Category Archives: cyberwarfare
Stuxnet raises ‘blowback’ risk in cyberwar
Tom Gjelten reports on efforts to defend the US from a Stuxnet-type attack — keeping mind that many experts believe that the Stuxnet worm, the first cyberweapon of its kind ever seen, was created by the US government.
The prospect of a cyberattack on U.S. infrastructure assets has prompted the Department of Homeland Security to arrange a new training program for the people who are supposed to protect the electric grid, manufacturing plants, refineries, water treatment centers and other critical facilities.
The top concern is the industrial control systems (ICS) that oversee the operation of key equipment at those facilities, from the valves to the breaker switches.
By hacking into the computer networks behind the industrial control systems, an adversary could reprogram an ICS so that it commands the equipment to operate at unsafe speeds or the valves to open when they should remain closed. This is roughly the way Stuxnet was able to damage the centrifuges in Iran.
Participants in the training program, based at the Idaho National Laboratory in Idaho Falls, are taken step by step through a simulated cyber-intrusion, so they can experience firsthand how a Stuxnet-like attack on their facilities might unfold.
During an Idaho National Laboratory exercise that was staged for visiting reporters in late September, instructor Mark Fabro installs his “red” team on the second floor of the training center, with the mission of penetrating the computer network of an unsuspecting industrial company, set up on the floor below.
The trainees on the “blue” team downstairs sit in a mock control room, monitoring their computer screens for any sign of trouble.
At first, everything appears normal. The attackers have managed to take control of the computer network without the defenders even realizing it. But gradually, problems develop in the control room.
“It’s running really slow,” says one operator. “My network is down.”
Sitting at their monitors upstairs, the attacking team is preparing to direct the computer system to issue commands to the industrial equipment.
“Take this one out,” says Fabro, pointing to a configuration that identifies the power supply to the control room. “Trip it. It should be dark very soon.”
Within 30 seconds, the mock control room downstairs is dark.
“This is not good,” says Jeff Hahn, a cybersecurity trainer who this day is playing the role of the CEO of the industrial company under attack. The blue team is under his direction.
“Our screens are black and the lights are out. We’re flying blind,” Hahn says.
During the exercise, the critical industrial facility under attack is a pumping station, such as might be found in a chemical plant or water treatment center. As the operators sit helpless at their terminals, the pumps suddenly start running, commanded by some unseen hand. Before long, water is gushing into a catch basin.
“There’s nothing we can do,” one of the operators tells the CEO. “We can only sit here and watch it happen.”
If this mock facility were an actual chemical plant, hazardous liquids could be spilling. If it were an electric utility, the turbines could be spinning out of control.
If it were a refinery, the tanks could be bursting or pipelines could be blowing up, all because the cyberattackers have been able to take over the computer network that controls the key operations.
The cyberattack scenario is all the more worrisome, because it is not clear that such attacks can be effectively stopped.
“Some of these [systems] can’t be protected,” says Weiss, the industrial control systems security expert. “We’re going to have to figure out how to recover from events that we simply can’t protect these systems from.”
Enter the cyber-dragon
In the September issue of Vanity Fair, Michael Joseph Gross writes:
Lying there in the junk-mail folder, in the spammy mess of mortgage offers and erectile-dysfunction drug ads, an e-mail from an associate with a subject line that looked legitimate caught the man’s eye. The subject line said “2011 Recruitment Plan.” It was late winter of 2011. The man clicked on the message, downloaded the attached Excel spreadsheet file, and unwittingly set in motion a chain of events allowing hackers to raid the computer networks of his employer, RSA. RSA is the security division of the high-tech company EMC. Its products protect computer networks at the White House, the Central Intelligence Agency, the National Security Agency, the Pentagon, the Department of Homeland Security, most top defense contractors, and a majority of Fortune 500 corporations.
The parent company disclosed the breach on March 17 in a filing with the Securities and Exchange Commission. The hack gravely undermined the reputation of RSA’s popular SecurID security service. As spring gave way to summer, bloggers and computer-security experts found evidence that the attack on RSA had come from China. They also linked the RSA attack to the penetration of computer networks at some of RSA’s most powerful defense-contractor clients—among them, Lockheed Martin, Northrop Grumman, and L-3 Communications. Few details of these episodes have been made public.
The RSA and defense-contractor hacks are among the latest battles in a decade-long spy war. Hackers from many countries have been exfiltrating—that is, stealing—intellectual property from American corporations and the U.S. government on a massive scale, and Chinese hackers are among the main culprits. Because virtual attacks can be routed through computer servers anywhere in the world, it is almost impossible to attribute any hack with total certainty. Dozens of nations have highly developed industrial cyber-espionage programs, including American allies such as France and Israel. And because the People’s Republic of China is such a massive entity, it is impossible to know how much Chinese hacking is done on explicit orders from the government. In some cases, the evidence suggests that government and military groups are executing the attacks themselves. In others, Chinese authorities are merely turning a blind eye to illegal activities that are good for China’s economy and bad for America’s. Last year Google became the first major company to blow the whistle on Chinese hacking when it admitted to a penetration known as Operation Aurora, which also hit Intel, Morgan Stanley, and several dozen other corporations. (The attack was given that name because the word “aurora” appears in the malware that victims downloaded.) Earlier this year, details concerning the most sweeping intrusion since Operation Aurora were discovered by the cyber-security firm McAfee. Dubbed “Operation Shady rat,” the attacks (of which more later) are being reported here for the first time. Most companies have preferred not to talk about or even acknowledge violations of their computer systems, for fear of panicking shareholders and exposing themselves to lawsuits—or for fear of offending the Chinese and jeopardizing their share of that country’s exploding markets. The U.S. government, for its part, has been fecklessly circumspect in calling out the Chinese.
Anonymous declares cyberwar against Orlando
The New York Times reports:
The hacker group Anonymous has declared a cyberwar against the City of Orlando, disabling Web sites for the city’s leading redevelopment organization, the local Fraternal Order of Police and the mayor’s re-election campaign.
Anonymous, a large yet loosely formed group of hackers that claimed responsibility for crashing the Web sites of MasterCard and the Church of Scientology, began attacking the Orlando-based Web sites earlier this week.
The group described its attacks as punishment for the city’s recent practice of arresting members of Orlando Food Not Bombs, an antipoverty group that provides vegan and vegetarian meals twice a week to homeless people in one of the city’s largest parks.
“Anonymous believes that people have the right to organize, that people have the right to give to the less fortunate and that people have the right to commit acts of kindness and compassion,” the group’s members said in a news release and video posted on YouTube on Thursday. “However, it appears the police and your lawmakers of Orlando do not.”
Cyber combat: act of war
The Wall Street Journal reports:
The Pentagon has concluded that computer sabotage coming from another country can constitute an act of war, a finding that for the first time opens the door for the U.S. to respond using traditional military force.
The Pentagon’s first formal cyber strategy, unclassified portions of which are expected to become public next month, represents an early attempt to grapple with a changing world in which a hacker could pose as significant a threat to U.S. nuclear reactors, subways or pipelines as a hostile country’s military.
In part, the Pentagon intends its plan as a warning to potential adversaries of the consequences of attacking the U.S. in this way. “If you shut down our power grid, maybe we will put a missile down one of your smokestacks,” said a military official.
Recent attacks on the Pentagon’s own systems—as well as the sabotaging of Iran’s nuclear program via the Stuxnet computer worm—have given new urgency to U.S. efforts to develop a more formalized approach to cyber attacks. A key moment occurred in 2008, when at least one U.S. military computer system was penetrated. This weekend Lockheed Martin, a major military contractor, acknowledged that it had been the victim of an infiltration, while playing down its impact.
The Associated Press reports:
This cyber attack didn’t go after people playing war games on their PlayStations. It targeted a company that helps the U.S. military do the real thing.
