This 2016 short documentary by Alex Gibney is based on a 2006 article, “The Agent,” by Lawrence Wright.
Category Archives: Department of Justice
If the FBI concerns us, Apple should concern us even more

Ned O’Gorman writes: whatever privacy is, it has to be in Apple’s eye primarily an engineering problem. Apple’s privacy is an engineer’s construct, even conceit. Many everyday senses of privacy follow this very limited idea of “data on my device.” Though I’ve entered vital data online numerous times, I would be more likely to feel a violation of privacy at an “unauthorized” family member thumbing through the pictures on my phone than a stranger using my date of birth and social security number to secure fraudulent credit. There’s something about Apple’s sense of “personal data” that gels very well with our sense that the gadgets we carry with us are “personal devices” rather than nodes in a massive economic and technological system.
But what about privacy’s co-dependents, especially the “public”? Apple’s narrow and problematic sense of privacy, if Apple sticks to it and if it were made the rule among tech companies, could have major public consequences, reshaping our experience of public life. First of all, Apple is explicitly pitting a forensic good, a good having to do with public justice, against the protection of privacy, and it is doing so in an absolutist fashion that undermines the delicate balance between certain rights and justice so vital to public life (just as the NSA did, but in reverse fashion).
In the case of Syed Rizwan Farook’s iPhone, we are talking about a specific and targeted forensic investigation — exactly what critics of the NSA call for. It is quite plausible that the data on Farook’s phone may be critical in helping to forensically reconstruct the networks (if any) of which Farook was a part. The knowledge that would come out of such an investigation may not end up preventing another similar attack. Nevertheless, it represents an immediate public good both with respect to our sense of justice and to making sense of indiscriminate acts of political violence that are, in their very performance, meant to cripple or otherwise alarm the citizenry. My point here is simply that legally sanctioned and legitimate forensic police work represents a public good, and Apple is now pitting that good against the good of privacy — and privacy as Apple defines it. [Continue reading…]
Apple vs. FBI: ‘Just this once’?
Julian Sanchez writes: Loudly as the Justice Department protests that this dispute is simply about one particular phone, that’s fairly clearly not the case. Forget other even more dangerous ways Apple could be compelled to use their private key and let’s stay focused on breaking iPhones for the moment. The Manhattan DA’s office alone has at least 175 iPhones that they’d like Apple to help them break into, and DOJ itself has 12 other ongoing lawsuits seeking access to iPhones. Realistically, if Apple loses here — and especially if they lose at the appellate level, which is where this is likely going given Apple’s decision to hire superstar lawyer Ted Olson for the case — they’re going to be fielding thousands of similar demands every year. As a practical matter, they’re going to need a dedicated team dedicated to developing, debugging, testing, customizing, and deploying the code used to brute force passcodes.
Now, when it comes to the Holy Grail of Apple’s security infrastructure — the private key — it’s almost certainly stored in secure vaults, on a Hardware Security Module that makes it difficult or impossible to copy the key itself off that dedicated hardware, and likely protected by elaborate procedures that have to be followed to authenticate major new software releases. If your adversaries realistically include, say, the Chinese and Russian intelligence services — and for Apple, you’d better believe it — it’s a serious enough security problem to guard against exfiltration or use of that Holy Grail private key. Doing the same for a continuously updated and deployed hacking tool is likely to be hugely more difficult. As the company explains:
Apple would do our best to protect that key, but in a world where all of our data is under constant threat, it would be relentlessly attacked by hackers and cybercriminals. As recent attacks on the IRS systems and countless other data breaches have shown, no one is immune to cyberattacks.
The Justice Department might not intend to “set a master key loose on the land” — but the predictable consequence of mandating compliance with requests of this type will be to significantly increase the chance of exactly that occurring. And that’s an increased risk that every individual or enterprise customer relying on iOS devices to secure critical data will need to take into account. [Continue reading…]
Ex-NSA chief opposes government effort to require ‘back doors’ in all devices
USA Today reports: Retired four-star general Michael Hayden, who as director of the NSA installed and still defends the controversial surveillance program to collect telephone metadata on millions of Americans, says he opposes proposals to force Apple and other tech companies to install “back doors” in digital devices to help law enforcement.
In an emerging court battle over access to information on the iPhone owned by one of the San Bernardino attackers, Hayden says “the burden of proof is on Apple” to show that limited cooperation with investigators would open the door to broader privacy invasions. Apple is being asked not to decrypt information on the smartphone but rather to override the operating system so investigators could try an endless series of passwords to unlock it.
