
David Sanger
Even while the
New York Times prides itself as a pillar of the American establishment, it generally tries to maintain at least a facade of independence from the U.S. government. It’s journalists generally enjoy higher levels and easier forms of access to administration officials than most other journalists and yet that access supposedly adds depth to their reporter rather than simply making them the dutiful mouthpieces of government.
But imagine this: Imagine if the Times’ chief Washington correspondent, David Sanger, was to begin a report like this:
I was talking to Ash Carter, deputy secretary of defense, an old friend of many, many years — I won’t say how many — and he tells me the NSA…
Well, before we even learned whatever gems of information Carter might have shared with his buddy, we’d have good reason to wonder whether Sanger was acting as a reporter or whether he might be doing his old friend a favor.
In “N.S.A. Imposes Rules to Protect Secret Data Stored on Its Networks,” Sanger reported on information he had gathered from Carter the day before at the Aspen Security Forum. But the New York Times reporter wasn’t there, notebook in hand, listening to briefings from Pentagon officials. It was Sanger acting as host who said:
It’s wonderful to be here with Ash Carter, deputy secretary of defense, an old friend of many, many years — I won’t say how many…
In his report, Sanger wrote:
Ashton B. Carter, the deputy secretary of defense, said the conditions that allowed Mr. Snowden to download and remove data without detection amounted to “a failure to defend our own networks.”
“It was not an outsider hacking in, but an insider,” he said.
This is another iteration of the meme that the administration has been disseminating: Edward Snowden is not a whistleblower; he’s a hacker.
The image that administration officials are trying to spread is of Snowden as essentially operating like a burglar — a low-level technician who pilfered classified information that he had no authority to access.
So far, there has been no reporting that substantiates this view. In fact, as an infrastructure analyst (not a systems administrator, as he is often described), it seems most likely that Snowden was fully authorized to examine all the documents that he later chose to leak.
Indeed, in his conversation with Sanger, Carter confirms that with Snowden “you had an individual who was given very substantial authority to access that information…”
Clearly, this is not a story about hacking, yet Sanger chose not to quote that part of his friend’s statement.
The main thrust of Sanger’s report — pushing the line that he had been spoon-fed by Carter and NSA chief Keith Alexander — is that Snowden’s leaks have made the work of the NSA more difficult. Subtext: if there’s another terrorist attack, blame Snowden.
And Sanger reports that the NSA has been forced to impose new rules such as the “two-man rule” derived from the safeguards on handling nuclear weapons. When it comes to nuclear weapons, Carter says, “You don’t let people all by themselves do anything.” So how’s that apply to the NSA? Is this a pitch to double the agency’s size?
Sanger’s explanation of the two-man rule is that it “requires two computer systems administrators to work simultaneously when they are inside systems that contain highly classified material.” It sounds like if the agency as a whole is not about to double it size, then they will at least need to hire lots of new systems administrators.
A search of the NSA’s current career openings does not actually show any positions available to systems administrators.
Here’s a transcript of the segment of the Sanger-Carter conversation that related to Snowden:
Sanger: After Wikileaks happened, and I was involved in some of the Times coverage on it so I recall this pretty distinctly, we were asking a lot of people the question: how could you download 250,000 documents from the State Department and no alarms going off? And my recollection is that your old boss Bob Gates asked that question both publicly and privately pretty vividly.
Then Mr Snowden comes along and it wasn’t 250,000 documents but it was certainly documents of a higher level of sensitivity than what was in Wikileaks. So, tell us first as you’ve looked at it, what you think happened — why that was able to happen — and secondly, since you mentioned before the importance of defending your own networks, how you’re changing your practices, or plan to change your practices going forward. And maybe make an assessment of how much damage, if any, was done.
Carter: Well, we are assessing the damage and I can just tell you right now, the damage is very substantial — and I won’t get into Snowden himself, because that’s a criminal investigation involved where I can’t talk about that.
But to the issue, it gets back to what I said: job one for us has to be defending our own networks. And this is a failure to defend our own networks. And it’s not an outsider hacking, it was an insider. And everybody who has networks knows that the insider threat is an enormous one.
This failure originated from two practices that we need to reverse. The first is that, in an effort for those in the intelligence community to be able to share information with one another, there was an enormous amount of information concentrated in one place. That’s a mistake.
We normally compartmentalize information for the very good reason so that one person can’t compromise a lot. Loading everything onto a server by people each cleared in their own compartment — but loading onto a server creates a security risk of decompartmentalization. That’s thing one —
Sanger: — But that wasn’t a surprise to anybody, people said that as they were doing it…
Carter: — I don’t know who it was a surprise to — it wasn’t a surprise to me, but it’s something we can’t do because it creates a — too much information in one place.
The second thing is you had an individual who was given very substantial authority to access that information and move that information. That ought’n to be the case either.
So, we’re acting to reverse both of those things. It’s quite clear that those were the two root causes of this.
Now what do you have to do about that? You do have to compartmentalize more rigidly and you have to have a system which I would liken to our longstanding system for handling nuclear weapons.
You know we have no-loan zones. We have two-man rule. You go out Barksdale and walk around the apron and you’ll see a red line, and it says: you cross that red line and you can get shot, because there are areas where you are simply not to be because proximity to nuclear weapons is too sensitive and momentous a thing to be allowed for individuals, because there’s always some aberrant individual, where you’ve got to recognize that fact.
So when it comes to nuclear weapons we give special — we watch people’s behavior in a special way. You don’t let people all by themselves do anything. Nobody ever touches a nuclear weapon by him or herself. There are always two people rated in the same specialty. So everybody can see and understand exactly what is being done to that weapon. It’s been that way for decades.
Here we had the case where we had a single person at one installation in the intelligence community, could have access to and moreover move that much information.
Both of those pieces are a mistake and have to be corrected.
As for Carter’s observation about red lines and the people who transgress them getting shot, is this the Obama administration’s latest threat to whistleblowers — that they now risk being shot on sight?

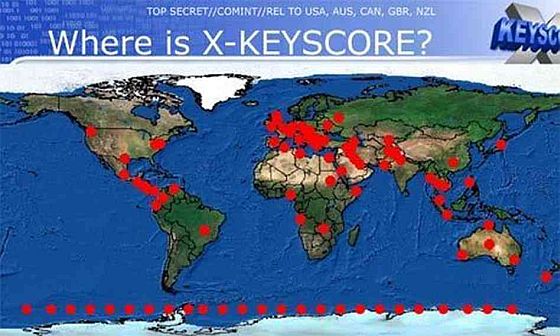




 Shortly after 9/11, Osama bin Laden appeared on the cover of Time magazine. What later became an iconic image — the embodiment of evil, global terrorist #1, the face of Islamic extremism, or however else Americans came to view this face — did at the time show a man with an indisputable look of serenity.
Shortly after 9/11, Osama bin Laden appeared on the cover of Time magazine. What later became an iconic image — the embodiment of evil, global terrorist #1, the face of Islamic extremism, or however else Americans came to view this face — did at the time show a man with an indisputable look of serenity.