Lockheed Martin says it was the recent target of a “significant and tenacious” hack, although the defense contractor and the Department of Homeland Security insist the attack was thwarted before any critical data was stolen. The effort highlighted the fact that some hackers, including many working for foreign governments, set their sights on information far more devastating than credit card numbers.
Information security experts say a rash of cyber attacks this year — including a massive security breach at Sony Corp. last month that affected millions of PlayStation users — has emboldened hackers and made them more willing to pursue sensitive information.
“2011 has really lit up the boards in terms of data breaches,” said Josh Shaul, chief technology officer at Application Security, a New York-based company that is one of the largest database security software makers. “The list of targets just grows and grows.”
Iran reports a major setback at Bushehr nuclear power plant
The New York Times reports:
Iran told atomic inspectors this week that it had run into a serious problem at a newly completed nuclear reactor that was supposed to start feeding electricity into the national grid this month, raising questions about whether the trouble was sabotage, a startup problem, or possibly the beginning of the project’s end.
In a report on Friday, the International Atomic Energy Agency said Iran told inspectors on Wednesday that it was planning to unload nuclear fuel from its Bushehr reactor — the sign of a major upset. For years, Tehran has hailed the reactor as a showcase of its peaceful nuclear intentions and its imminent startup as a sign of quickening progress.
But nuclear experts said the giant reactor, Iran’s first nuclear power plant, now threatens to become a major embarrassment, as engineers remove 163 fuel rods from its core.
Iran gave no reason for the unexpected fuel unloading, but it has previously admitted that the Stuxnet computer worm infected the Bushehr reactor. On Friday, computer experts debated whether Stuxnet was responsible for the surprising development.
Russia, which provided the fuel to Iran, said earlier this month that the worm’s infection of the reactor should be investigated, arguing that it might trigger a nuclear disaster. Other experts said those fears were overblown, but noted that the full workings of the Stuxnet worm remained unclear.
In interviews Friday, nuclear experts said the trouble behind the fuel unloading could range from minor safety issues and operational ineptitude to serious problems that would bring the reactor’s brief operational life to a premature end.
Stuxnet attack on Bushehr: Russia warns of ‘Iranian Chernobyl’
Following Saturday’s New York Times report that the Stuxnet malware targeting Iran’s nuclear program was a joint US-Israeli operation, the Daily Telegraph reports that Russian nuclear scientists are concerned that the Bushehr nuclear plant could suffer catastrophic damage.
Fuel rods were inserted in the new reactor at the end of November and the plant is due to start producing electricity in the coming weeks. Ralph Langner, whose German team first identified Iran’s nuclear program as Stuxnet’s target, says the plant’s steam turbine is vulnerable to attack and in November wrote: “If you blow a 1000 Megawatt turbine, you will very likely be able to see the impact by satellite imagery.”
Con Coughlin writes:
Russian scientists working at the plant have become so concerned by Iran’s apparent disregard for nuclear safety issues that they have lobbied the Kremlin directly to postpone activation until at least the end of the year, so that a proper assessment can be made of the damage caused to its computer operations by Stuxnet.
The Iranian government is bitterly opposed to any further delay, which it would regard as another blow to national pride on a project that is more than a decade behind schedule. While Western intelligence officials believe Iran’s nuclear programme is aimed at producing nuclear weapons, Iran insists the project’s goals are peaceful.
The Russian scientists’ report to the Kremlin, a copy of which has been seen by The Daily Telegraph, concludes that, despite “performing simple, basic tests” on the Bushehr reactor, the Russian team “cannot guarantee safe activation of the reactor”.
It also accuses the Iranian management team, which is under intense political pressure to stick to the deadline, of “not exhibiting the professional and moral responsibility” that is normally required. They accuse the Iranians of having “disregard for human life” and warn that Russia could find itself blamed for “another Chernobyl” if it allows Bushehr to go ahead.
While it’s natural that the Russians would be concerned about being blamed, in such a scenario it’s a bit difficult to see how US interests would be served if vital shipping lanes and America’s Gulf allies were also put in jeopardy.
An American expert in nuclear intelligence told the New York Times “that Israel worked in collaboration with the United States in targeting Iran, but that Washington was eager for ‘plausible deniability'” — plausible deniability that the US no longer has.
Does this raise the possibility that the US might need to discreetly intervene to prevent an Israeli-made disaster?
Stuxnet could cause Bushehr meltdown
On the eve of the release of a new IAEA report on Iran, officials linked to the UN nuclear oversight agency have added to speculation on the possible impact that the Stuxnet malware may have had on Iran’s nuclear program — including the possibility that it could lead to the meltdown of the reactor in the Bushehr nuclear power plant.
The Associated Press reports:
Iran’s nuclear program has suffered a recent setback, with major technical problems forcing the temporary shutdown of thousands of centrifuges enriching uranium, diplomats told The Associated Press on Monday.
The diplomats said they had no specifics on the nature of the problem that in recent months led Iranian experts to briefly power down the machines they use for enrichment — a nuclear technology that has both civilian and military uses.
But suspicions focused on the Stuxnet worm, the computer virus thought to be aimed at Iran’s nuclear program, which experts last week identified as being calibrated to destroy centrifuges by sending them spinning out of control.
[…]
Tehran has taken hundreds of centrifuges off line over the past 18 months, prompting speculation of technical problems.A U.N official close to the IAEA said a complete stop in Iran’s centrifuge operation would be unprecedented to his knowledge but declined to discuss specifics.
[…]
Separately, another official from an IAEA member country suggested the worm could cause further damage to Iran’s nuclear program.The official also asked for anonymity because his information was privileged. He cited a Western intelligence report suggesting that Stuxnet had infected the control system of Iran’s Bushehr reactor and would be activated once the Russian-built reactor goes on line in a few months.
Stuxnet would interfere with control of “basic parameters” such as temperature and pressure control and neutron flow, that could result in the meltdown of the reactor, raising the specter of a possible explosion, he said.
Evolving understanding of Stuxnet
Reporting on the latest findings on the design of the Stuxnet malware which targeted Iran’s nuclear program, the New York Times says that Ralph Langner — a German software engineer who has been one of the leading investigators — has identified two forms of attack directed at different targets.
In a statement Friday on his Web site, he described two different attack modules that are designed to run on different industrial controllers made by Siemens, the German industrial equipment maker. “It appears that warhead one and warhead two were deployed in combination as an all-out cyberstrike against the Iranian nuclear program,” he wrote.
In testimony before the Senate on Wednesday, federal and private industry officials said that the Iranian nuclear program was a probable target, but they stopped short of saying they had confirming evidence. Mr. Langner said, however, that he had found enough evidence within the programs to pinpoint the intended targets. He described his research process as being akin to being at a crime scene and examining a weapon but lacking a body.
The second code module — aimed at the [Bushehr] nuclear power plant — was written with remarkable sophistication, he said. The worm moves from personal computers to Siemens computers that control industrial processes. It then inserts fake data, fooling the computers into thinking that the system is running normally while the sabotage of the frequency converters is taking place. “It is obvious that several years of preparation went into the design of this attack,” he wrote.
In a separate report, the New York Times said:
The paternity of the worm is still in dispute, but in recent weeks officials from Israel have broken into wide smiles when asked whether Israel was behind the attack, or knew who was.
Langner says: “Stuxnet is like the arrival of an F-35 fighter jet on a World War I battlefield.”
Why would Israel target a civilian nuclear facility that is generally understood to pose no proliferation threat?
In line with its practice of paying selective attention to international opinion, Israel’s public position has been that Iran should not be “rewarded” for its defiance of the international community by being allowed to operate Bushehr. Moreover, there could also be a political motive for trying to prevent Bushehr from operating successfully, that being, to undermine the credibility of the nuclear program in the eyes of the otherwise widely supportive Iranian public.