“In this specific case, I’m trending toward the government, but I’ve got to tell you in general I oppose the government’s effort, personified by FBI Director Jim Comey,” Hayden told Capital Download in an interview about his memoir, Playing to the Edge: American Intelligence in the Age of Terror. “Jim would like a back door available to American law enforcement in all devices globally. And, frankly, I think on balance that actually harms American safety and security, even though it might make Jim’s job a bit easier in some specific circumstances.”[Continue reading…]
The technical reasons the FBI’s claim, ‘just this one phone,’ is bogus
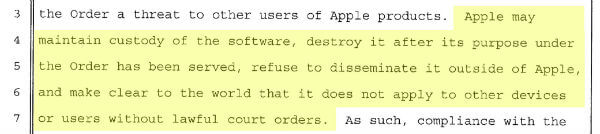
Jonathan Zdziarski, an expert in iOS forensics, writes: For years, the government could come to Apple with a subpoena and a phone, and have the manufacturer provide a disk image of the device. This largely worked because Apple didn’t have to hack into their phones to do this. Up until iOS 8, the encryption Apple chose to use in their design was easily reversible when you had code execution on the phone (which Apple does). So all through iOS 7, Apple only needed to insert the key into the safe and provide FBI with a copy of the data.
This service worked like a “black box”, and while Apple may have needed to explain their methods in court at some point, they were more likely considered a neutral third party lab as most forensics companies would be if you sent them a DNA sample. The level of validation and accountability here is relatively low, and methods can often be opaque; that is, Apple could simply claim that the tech involved was a trade secret, and gotten off without much more than an explanation. An engineer at Apple could hack up a quick and dirty tool to dump disk, and nobody would need to ever see it because they were providing a lab service and were considered more or less trade secrets.
Now lets contrast that history with what FBI and the courts are ordering Apple to do here. FBI could have come to Apple with a court order stating they must brute force the PIN on the phone and deliver the contents. It would have been difficult to get a judge to sign off on that, since this quite boldly exceeds the notion of “reasonable assistance” to hack into your own devices. No, to slide this by, FBI was more clever. They requested that Apple developed a forensics tool but did not do the actual brute force themselves. [Continue reading…]
The archaic All Writs Act the government is using to try and unlock a terrorist’s iPhone
The Washington Post reports: The U.S. government and Apple are locked in a legal battle over unlocking an iPhone used by one of the San Bernardino shooters. But a new court order is throwing a law that dates to the days of the founding fathers into a high-tech debate over digital security.
On Tuesday, a U.S. magistrate judge in California ordered Apple to provide “reasonable technical assistance” to the government as it tries to bypass security features built into its products based on an interpretation of the “All Writs Act.”
The original form of that statute dates to the Judiciary Act of 1789, centuries before the iPhone was a twinkle in Steve Jobs’s eye. In its current form, the law gives federal courts the power to “issue all writs necessary or appropriate in aid of their respective jurisdictions and agreeable to the usages and principles of law.”
Basically, it’s “a very short, cryptic statute” that gives the courts “all sorts of incidental powers” to require things not specifically covered by other laws, according to Stephen Vladeck, a law professor at American University.
In the past, the act has been used to compel non-parties — like service providers of tech companies — to help in criminal investigations, Vladeck said. But that help has typically been limited to straightforward requests, like activating or turning off particular features and using systems that are already in place, he said.
The new order is different: It tells Apple to help the government by creating an entirely new software to help investigators bypasses security features. “That requires Apple to go much further than any company has ever been required to go in one of these cases,” said Vladeck. [Continue reading…]
Last October, Jennifer Granick and Riana Pfefferkorn wrote: Under the government’s interpretation of the All Writs Act, anyone who makes software could be dragooned into assisting the government in investigating users of the software. If the court adopts this view, it would give investigators immense power. The quotidian aspects of our lives increasingly involve software (from our cars to our TVs to our health to our home appliances), and most of that software is arguably licensed, not bought. Conscripting software makers to collect information on us would afford the government access to the most intimate information about us, on the strength of some words in some license agreements that people never read. (And no wonder: The iPhone’s EULA came to over 300 pages when the government filed it as an exhibit to its brief.)
