mountains of Pakistan to safe houses near the Arabian Sea, plotting mayhem in Mumbai, India’s commercial gem.
Mr. Shah, the technology chief of Lashkar-e-Taiba, the Pakistani terror group, and fellow conspirators used Google Earth to show militants the routes to their targets in the city. He set up an Internet phone system to disguise his location by routing his calls through New Jersey. Shortly before an assault that would kill 166 people, including six Americans, Mr. Shah searched online for a Jewish hostel and two luxury hotels, all sites of the eventual carnage.
But he did not know that by September, the British were spying on many of his online activities, tracking his Internet searches and messages, according to former American and Indian officials and classified documents disclosed by Edward J. Snowden, the former National Security Agency contractor.
They were not the only spies watching. Mr. Shah drew similar scrutiny from an Indian intelligence agency, according to a former official who was briefed on the operation. The United States was unaware of the two agencies’ efforts, American officials say, but had picked up signs of a plot through other electronic and human sources, and warned Indian security officials several times in the months before the attack.
What happened next may rank among the most devastating near-misses in the history of spycraft. The intelligence agencies of the three nations did not pull together all the strands gathered by their high-tech surveillance and other tools, which might have allowed them to disrupt a terror strike so scarring that it is often called India’s 9/11.
“No one put together the whole picture,” said Shivshankar Menon, who was India’s foreign secretary at the time of the attacks and later became the national security adviser. “Not the Americans, not the Brits, not the Indians.” [Continue reading…]
How the NSA hacks cellphone networks worldwide
Ryan Gallagher reports: In March 2011, two weeks before the Western intervention in Libya, a secret message was delivered to the National Security Agency. An intelligence unit within the U.S. military’s Africa Command needed help to hack into Libya’s cellphone networks and monitor text messages.
For the NSA, the task was easy. The agency had already obtained technical information about the cellphone carriers’ internal systems by spying on documents sent among company employees, and these details would provide the perfect blueprint to help the military break into the networks.
The NSA’s assistance in the Libya operation, however, was not an isolated case. It was part of a much larger surveillance program—global in its scope and ramifications—targeted not just at hostile countries. [Continue reading…]
INCENSER, or how NSA and GCHQ are tapping internet cables
Peter Koop writes: Documents recently disclosed by Edward Snowden show that the NSA’s fourth-largest cable tapping program, codenamed INCENSER, pulls its data from just one single source: a submarine fiber optic cable linking Asia with Europe.
Until now, it was only known that INCENSER was a sub-program of WINDSTOP and that it collected some 14 billion pieces of internet data a month. The latest revelations now say that these data are collected with the help of the British company Cable & Wireless (codenamed GERONTIC, now part of Vodafone) at a location in Cornwall in the UK, codenamed NIGELLA.
For the first time, this gives us a view on the whole interception chain, from the parent program all the way down to the physical interception facility. Here we will piece together what is known about these different stages and programs from recent and earlier publications. [Continue reading…]