Langner says that a cyber attack targeting a nuclear reactor is virtually impossible but that Bushehr’s steam turbine (located outside the containment facility) could be hit and that “Stuxnet can destroy the turbine as effectively as an air strike.”
Like everyone else, the Israelis understand that the most critical part of the infrastructure in Iran’s nuclear program is not made of steel or concrete — it is the expertise of Iran’s nuclear scientists and engineers. (For that reason, Israel’s covert war against Iran apparently includes a “decapitation” program aimed at eliminating the top figures in Iran’s nuclear operations.)
Since many of the skills required to run a civilian nuclear power program are presumably transferable to a military program, sabotage on any of Iran’s nuclear facilities will have the net effect of becoming a drain on the human resources available to advance the program as a whole.
The fact is, after decades of nuclear development, Iran still has precious little to show for its efforts. Keep in mind, the construction of Bushehr began 35 years ago and Iran’s nuclear program was launched in the 1950s!
Clear evidence that Stuxnet targeted Natanz nuclear centrifuges

The latest evidence revealed by two independent groups of researchers studying the code in the Stuxnet malware — the world’s first identified cyber weapon — indicates the Iran’s uranium enrichment facility at Natanz was almost certainly the target for attack. Not only was it aimed at programmable logic controllers that regulate motor speeds in a limited number of applications, mainly in uranium enrichment. Stuxnet would also alter operating speeds in such a way that centrifuges would unpredictably malfunction — the intent clearly being that the sabotage would be both effective yet also go unrecognized as sabotage.
Christian Science Monitor reports:
Once Stuxnet has locked its sights on the target, it alternately brings the centrifuge process to either a grinding slowdown or an explosive surge – by sabotaging the centrifuge refining process. It tells the commandeered PLC to force the frequency converter drive to do something it’s not ever supposed to do: Switch back and forth from high speed to low speed at intervals punctuated by long period of normal operation. It also occasionally pushes the centrifuge to far exceed its maximum speed.
“Stuxnet changes the output frequencies and thus the speed of the motors for short intervals over periods of months,” Symantec researcher Eric Chien reported Nov. 12 on his blog. “Interfering with the speed of the motors sabotages the normal operation of the industrial control process.”
Normal operating frequency of the special drive is supposed to be between 807 and 1210 Hz – the higher the hertz, the higher the speed. One hertz means that a cycle is repeated once per second.
Stuxnet “sabotages the system by slowing down or speeding up the motor to different rates at different times,” including sending it up to 1410 Hz, well beyond its intended maximum speed. Such wide swings would probably destroy the centrifuge – or at least wreck its ability to produce refined uranium fuel, others researchers say.
“One reasonable goal for the attack could be to destroy the centrifuge rotor by vibration, which causes the centrifuge to explode” as well as simply degrading the output subtly over time, Ralph Langner, the German researcher who first revealed Stuxnet’s function as a weapon in mid-September, wrote on his blog last week.
All of the circumstantial evidence points in the same direction: Natanz.
The Natanz nuclear centrifuge fuel-refining plant may have been hit first by Stuxnet in mid-2009, said Frank Rieger, a German researcher with Berlin encryption firm GSMK. The International Atomic Energy Agency found a sudden drop in the number of working centrifuges at the Natanz site, he noted in an interview in September.
“It seems like the parts of Stuxnet dealing with PLCs have been designed to work on multiple nodes at once – which makes it fit well with a centrifuge plant like Natanz,” Mr. Rieger says. By contrast, Bushehr is a big central facility with many disparate PLCs performing many different functions. Stuxnet seems focused on replicating its intrusion across a lot of identical units in a single plant, he said.
That and Symantec’s new findings also dovetail nicely with Mr. Langner’s detailed findings in his ongoing dissection of Stuxnet. Parts of the code show Stuxnet causing problems for short periods, then resuming undisturbed operation, Symantec’s findings show. As a result, Langner writes, “the victim, having no clue of being under a cyber attack, will replace broken centrifuges by new ones – until ending in frustration. It’s like a Chinese water torture.”
Pentagon’s Cyber Command seeks authority to expand its battlefield
A defense official quote in this report from the Washington Post says: “Al Qaeda is everywhere.”
That’s the same as saying that anyone who has a blog is “everywhere” — presence on the web is by its nature global. Still, it’s a dubious claim when coming out of the mouth of a US government official because it will inevitably be used to justify the extension of government powers in ways that vastly exceed the size or scope of the threat that they are designed to counter.
The Pentagon’s new Cyber Command is seeking authority to carry out computer network attacks around the globe to protect U.S. interests, drawing objections from administration lawyers uncertain about the legality of offensive operations.
Cyber Command’s chief, Gen. Keith B. Alexander, who also heads the National Security Agency, wants sufficient maneuvering room for his new command to mount what he has called “the full spectrum” of operations in cyberspace.
Offensive actions could include shutting down part of an opponent’s computer network to preempt a cyber-attack against a U.S. target or changing a line of code in an adversary’s computer to render malicious software harmless. They are operations that destroy, disrupt or degrade targeted computers or networks.
But current and former officials say that senior policymakers and administration lawyers want to limit the military’s offensive computer operations to war zones such as Afghanistan, in part because the CIA argues that covert operations outside the battle zone are its responsibility and the State Department is concerned about diplomatic backlash.
The administration debate is part of a larger effort to craft a coherent strategy to guide the government in defending the United States against attacks on computer and information systems that officials say could damage power grids, corrupt financial transactions or disable an Internet provider.
The effort is fraught because of the unpredictability of some cyber-operations. An action against a target in one country could unintentionally disrupt servers in another, as happened when a cyber-warfare unit under Alexander’s command disabled a jihadist Web site in 2008. Policymakers are also struggling to delineate Cyber Command’s role in defending critical domestic networks in a way that does not violate Americans’ privacy.
Why the threat of cyber-warfare is being exaggerated
In an assessment of the dangers posed by cyber-warfare and while noting that the threats posed by cyber-warfare and cyber-espionage are repeatedly being conflated, Seymour Hersh points out that the interests of the National Security Agency and those of hackers coincide: both want communications networks that remain open to interception. But John Arquilla, who has taught since 1993 at the U.S. Naval Postgraduate School in Monterey, argues that privacy and security are complimentary. “We would all be far better off if virtually all civil, commercial, governmental, and military internet and web traffic were strongly encrypted,” he writes in his book, Worst Enemies.
At the same time, cyber-warfare fearmongers like Richard Clarke describe apocalyptic scenarios in which America could be crippled by China, though China’s motives for engaging in such an attack would be hard to fathom.
Within a quarter of an hour, 157 major metropolitan areas have been thrown into knots by a nationwide power blackout hitting during rush hour. Poison gas clouds are wafting toward Wilmington and Houston. Refineries are burning up oil supplies in several cities. Subways have crashed in New York, Oakland, Washington, and Los Angeles. . . . Aircraft are literally falling out of the sky as a result of midair collisions across the country. . . . Several thousand Americans have already died.
Hersh quotes James Lewis, a senior fellow at the Center for Strategic and International Studies, who points out that China is massively invested in the maintenance — not destruction — of America’s economic health: “Current Chinese officials have told me that we’re not going to attack Wall Street, because we basically own it” — a reference to China’s holdings of nearly a trillion dollars in American securities — “and a cyber-war attack would do as much economic harm to us as to you.”