The government’s brief does not acknowledge the sweeping implications of its arguments. It tries to portray its requested unlocking order as narrow and modest, because it “would not require Apple to make any changes to its software or hardware, … [or] to introduce any new ability to access data on its phones. It would simply require Apple to use its existing capability to bypass the passcode on a passcode-locked iOS 7 phone[.]” But that undersells the implications of the legal argument the government is making: that anything a company already can do, it could be compelled to do under the All Writs Act in order to assist law enforcement. [Continue reading…]
How a New York judge inspired Apple’s encryption fight
Reuters reports: Last October, prosecutors from the Justice Department asked a federal magistrate judge in Brooklyn to issue an order directing Apple to help the Drug Enforcement Administration bust security on an iPhone 5 seized from the home of Jun Feng, a suspected meth dealer.
The government had previously obtained many such orders against Apple and other companies under the All Writs Act, a 1789 statute that grants federal courts broad power to issue “necessary or appropriate” writs.
The act has been a powerful tool for prosecutors since 1977, when the U.S. Supreme Court ruled in U.S. v. New York Telephone that the All Writs Act extends, under certain conditions, to private companies in a position to assist “the proper administration of justice.”
Apple has a long history of compliance with All Writs Act orders. The company helped New York investigators extract data from a suspected child sex abuser’s iPhone in 2008; rushed a data extraction in 2013 from the phone of an alleged child pornographer in Washington; and in 2015 provided federal agents in Florida with data the company extracted from a drug suspect’s phone.
According to a Justice Department brief filed last fall, Apple never objected to All Writs Act orders in those cases – nor, for that matter, to any All Writs Act order directing the company to help federal investigators break into iPhones.
Apple’s policy of acquiescence abruptly changed in the Jun Feng case last year. And for all of the attention now focused on Apple’s announced opposition to a newly issued All Writs Act order directing the company to help Justice Department investigators break the passcode on an iPhone belonging to San Bernardino shooter Syed Farook, the Feng case is quite likely to produce a ruling before the Farook case.
The impending showdown over Farook’s phone is an irresistibly stark depiction of the competing interests of individual privacy and national security. But keep your eye on precedent from Feng. [Continue reading…]
FBI’s push to ‘fix a typo’ would really expand its surveillance authority
Robyn Greene writes: At last week’s Senate Intelligence Committee hearing on Worldwide Threats, FBI Director James Comey reiterated his call for a major expansion of the FBI’s surveillance authorities, but disingenuously downplayed it as fixing a “typo” in the law. In fact, Comey’s proposed fix, which he calls one of the FBI’s top legislative priorities, would be a major expansion of surveillance authority, and a major hit to Americans’ privacy and civil liberties. It would grant the FBI access to a range of revealing and personal details about Americans’ online communications — what are called Electronic Communications Transactional Records (ECTR), in legalese — without court approval.
Through Comey’s “ECTR fix,” the FBI would have the unilateral authority to obtain information from phone and Internet companies about your online communications such as logs of emails you send and receive, cell site data (including your location information), and lists of websites you visit. The FBI wants to get this information using National Security Letters (NSLs), which are demands for information issued directly by local FBI offices without any court approval or supervision.
Under current law, the FBI can only use NSLs to get information pertaining to a customer’s “name, address, length of service, and local and long distance toll billing records of a person or entity.” By contrast, if the FBI wants to compel a company to hand over the much more revealing private information that is included in ECTRs, they currently can’t use NSLs — instead, they have to get a court order after convincing a judge that they have a factual basis for demanding those records. Therefore, the FBI’s proposal that Congress add ECTRs to the NSL statute is far from a typo fix, and would instead be a major expansion of FBI’s authority to conduct surveillance with virtually no oversight and no accountability. [Continue reading…]
Apple’s stance highlights a more confrontational tech industry
Farhad Manjoo writes: The battle between Apple and law enforcement officials over unlocking a terrorist’s smartphone is the culmination of a slow turning of the tables between the technology industry and the United States government.
After revelations by the former National Security Agency contractor Edward J. Snowden in 2013 that the government both cozied up to certain tech companies and hacked into others to gain access to private data on an enormous scale, tech giants began to recognize the United States government as a hostile actor.
But if the confrontation has crystallized in this latest battle, it may already be heading toward a predictable conclusion: In the long run, the tech companies are destined to emerge victorious.
It may not seem that way at the moment. On the one side, you have the United States government’s mighty legal and security apparatus fighting for data of the most sympathetic sort: the secrets buried in a dead mass murderer’s phone. The action stems from a federal court order issued on Tuesday requiring Apple to help the F.B.I. unlock an iPhone used by one of the two attackers who killed 14 people in San Bernardino, Calif., in December.