[President Obama’s coordinator for cyber security] Howard Schmidt doesn’t like the term “cyber war.” “The key point is that cyber war benefits no one,” Schmidt told me in an interview at the Old Executive Office Building. “We need to focus on that fact. When people tell me that these guys or this government is going to take down the U.S. military with information warfare I say that, if you look at the history of conflicts, there’s always been the goal of intercepting the communications of combatants — whether it’s cutting down telephone poles or intercepting Morse-code signalling. We have people now who have found that warning about ‘cyber war’ has become an unlikely career path” — an obvious reference to McConnell and Clarke. “All of a sudden, they have become experts, and they get a lot of attention. ‘War’ is a big word, and the media is responsible for pushing this, too. Economic espionage on the Internet has been mischaracterized by people as cyber war.”
Schmidt served in Vietnam, worked as a police officer for several years on a SWAT team in Arizona, and then specialized in computer-related crimes at the F.B.I. and in the Air Force’s investigative division. In 1997, he joined Microsoft, where he became chief of security, leaving after the 9/11 attacks to serve in the Bush Administration as a special adviser for cyber security. When Obama hired him, he was working as the head of security for eBay. When I asked him about the ongoing military-civilian dispute, Schmidt said, “The middle way is not to give too much authority to one group or another and to make sure that we share information with each other.”
Schmidt continued, “We have to protect our infrastructure and our way of life, for sure. We do have vulnerabilities, and we do talk about worst-case scenarios” with the Pentagon and the Department of Homeland Security. “You don’t see a looming war and just wait for it to come.” But, at the same time, “we have to keep our shipping lanes open, to continue to do commerce, and to freely use the Internet.”
How should the power grid be protected? It does remain far too easy for a sophisticated hacker to break into American networks. In 2008, the computers of both the Obama and the McCain campaigns were hacked. Suspicion fell on Chinese hackers. People routinely open e-mails with infected attachments, allowing hackers to “enslave” their computers. Such machines, known as zombies, can be linked to create a “botnet,” which can flood and effectively shut down a major system. Hackers are also capable of penetrating a major server, like Gmail. Guesses about the cost of cyber crime vary widely, but one survey, cited by President Obama in a speech in May, 2009, put the price at more than eight billion dollars in 2007 and 2008 combined. Obama added, referring to corporate cyber espionage, “It’s been estimated that last year alone cyber criminals stole intellectual property from businesses worldwide worth up to one trillion dollars.”
One solution is mandated encryption: the government would compel both corporations and individuals to install the most up-to-date protection tools. This option, in some form, has broad support in the technology community and among privacy advocates. In contrast, military and intelligence eavesdroppers have resisted nationwide encryption since 1976, when the Diffie-Hellman key exchange (an encryption tool co-developed by Whitfield Diffie) was invented, for the most obvious of reasons: it would hinder their ability to intercept signals. In this sense, the N.S.A.’s interests align with those of the hackers.
Stuxnet, Bushehr and Siemens WinCC software
Ben D, a commenter at this site and Arms Control Wonk is skeptical about my assertion that Siemens SCADA software is being used at Iran’s Bushehr nuclear facility. I based that claim on a UPI photograph that led the German industrial security expert, Ralph Langner, to speculate that Bushehr was the intended target of the Stuxnet malware.
These are Ben’s qualms:
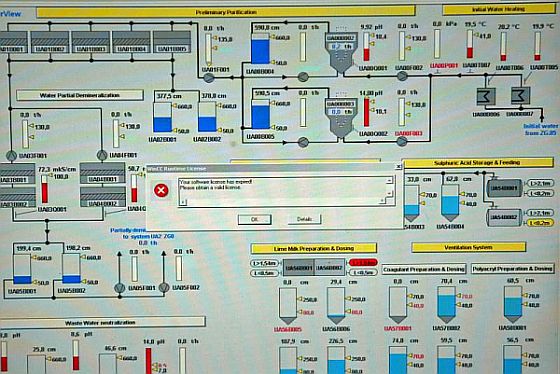
Concerning the UPI image of a control panel with a MS look window superimposed that says.. “WinCC Runtime License: Your software license has expired. Please obtain a valid license”, well it doesn’t prove a thing.
First of all, the WinCC window could so easily be a photo- shopped overlay on the image of a process control panel.
Secondly, the Control Panel image is typical of process control panels everywhere and even if the WinCC window was not photo-shopped, what has that got to do with Bushehr. There is nothing else in the image to provide any information whatsoever about the local environment to provide any context as to its locality or purpose.
Thirdly, UPI does not provide a source for anyone claiming that the UPI Photo by Mohammad Kheirkhah is actually Bushehr, they just provide a narrative to imply that it is.
Fourthly, Ralph Lagner is not claiming the UPI image is actually genuine or that it is of Bushehr, he merely prefaces his speculative theory with ” If the picture is authentic, which I have no means of verifying,….”.
Has the image been doctored? I’m not in a position to determine that, but the Hacker Factor Blog did some image analysis and concluded that it was not doctored. He has other reasons for questioning whether it was taken at Bushehr but found no evidence that it had been manipulated with Photoshop.
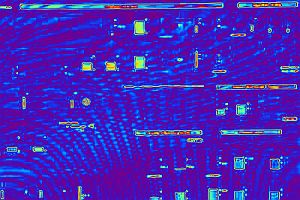 This image apparently confirms that the photograph is of a computer monitor and the continuity in the ripple pattern across the part of the screen where the WinCC message appears seems to confirm that this was not inserted from a different screen image. (This ripple pattern can be seen both in the blue image and the close-up image.)
This image apparently confirms that the photograph is of a computer monitor and the continuity in the ripple pattern across the part of the screen where the WinCC message appears seems to confirm that this was not inserted from a different screen image. (This ripple pattern can be seen both in the blue image and the close-up image.)
So, assuming that the WinCC expired-licence message was actually appearing on that monitor screen, is there any evidence that the monitor and the control system it depicts is in Bushehr?
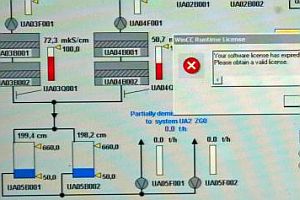 Frankly, I was willing to accept that UPI was not misrepresenting or incorrectly labeling its photos, but still, some additional analysis was both in order and turned out to be fruitful. There is indeed evidence that this image depicts a Bushehr control system.
Frankly, I was willing to accept that UPI was not misrepresenting or incorrectly labeling its photos, but still, some additional analysis was both in order and turned out to be fruitful. There is indeed evidence that this image depicts a Bushehr control system.
The elements in the schematic have a uniform numbering system — UA04B001, UA04B002 etc.
 Another UPI photograph appears to show the physical components depicted on the system control monitor. This vessel shown on the right is numbered UA06B002. That particular number doesn’t appear on the monitor image but it’s hard to believe that this is not part of the same system.
Another UPI photograph appears to show the physical components depicted on the system control monitor. This vessel shown on the right is numbered UA06B002. That particular number doesn’t appear on the monitor image but it’s hard to believe that this is not part of the same system.
OK. But maybe the screen image and the image of an Iranian technician turning a valve were taken some place other than Bushehr.
 Well, UPI’s photographer was one among a group of international journalists who were shown around Bushehr in February 2009. They included Jon Leyne, a reporter for the BBC, and a video in his report shows the same assembly of pale gray vessels that appear in the UPI photo. Indeed, an AFP image in the same report shows the same technician, from a different angle, doing his valve-turning performance for the assembled press.
Well, UPI’s photographer was one among a group of international journalists who were shown around Bushehr in February 2009. They included Jon Leyne, a reporter for the BBC, and a video in his report shows the same assembly of pale gray vessels that appear in the UPI photo. Indeed, an AFP image in the same report shows the same technician, from a different angle, doing his valve-turning performance for the assembled press.
With the evidence that I’ve laid out I will assert with even more confidence that the Bushehr nuclear plant uses Siemens WinCC SCADA software. I also see little reason to doubt that Iranian officials were telling the truth when they said that Stuxnet had been found on personal computers used by the facility’s operators. What I remain skeptical about is their claim that the malware did not penetrate the system. How confident the Iranians are on that question may become evident in the coming months when the plant begins or fails to begin generating electricity.
The Israeli threat to global security
A USB memory stick carrying the Stuxnet malware is believed to have provided intruders with access to Iran’s nuclear program. The same technique was used in November 2008 to break into CENTCOM, providing a foreign government with unfiltered access to the Pentagon’s command of the wars in Iraq and Afghanistan. Did both attacks come from the same source?
Earlier this week, Reuters reported:
Cyber warfare has quietly grown into a central pillar of Israel’s strategic planning, with a new military intelligence unit set up to incorporate high-tech hacking tactics, Israeli security sources said on Tuesday.
Israel’s pursuit of options for sabotaging the core computers of foes like Iran, along with mechanisms to protect its own sensitive systems, were unveiled last year by the military intelligence chief, Major-General Amos Yadlin.
The government of Prime Minister Benjamin Netanyahu has since set cyber warfare as a national priority, “up there with missile shields and preparing the homefront to withstand a future missile war”, a senior source said on condition of anonymity.
Back in 1997, when the US did not overtly support political assassinations, President Clinton intervened to save the life of Khalid Meshaal. The Hamas political bureau chief had been poisoned by Mossad operatives (carrying stolen Canadian passports) on the streets of Jordan’s capital, Amman.
Clinton wasn’t trying to help Hamas but knew that a peace treaty he had helped broker between Israel and Jordan would be in jeopardy if Prime Minister Netanyahu thought he could disregard the sovereignty of Jordan and carry out assassinations with impunity. Likewise, neither King Hussein nor the Canadian government believed that Israeli actions showing a flagrant disregard for the authority of their respective governments could go unanswered.
Netanyahu would probably have found Clinton’s pressure unpersuasive were it not for the fact that the Israeli operatives had already been arrested. In exchange for their release, the Israelis supplied the antidote that saved Meshaal’s life while also releasing the Hamas spiritual leader Sheikh Ahmed Yassin.
Then came 9/11.
Before long, Yassin had been assassinated, the US was using Israeli methods of torture in its campaign against an amorphous Islamic threat, Israel’s own war crimes were sanctioned by the US in the name of the war on terrorism, and the use of stolen foreign passports by Mossad agents committing murder on foreign soil provoked nothing more than a diplomatic slap on the wrists.
When suspected Israeli agents were reported this week to be conducting surveillance on the NSA in Utah, the national security breach did not provoke a murmur in the national media — even though a string of similar incidents prior to 9/11 raised questions about whether Israel could have had foreknowledge of the attacks.
The willingness of this and the previous administration to allow Israel to disregard international law shows that even if the Israel lobby can no longer flourish like a night flower, its power is barely diminished. Even so, the appearance of the Stuxnet malware should be a wake-up call to every government around the world that refuses to place Israel’s national interests above its own.
In its conception, Stuxnet can be viewed very much like a targeted killing — but one designed to attack silently and leave no trace of its origin.
It’s creators understood that they had designed an exceedingly dangerous weapon and so they made sure its damage could be contained. But it seems not to have worked according to plan and so caution got tossed out of the window. Apparently, Israel did what it has done so many times before: pursued what it regarded as its own interests with an utter disregard for the international consequences.
Computerworld reports:
The original infection method, which relied on infected USB drives, included a counter that limited the spread to just three PCs, said [Liam] O Murchu [operations manager with Symantec’s security response]. “It’s clear that the attackers did not want Stuxnet to spread very far,” he said. “They wanted it to remain close to the original infection point.”
O Murchu’s research also found a 21-day propagation window; in other words, the worm would migrate to other machines in a network only for three weeks before calling it quits.
Those anti-propagation measures notwithstanding, Stuxnet has spread widely. Why?
Kaspersky’s [Roel] Schouwenberg [a senior antivirus researcher] believes it’s because the initial attack, which relied on infected USB drives, failed to do what Stuxnet’s makers wanted.
“My guess is that the first variant didn’t achieve its target,” said Schouwenberg, referring to the worm’s 2009 version that lacked the more aggressive propagation mechanisms, including multiple Windows zero-day vulnerabilities. “So they went on to create a more sophisticated version to reach their target.”
That more complex edition, which O Murchu said was developed in March of this year, was the one that “got all the attention,” according to Schouwenberg. But the earlier edition had already been at work for months by then — and even longer before a little-known antivirus vendor from Belarus first found it in June. “The first version didn’t spread enough, and so Stuxnet’s creators took a gamble, and abandoned the idea of making it stealthy,” said Schouwenberg.
In Schouwenberg’s theory, Stuxnet’s developers realized their first attempt had failed to penetrate the intended target or targets, and rather than simply repeat the attack, decided to raise the ante.
“They spent a lot of time and money on Stuxnet,” Schouwenberg said. “They could try again [with the USB-only vector] and maybe fail again, or they could take the risk of it spreading by adding more functionality to the worm.”
O Murchu agreed that it was possible the worm’s creators had failed to infect, and thus gain control, of the industrial systems running at their objective(s), but said the code itself didn’t provide clear clues.
What is clear, O Murchu said in a news conference Friday morning, is that Stuxnet evolved over time, adding new ways to spread on networks in the hope of finding specific PLCs (programming logic control) hardware to hijack. “It’s possible that [the attackers] didn’t manage to get to all of their targets [with the earlier version],” O Murchu said. “The increased sophistication of Stuxnet in 2010 may indicate that they had not reached their target.”
With the proliferation of Stuxnet, Schouwenberg said that the country or countries that created the worm may have themselves been impacted by its spread. But that was likely a calculated risk the worm’s developers gladly took.
And that risk may have been quite small. “Perhaps they knew that their own critical infrastructure wouldn’t be affected by Stuxnet because it’s not using Siemens PLCs,” Schouwenberg said.
The danger now posed by Stuxnet is not simply through its direct proliferation but by virtue of the fact that it provides a blueprint that can be adapted by other parties who would otherwise lack the resources to create malware this sophisticated from scratch.
What might have been conceived as a tool to prevent the creation of a weapon of mass destruction could itself be turned into a WMD.
The Washington Post reports:
“Stuxnet opened Pandora’s box,” said Ralph Langner, a German researcher whose early analysis of the worm’s ability to target control systems raised public awareness of the threat. “We don’t need to be concerned about Stuxnet, but about the next-generation malware we will see after Stuxnet.”
Sean McGurk, director of the U.S. National Cybersecurity and Communications Integration Center at the Department of Homeland Security, said that the department posted its first report to industry recommending steps to mitigate the effects of Stuxnet on July 15. But “not even two days later,” he said, a hacker Web site posted the code so that others could use it to exploit the vulnerabilities in Microsoft.
“So we know that once the information is out in the wild, people are taking it and they’re modifying it,” he said.
In other words, what started as an Israeli cyber attack on nuclear installations in Iran could end up crashing the US powergrid or causing havoc anywhere else on the globe.
Even before Stuxnet loomed over the horizon, serious warnings were being issued about the United States’ vulnerability to a crippling cyber attack, yet thus far none of those raising the alarm have pointed to the ways in which Israel’s cyber warfare capabilities may now indirectly or directly threaten the United States and its interests.
– – –
Late last year, 60 Minutes reported on America’s vulnerability to a major cyber attack.
Israel: smart enough to create Stuxnet and stupid enough to use it
Ever since speculation began, suggesting that Israel is the source of the Stuxnet malware, there has been a buzz of excitement in the Zionist corner of the blogosphere. The DEBKAfile — trusted source for pro-Israel fantasists all over the world — declared that if it turns out that millions of Iranian industrial units have been hit, “this cyber weapon attack on Iran would be the greatest ever.”