In the other corner is the world’s most valuable company, whose chief executive, Timothy D. Cook, has said he will appeal the court’s order. Apple argues that it is fighting to preserve a principle that most of us who are addicted to our smartphones can defend: Weaken a single iPhone so that its contents can be viewed by the American government and you risk weakening all iPhones for any government intruder, anywhere.
There will probably be months of legal tussling, and it is not at all clear which side will prevail in court, nor in the battle for public opinion and legislative favor.
Yet underlying all of this is a simple dynamic: Apple, Google, Facebook and other companies hold most of the cards in this confrontation. They have our data, and their businesses depend on the global public’s collective belief that they will do everything they can to protect that data. [Continue reading…]
Apple encryption case risks influencing Russia and China, privacy experts say
The Guardian reports: Authoritarian governments including Russia and China will demand greater access to mobile data should Apple lose a watershed encryption case brought by the FBI, leading technology analysts, privacy experts and legislators have warned.
Apple’s decision to resist a court order to unlock a password-protected iPhone belonging to one of the San Bernardino killers has created a worldwide privacy shockwave, with campaigners around the world expecting the struggle to carry major implications for the future of mobile and internet security. They warned that Barack Obama’s criticism of a similar Chinese measure last year now risked ringing hollow.
Senator Ron Wyden of Oregon, a leading legislator on privacy and tech issues, warned the FBI to step back from the brink or risk setting a precedent for authoritarian countries.
“This move by the FBI could snowball around the world. Why in the world would our government want to give repressive regimes in Russia and China a blueprint for forcing American companies to create a backdoor?” Wyden told the Guardian.
“Companies should comply with warrants to the extent they are able to do so, but no company should be forced to deliberately weaken its products. In the long run, the real losers will be Americans’ online safety and security.” [Continue reading…]
Warnings about risks posed by encryption have been wildly overblown by intelligence agencies, says report

The New York Times reports: For more than two years the F.B.I. and intelligence agencies have warned that encrypted communications are creating a “going dark” crisis that will keep them from tracking terrorists and kidnappers.
Now, a study in which current and former intelligence officials participated concludes that the warning is wildly overblown, and that a raft of new technologies — like television sets with microphones and web-connected cars — are creating ample opportunities for the government to track suspects, many of them worrying.
“ ‘Going dark’ does not aptly describe the long-term landscape for government surveillance,” concludes the study, to be published Monday by the Berkman Center for Internet and Society at Harvard.
The study argues that the phrase ignores the flood of new technologies “being packed with sensors and wireless connectivity” that are expected to become the subject of court orders and subpoenas, and are already the target of the National Security Agency as it places “implants” into networks around the world to monitor communications abroad. [Continue reading…]
How the FBI is pressuring Muslim immigrants to become informants

BuzzFeed reports: When he got the last call to come meet with the FBI agents, A.M. allowed himself an uncharacteristic bit of optimism. An immigrant from Pakistan, he had spent the last seven years trying to get a green card, a process that had so far included a series of interviews, three encounters with the FBI, and unexplained bureaucratic delays. Maybe this meeting would bring some resolution?
But when the 37-year-old software programmer arrived at the Homeland Security offices in Dallas that day in August 2014, the conversation quickly swerved. One of the two agents placed a piece of paper on the table and told him to write down the names of all the people he knew who he thought were terrorists.Bewildered, he said he didn’t know any terrorists. He said he didn’t know about any suspicious activity at all. “We think you do,” the agents replied.
A.M. was quickly becoming alarmed. (Like almost all other immigrants interviewed for this story, he said he did not feel safe allowing his name to be published. A.M. are his initials.) He was a family man, with a highly skilled 9-to-5 job. He had lived in America for nearly two decades. He went to college in America. Why would the FBI see him as a link to terrorism? And weren’t they supposed to be discussing his green card application?
As it turned out, that’s precisely what they were discussing. “We know about your immigration problems,” he recalls one of the agents telling him. “And we can help you with that.” If, they said, he agreed to start making secret reports on his community, his friends, even his family.Pressuring people to become informants by dangling the promise of citizenship — or, if they do not comply, deportation — is expressly against the rules that govern FBI agents’ activities.
Attorney General Alberto Gonzales forbade the practice nine years ago: “No promises or commitments can be made, except by the United States Department of Homeland Security, regarding the alien status of any person or the right of any person to enter or remain in the United States,” according to the Attorney General’s Guidelines Regarding the Use of FBI Confidential Human Sources.
In fact, Gonzales’s guidelines, which are still in force today, require agents to go further: They must explicitly warn potential informants that the FBI cannot help with their immigration status in any way.