Glee at such a prospect is not shared by observers who lack the Zionist pathological obsession with Iran.
Stephen Spoonamore, a veteran cybersecurity consultant interviewed by NPR said: “I can think of very few stupider blowback decisions” than to release code that controls most of the worlds’ hydroelectric dams or many of the world’s nuclear plants or many of the world’s electrical switching stations.
The fallout from Stuxnet is clearly going global.
AFP now reports:
The Stuxnet computer worm has wreaked havoc in China, infecting millions of computers around the country, state media reported this week.
Stuxnet is feared by experts around the globe as it can break into computers that control machinery at the heart of industry, allowing an attacker to assume control of critical systems like pumps, motors, alarms and valves.
It could, technically, make factory boilers explode, destroy gas pipelines or even cause a nuclear plant to malfunction.
The virus targets control systems made by German industrial giant Siemens commonly used to manage water supplies, oil rigs, power plants and other industrial facilities.
“This malware is specially designed to sabotage plants and damage industrial systems, instead of stealing personal data,” an engineer surnamed Wang at antivirus service provider Rising International Software told the Global Times.
“Once Stuxnet successfully penetrates factory computers in China, those industries may collapse, which would damage China’s national security,” he added.
Another unnamed expert at Rising International said the attacks had so far infected more than six million individual accounts and nearly 1,000 corporate accounts around the country, the official Xinhua news agency reported.
Jeffrey Carr, author of “Inside Cyber Warfare,” describes what he believes is the first example of Stuxnet’s destructive power: the loss of India’s INSAT-4B communications satellite which shut down in July. The satellite’s control systems use Siemens S7-400 PLC and SIMATIC WinCC software, both of which are targeted by Stuxnet.
If speculation that Stuxnet was created by Israel has been driven by the circumstantial evidence that Israel’s nemesis Iran appears to have been the primary target, there is now some subtle but concrete evidence again pointing in Israel’s direction.
Computerworld reports:
Buried in Stuxnet’s code is a marker with the digits “19790509” that the researchers believe is a “do-not infect” indicator. If the marker equals that value, Stuxnet stops in its tracks, and does not infect the targeted PC.
The researchers — Nicolas Falliere, Liam O Murchu and Eric Chen — speculated that the marker represents a date: May 9, 1979.
“While on May 9, 1979, a variety of historical events occurred, according to Wikipedia “Habib Elghanian was executed by a firing squad in Tehran sending shock waves through the closely knit Iranian Jewish community,” the researchers wrote.
Elghanian, a prominent Jewish-Iranian businessman, was charged with spying for Israel by the then-new revolutionary government of Iran, and executed May 9, 1979.
Earlier, the New York Times reported:
Deep inside the computer worm that some specialists suspect is aimed at slowing Iran’s race for a nuclear weapon lies what could be a fleeting reference to the Book of Esther, the Old Testament tale in which the Jews pre-empt a Persian plot to destroy them.
That use of the word “Myrtus” — which can be read as an allusion to Esther — to name a file inside the code is one of several murky clues that have emerged as computer experts try to trace the origin and purpose of the rogue Stuxnet program, which seeks out a specific kind of command module for industrial equipment.
Not surprisingly, the Israelis are not saying whether Stuxnet has any connection to the secretive cyberwar unit it has built inside Israel’s intelligence service. Nor is the Obama administration, which while talking about cyberdefenses has also rapidly ramped up a broad covert program, inherited from the Bush administration, to undermine Iran’s nuclear program. In interviews in several countries, experts in both cyberwar and nuclear enrichment technology say the Stuxnet mystery may never be solved.
There are many competing explanations for myrtus, which could simply signify myrtle, a plant important to many cultures in the region. But some security experts see the reference as a signature allusion to Esther, a clear warning in a mounting technological and psychological battle as Israel and its allies try to breach Tehran’s most heavily guarded project. Others doubt the Israelis were involved and say the word could have been inserted as deliberate misinformation, to implicate Israel.
The same report cites Shai Blitzblau, the technical director and head of the computer warfare laboratory at Maglan, an Israeli company specializing in information security, who said he was “convinced that Israel had nothing to do with Stuxnet.”
“We did a complete simulation of it and we sliced the code to its deepest level,” he said. “We have studied its protocols and functionality. Our two main suspects for this are high-level industrial espionage against Siemens and a kind of academic experiment.”
Did Blitzblau present his findings at this week’s VB Conference in Vancouver where Stuxnet was the focus of attention? No — which is not surprising given his vacuous claim to have studied the code at its deepest level while other experts say it will take months to penetrate the thousands of lines of code contained in a 500kB piece of software.
As for why Israeli programmers would have inserted clues about about authorship deep inside the malware, the most obvious explanation would be the most prosaic: pride.
Even when the utmost secrecy is called for, there are those who cannot resist the temptation to leave their mark.
As for the significance of another finding — June 24, 2012 is the “kill date” after which the worm will refuse to execute — again, we can only speculate.
Is this the cut-off point for Israel’s campaign of cyber warfare against Iran after which will come the time for real war? Right in the run up to the 2012 US presidential election.
Iran confirms Stuxnet found at Bushehr nuclear power plant
 An AFP report earlier today reveals that the Stuxnet malware has been found at Iran’s nuclear power plant at Bushehr. (All the blockquotes below are from the AFP report.)
An AFP report earlier today reveals that the Stuxnet malware has been found at Iran’s nuclear power plant at Bushehr. (All the blockquotes below are from the AFP report.)
Iranian officials confirm that 30,000 industrial computers in Iran have been hit by Stuxnet yet deny that Bushehr was among those infected.
That might be what Iranian officials believe, but whether it’s a belief based on fact is another matter.
As we get further into this report, it becomes apparent there is a high probability both that Bushehr has been penetrated and that the malware may still be active.
Siemens said its software has not been installed at the plant, and an Iranian official denied the malware may have infected nuclear facilities.
Siemens might not know that its software was installed at the plant, but thanks to a UPI photograph, we know that Bushehr control systems do indeed run on Siemens’ WinCC SCADA system. The warning shown below says: “WinCC Runtime License: Your software license has expired. Please obtain a valid license.”
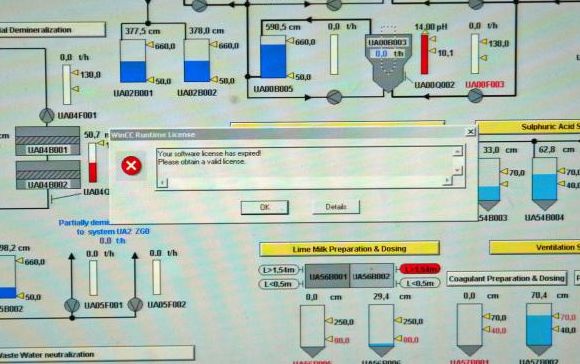
This is what Ralph Langner, a German industrial security expert, saw as a red flag indicating that the plant is vulnerable to a cyber attack.
“This virus has not caused any damage to the main systems of the Bushehr power plant,” Bushehr project manager Mahmoud Jafari said on Iran’s Arabic-language Al-Alam television network.
“All computer programmes in the plant are working normally and have not crashed due to Stuxnet,” said Jafari, adding there was no problem with the plant’s fuel supply.
The official IRNA news agency meanwhile quoted him as saying the worm had infected some “personal computers of the plant’s personnel.”
And no infected personal computers have been hooked into the plants control system?
As indicated in this photograph showing Russian contractors inside Bushehr, the path from a personal computer to the plant’s control system is short and direct.