But a BuzzFeed News investigation — based on government and court documents, official complaints, and interviews with immigrants, immigration and civil rights lawyers, and former special agents — shows that the FBI violates these rules. Mandated to enforce the law, the bureau has assumed a powerful but unacknowledged role in a very different realm: decisions about the legal status of immigrants — in particular, Muslim immigrants. First the immigration agency ties up their green card applications for years, even a decade, without explanation, then FBI agents approach the applicants with a loaded offer: Want to get your papers? Start reporting to us about people you know. [Continue reading…]
Suspect in pro-ISIS plot called mentally ill ‘panhandler’ who was ‘manipulated’
The Associated Press reports: An ex-convict arrested in a plot to carry out a pro-Islamic State attack at a bar on New Year’s Eve is a panhandler who had been asked to leave in the past, the bar’s owner said. The man’s family said he had a long history of mental problems.
Federal authorities have said Emanuel Lutchman, 25, sought to prove he was worthy of joining Isis by leading an attack in Rochester with a machete and knives that were provided by an FBI informant.
After authorities announced his arrest on Thursday, Lutchman’s father and mother described a man who had had psychiatric troubles since childhood, had recently stabbed himself in a suicide attempt and, they said, would not have conducted the attack on his own.
“The boy is impressionable,” his father, Omar Lutchman, told NBC News. “First he was a Blood, then he was a Crip, then he became a Muslim. He’s easily manipulated.”
The father and the suspect’s grandmother, Beverley Carridice-Henry, told the network Lutchman is married and has a two-year-old son but had been having marital and money problems. He was frustrated over being unable to find work and care for his family, they said. [Continue reading…]
FBI listed It’s a Wonderful Life as suspected Communist propaganda
Quartz reports: It’s a Wonderful Life is a staple of the holiday season in the United States, but it was once considered un-American by the government.
From the film’s release in 1946 until 1956, it was listed by the Federal Bureau of Investigation as suspected Communist propaganda. Mr. Potter, the villainous banker who nearly drives George Bailey to financial ruin and suicide, “represented a rather obvious attempt to discredit bankers by casting Lionel Barrymore as ‘scrooge-type’ so that he would be the most hated man in the picture,” according to an FBI report (pdf, pg. 14) in 1947.
The report called it “a common trick used by Communists.” [Continue reading…]
Pete Seeger’s FBI file reveals how the folk legend first became a target of the feds
David Corn writes: From the 1940s through the early 1970s, the US government spied on singer-songwriter Pete Seeger because of his political views and associations. According to documents in Seeger’s extensive FBI file—which runs to nearly 1,800 pages (with 90 pages withheld) and was obtained by Mother Jones under the Freedom of Information Act—the bureau’s initial interest in Seeger was triggered in 1943 after Seeger, as an Army private, wrote a letter protesting a proposal to deport all Japanese American citizens and residents when World War II ended.
Seeger, a champion of folk music and progressive causes—and the writer, performer, or promoter of now-classic songs, including as “If I Had a Hammer,” “Where Have All the Flowers Gone?,” Turn! Turn! Turn!,” “Kisses Sweeter Than Wine,” “Goodnight, Irene,” and “This Land Is Your Land”—was a member of the Communist Party for several years in the 1940s, as he subsequently acknowledged. (He later said he should have left earlier.) His FBI file shows that Seeger, who died in early 2014, was for decades hounded by the FBI, which kept trying to tie him to the Communist Party, and the first investigation in the file illustrates the absurd excesses of the paranoid security establishment of that era. [Continue reading…]
Climate advocates to Department of Justice: It’s time to prosecute Exxon
Good reports: Members of Congress, presidential candidates, and now at least 350,000 American citizens are calling upon U.S. Attorney General Loretta Lynch to investigate and prosecute Exxon Mobil for intentionally deceiving the public about the science of climate change.
In September, two exclusive investigative reports by the Los Angeles Times and Inside Climate News, revealed that Exxon’s own scientists were researching climate change, even as the company was spending big money to misinform the public about climate science. The Inside Climate News investigation found that as early as 1977, Exxon’s own scientists were warning management about oil’s role in “potentially catastrophic” global warming.