As for the fact that Bushehr’s control system has not crashed, the fact that the project manager cites this as evidence that the system is malware-free suggests that he does not understand how Stuxnet is designed. Stuxnet monitors process conditions and until those conditions have been met, everything should work fine. This is not like a virus that slows down an operating system.
Given the inside knowledge that Stuxnet’s creators required, it seems quite likely that the moment they would want it to kick into action — assuming that Bushehr was the intended target — would be a moment at which a catastrophic system failure could be attributed to a flaw in the facility’s construction, design or operation. A failure, for instance, as the plant approaches its intended full operational generation capacity. The 1000 megawatt plant is expected to have reached only 40% capacity by the end of December.
Telecommunications minister Reza Taqipour said “the worm has not been able to penetrate or cause serious damage to government systems.”
Again, this statement suggests a lack of understanding about Stuxnet’s highly targeted design and the fact that it is designed not to cause damage elsewhere.
Mahmoud Liayi, head of the information technology council at the ministry of industries said:
…industries were currently receiving systems to combat Stuxnet, while stressing Iran had decided not to use anti-virus software developed by Siemens because “they could be carrying a new version of the malware.”
“When Stuxnet is activated, the industrial automation systems start transmitting data about production lines to a main designated destination by the virus,” Liayi said.
“There, the data is processed by the worm’s architects and then engineer plots to attack the country.”
If this is the official consensus, Iranian facilities such as Bushehr are as vulnerable now as they were before anyone knew about Stuxnet. Liayi’s statement suggests that Stuxnet is being viewed as a tool of espionage designed to facilitate rather than execute sabotage.
Bush White House security adviser: Israel likely source of cyber attack on Iran
(Updated below)
In an interview on Bloomberg TV, Richard Falkenrath suggested that Israel is the most likely source of the Stuxnet malware which seems designed to cripple industrial facilities in Iran.
Falkenrath is currently the Deputy Commissioner of Counter-Terrorism for the NYPD and held several positions in the George W Bush White House including Deputy Assistant to the President and Deputy Homeland Security Advisor.
The Associated Press says that experts from Iran’s nuclear agency met this week to discuss how to combat the Stuxnet attack on Iranian facilities, according to the semi-official ISNA news agency.
Iran’s Mehr News Agency adds:
The director of the Information Technology Council of the Industries and Mines Ministry has announced that the IP addresses of 30,000 industrial computer systems infected by this malware have been detected, the Mehr New Agency reported on Saturday.
“An electronic war has been launched against Iran,” Mahmoud Liaii added.
“This computer worm is designed to transfer data about production lines from our industrial plants to (locations) outside of the country,” he said.
He also announced that a working group composed of representatives from the Communications and Information Technology Ministry, the Industries and Mines Ministry, and the Passive Defense Organization has been set up to find ways to combat the spyware.
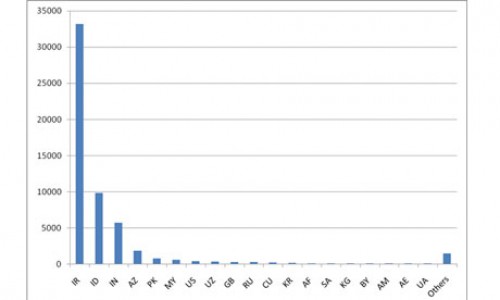
Graph shows concentration of Stuxnet-infected computers in Iran as of August. Source: Symantec
Eugene Kaspersky, co-founder and chief executive officer of Kaspersky Lab, says that the creation of Stuxnet marks the beginning of the new age of cyber-warfare.
Speaking at the Kaspersky Security Symposium with international journalists in Munich, Germany, Kaspersky described Stuxnet as the opening of “Pandora’s Box.”
“This malicious program was not designed to steal money, send spam, grab personal data, no, this piece of malware was designed to sabotage plants, to damage industrial systems,” he said.
“I am afraid this is the beginning of a new world. [The] 90’s were a decade of cyber-vandals, 2000’s were a decade of cybercriminals, I am afraid now it is a new era of cyber-wars and cyber-terrorism,” Kaspersky added.
Among industrial security experts who are convinced that Iran is the target of the Stuxnet attack, a debate has opened up around which facility the malware was designed to strike.
Frank Rieger, a German researcher with GSMK, a Berlin encryption firm, suggests that the Natanz enrichment facility looks like the most likely target. He laid out his reasoning to the Christian Science Monitor.
• Stuxnet had a halt date. Internal time signatures in Stuxnet appear to prevent it from spreading across computer systems after July 2009. That probably means the attack had to be conducted by then – though such time signatures are not certain.
• Stuxnet appears designed to take over centrifuges’ programmable logic controllers. Natanz has thousands of identical centrifuges and identical programmable logic controllers (PLCs), tiny computers for each centrifuge that oversee the centrifuge’s temperature, control valves, operating speed, and flow of cooling water. Stuxnet’s internal design would allow the malware to take over PLCs one after another, in a cookie-cutter fashion.
“It seems like the parts of Stuxnet dealing with PLCs have been designed to work on multiple nodes at once – which makes it fit well with a centrifuge plant like Natanz,” Rieger says. By contrast, Bushehr is a big central facility with many disparate PLCs performing many different functions. Stuxnet seems focused on replicating its intrusion across a lot of identical units in a single plant, he says.
Natanz also may have been hit by Stuxnet in mid-2009, Rieger says. He notes that “a serious, recent, nuclear accident” was reported at that time on WikiLeaks, the same organization that recently revealed US Afghanistan-war documents. About the same time, the BBC reported that the head of Iran’s nuclear agency had resigned.
Lending some credence to the notion that Stuxnet attacked more than a year ago, he says, is the International Atomic Energy Agency’s finding of a sudden 15 percent drop in the number of working centrifuges at the Natanz site.
Even though Natanz would seem like a logical target to choose if the objective of the attackers was to disrupt Iran’s nuclear program, Rieger’s inference — that the halt date preventing Stuxnet spreading means the attack had to take place before July 2009 — is questionable, for at least two reasons.
Firstly, given that the designers had a very specific target, their aim is likely to have been to penetrate that target while trying to limit the proliferation of the malware and thus reduce the risks of the operation’s exposure.
Secondly, code for one of the four zero-day vulnerabilities that the worm exploits was only added in March 2010 — well after the halt date. The fact that the code was being modified at that time suggests that it had yet to perform its function.
As previously reported, another German industrial security expert, Ralph Langner, has speculated that the Bushehr nuclear reactor is the most likely target. He bases this theory on various pieces of circumstantial evidence.
Firstly, it is known that Bushehr uses the Siemens SCADA systems that Stuxnet targets and that access to these systems available to Russian contractors working on the facility would allow the malware to be installed through USB memory sticks.
Secondly, photographic evidence shows that the facility had very weak cyber security.
A journalist’s photo from inside the Bushehr plant in early 2009, which Langner found on a public news website, shows a computer-screen schematic diagram of a process control system – but also a small dialog box on the screen with a red warning symbol. Langner says the image on the computer screen is of a Siemens supervisory control and data acquisition (SCADA) industrial software control system called Simatic WinCC – and the little warning box reveals that the software was not installed or configured correctly, and was not licensed. That photo was a red flag that the nuclear plant was vulnerable to a cyberattack, he says.
“Bushehr has all kinds of missiles around it to protect it from an airstrike,” Langner says. “But this little screen showed anyone that understood what that picture meant … that these guys were just simply begging to be [cyber]attacked.”
The picture was reportedly taken on Feb. 25, 2009, by which time the reactor should have had its cybersystems up and running and bulletproof, Langner says. The photo strongly suggests that they were not, he says. That increases the likelihood that Russian contractors unwittingly spread Stuxnet via their USB drives to Bushehr, he says.