Many climate advocates – including a growing number of politicians – believe that the deception could well be criminal. Last Thursday, representatives from a number of climate advocacy group – including Climate Hawks Vote, 350.org, the Moms Clean Air Force, the Working Families Party, and Greenpeace USA – delivered over 350,000 signed petitions to the Department of Justice demanding an investigation. [Continue reading…]
FBI to help Russia investigate plane crash in Egypt
The New York Times reports: The F.B.I. has agreed to help the Russian government with its investigation into the deadly crash of a Russian charter plane in the Sinai Peninsula in Egypt, senior American officials said on Saturday.
Some American officials said that the Russians want help doing a forensic analysis to determine what brought down the Airbus A321-200, while other officials said that the request from the Russians was more general. Although most of the debris is scattered over nearly eight square miles in the desert, some parts of the plane were taken to Russia for analysis.
It is rare for the Russians to make such a request, which was first reported on Friday by CBS News, and some American officials interpreted it as a sign of the challenges facing investigators. [Continue reading…]
The New York Times reports: Russian officials said Saturday that more than 70,000 of their citizens were in Egypt awaiting the arrival of jets being sent to carry them home. British officials said on Saturday that there were about 19,000 Britons at Sharm el Sheikh and that it would take 10 days to get them all home.
The exodus from Sharm el Sheikh has dealt a devastating blow to Egypt’s already sputtering tourism industry. The loss of foreign currency from tourists is likely to greatly increase downward pressure on the value of the Egyptian pound, compounding the damage to the broader economy.
Only a small number of Western European airlines operated direct flights to Sharm el Sheikh before the crash, flying from Britain, Belgium, Germany, Italy and Switzerland. Airlines from some countries, including France and the Netherlands, stopped offering direct service in recent years, in part out of security concerns, European officials said. [Continue reading…]
Global reaction to Egyptian plane crash a real test for Sisi – he received no such censure over Rabaa massacre, which killed 1000+ people.
— Louisa Loveluck (@leloveluck) November 6, 2015
The New York Times reports: Six days after the crash of a Russian charter flight from the Egyptian resort area of Sharm el Sheikh, the government of Egypt is finding itself increasingly isolated in its resistance to the possibility that a terrorist’s bomb brought down the plane.
Britain has concluded the cause was most likely a bomb. President Obama has said pointedly that he takes the possibility “very seriously.” After standing arm in arm with Egypt for six days in discouraging any such discussion of terrorism, even President Vladimir V. Putin on Friday suspended Russia’s flights to Egypt for fear of another attack, stranding tens of thousands of tourists at the resort.
But the government of Egypt, critically dependent on the money tourists bring to Sharm el Sheikh’s resorts, has dismissed any suggestion that a bombing killed the 224 people aboard as “premature,” “surprising” and “unwarranted.”
The widening chasm between Egypt and the world, some say, recalls an earlier crash, in 1999, when EgyptAir Flight 990 plunged into the ocean off the coast of Nantucket Island. Although American investigators said flight records pointed to the decisions of an Egyptian pilot, the Egyptian government blamed a malfunction in the Boeing airplane, and 17 years later the Egyptian-American dispute over the cause is still unresolved.
In that case, the Egyptian investigation was cloaked in mystery and, critics say, politicized from that start.
“I don’t anticipate the Egyptian investigation here to be any more transparent than their work on EgyptAir 990,” James E. Hall, the former head of the National Transportation Safety Board who oversaw that investigation, said in an interview. [Continue reading…]
How U.S. officials can kidnap and threaten American citizens without legal risk
Patrick G. Eddington writes: At exactly 5 p.m. on March 13, 2007, just as I was preparing to leave my cubicle in Washington for the day, I got a phone call from the journalist Jonathan Landay of McClatchy Newspapers. To this day, I remember his exact words.
“One of your congressman’s constituents is being held in an Ethiopian intelligence service prison, and I think your former employer is neck-deep in this.”
The congressman was Rush Holt, then a Democratic representative from New Jersey, for whom I worked for 10 years starting in 2004. The constituent was Amir Mohamed Meshal of Tinton Falls, N.J., who alleges that he was illegally taken to Ethiopia, where he was threatened with torture by American officials. My “former employer” was the Central Intelligence Agency, but it soon became apparent that the agency “neck-deep in this” was the Federal Bureau of Investigation.
Eight years after Mr. Meshal’s rendition, his case ended up before a three-judge panel of the United States Court of Appeals for the District of Columbia. The questions hanging over the proceeding were: can the United States government allow, or even facilitate, the rendition of an American citizen to another country for interrogation? And can United States officials themselves conduct rendition and interrogations of American citizens, including threats of torture, on foreign soil?
According to a decision handed down last week, the answers appear to be yes. [Continue reading…]