“The attackers realized they could not get to the target simply through the Internet – a nuclear plant is not reachable that way,” he says. “But the engineers who commission such plants work very much with USBs like those Stuxnet exploited to spread itself. They’re using notebook computers and using the USBs to connect to one machine, then maybe going 20 yards away to another machine.”
Langner also cites international concern about the Bushehr reactor becoming operational.
This is a somewhat weaker strand of his argument. After all, the existence of this Russian-fueled reactor was widely seen as a demonstration of the fact that Iran could, it it chooses, have a civilian nuclear energy program without any need for a uranium enrichment program.
There is however another argument that can be made in which Bushehr becomes the target of cyberwarfare, even if it might not be a vital node in Iran’s nuclear program. In this scenario, Stuxnet would not be designed to perform its function until the reactor becomes fully operational. At that point, the malware would not simply stop the reactor working — it would trigger a Chernobyl-type nuclear meltdown.
Why would the attackers want to precipitate such a catastrophic event?
- In the hope that such an “accident” would make the Iranian government look unfit to safely operate any kind of nuclear program.
- To undermine Iranian domestic support for the program.
- To alienate Iran from its Gulf neighbors who would be exposed to the fallout.
When John Bolton was last month melodramatically counting the days left for Israel to launch a missile strike on Bushehr, it was ostensibly because once the plant was fueled the Israelis would no longer be willing to risk the lives of so many in the region. With Gulf shipping lanes also closed down for an indeterminate period after an Israeli strike, the global economic impact would be severe.
On the other hand, in the event that Israel struck but did not fire a single missile and could not be shown to be responsible, the results of its own cost-benefit analysis — vastly different from that of the US — might make a devastating cyber attack on Bushehr seem well worth the risk.
In an analysis of Israel’s expanding cyberwarfare capabilities, Scott Borg, director of the US Cyber Consequences Unit, which advises various Washington agencies on cyber security, told Reuters last year that an Israeli attack on an Iranian nuclear facility could employ “malware loitering unseen and awaiting an external trigger, or pre-set to strike automatically when the infected facility reaches a more critical level of activity.”
The decision by Iranian authorities to announce that they have an ongoing investigation on how to thwart Stuxnet, suggests that they may now also be reassessing the risks of bringing Bushehr online as a fully operational facility.
Postscript: Even though discussion on the whole subject of Stuxnet’s purpose and origin is at this point highly speculative, some readers may view my suggestion that the goal is to cause a Chernobyl-type disaster to be a particularly wild conjecture. Maybe it is, but here’s a little more of my thinking on why that would be a plausible objective.
There is little reason to doubt that Israeli leaders from across the political spectrum are serious in their stated objections to Iran’s nuclear program. (Whether those objections correspond with Iran’s genuine nuclear ambitions is another question, as is the question of whether a nuclear-armed Iran would actually pose an existential threat to Israel.)
Among analysts inside and outside Israel there is a broad consensus that military action aimed at crippling Iran’s nuclear facilities would accomplish no more than cause a setback of a few years in the program. The same applies to sabotage.
Given the broad national support the nuclear program has, there is also reason to doubt that regime change would necessarily result in Iran’s enrichment program being scrapped.
What those who fear a nuclear-armed Iran hope to see is a credible political shift as a result of which Iran’s nuclear intentions are no longer in doubt and are demonstrably peaceful. (Which is to say, an ideal end-state similar to the one adopted by South Africa when it chose to abandon nuclear weapons — an ironic comparison of course, given that it was Israel that helped South Africa become a nuclear-armed state.)
For that reason, coercion (through sanctions) and military force are both potentially counterproductive in that pressure generally produces resistance.
On the other hand, the desired outcome might be reached if the Iranians through their own volition came to the conclusion that the costs of nuclear development outweighed the benefits. A catastrophic “accident” might be instrumental in bringing about a change of perspective through which for Iran as a nation, nuclear power lost most of its appeal.
Needless to say, if such an accident was exposed to be the result of an Israeli cyber attack, the plan would dangerously backfire.
Do intelligence agencies come up with such reckless plans? All the time.
Inveterate gamers will no doubt see another possibility here — that Stuxnet is part of a psy-ops plan designed to provoke a greater fear of catastrophic damage than it can actually cause. Possibly, but to identify and then exploit four Windows vulnerabilities suggests that the creators of this malware were willing to employ every possible resource at their disposal. In other words, they were seriously intent on doing damage — not just provoking fear.
Stuxnet: the Trinity test of cyberwarfare

Russian technicians work at Bushehr nuclear power plant in Iran
On August 5, I reported on the strong evidence that Iran had become the target of a state-sponsored cyber attack.
At that point it was already understood that the Stuxnet computer worm was almost certainly targeting Iran since that was the location of 60% of the computer systems affected. Moreover, since the worm targets Siemens SCADA (supervisory control and data acquisition) management systems that control energy utilities, and since its design strongly suggested that it had been created for sabotage, it seemed likely that the specific target was Iran’s nuclear program.
 A German team of industrial cyber security experts who have analyzed the way the worm operates now claim that it may have been designed to attack the newly operational Bushehr nuclear reactor.
A German team of industrial cyber security experts who have analyzed the way the worm operates now claim that it may have been designed to attack the newly operational Bushehr nuclear reactor.
Ralph Langner envisages that the highly sophisticated attack would have required a preparation team that included “intel, covert ops, exploit writers, process engineers, control system engineers, product specialists, military liaison.”
The Christian Science Monitor reports:
Since reverse engineering chunks of Stuxnet’s massive code, senior US cyber security experts confirm what Mr. Langner, the German researcher, told the Monitor: Stuxnet is essentially a precision, military-grade cyber missile deployed early last year to seek out and destroy one real-world target of high importance — a target still unknown.
“Stuxnet is a 100-percent-directed cyber attack aimed at destroying an industrial process in the physical world,” says Langner, who last week became the first to publicly detail Stuxnet’s destructive purpose and its authors’ malicious intent. “This is not about espionage, as some have said. This is a 100 percent sabotage attack.”
On his website, Langner lays out the Stuxnet code he has dissected. He shows step by step how Stuxnet operates as a guided cyber missile. Three top US industrial control system security experts, each of whom has also independently reverse-engineered portions of Stuxnet, confirmed his findings to the Monitor.
“His technical analysis is good,” says a senior US researcher who has analyzed Stuxnet, who asked for anonymity because he is not allowed to speak to the press. “We’re also tearing [Stuxnet] apart and are seeing some of the same things.”
Other experts who have not themselves reverse-engineered Stuxnet but are familiar with the findings of those who have concur with Langner’s analysis.
“What we’re seeing with Stuxnet is the first view of something new that doesn’t need outside guidance by a human – but can still take control of your infrastructure,” says Michael Assante, former chief of industrial control systems cyber security research at the US Department of Energy’s Idaho National Laboratory. “This is the first direct example of weaponized software, highly customized and designed to find a particular target.”
“I’d agree with the classification of this as a weapon,” Jonathan Pollet, CEO of Red Tiger Security and an industrial control system security expert, says in an e-mail.
Langner’s research, outlined on his website Monday, reveals a key step in the Stuxnet attack that other researchers agree illustrates its destructive purpose. That step, which Langner calls “fingerprinting,” qualifies Stuxnet as a targeted weapon, he says.
Langner zeroes in on Stuxnet’s ability to “fingerprint” the computer system it infiltrates to determine whether it is the precise machine the attack-ware is looking to destroy. If not, it leaves the industrial computer alone. It is this digital fingerprinting of the control systems that shows Stuxnet to be not spyware, but rather attackware meant to destroy, Langner says.
Langer speculates that Iran’s Bushehr nuclear power plant may have been the Stuxnet target. He also writes: “The forensics that we are getting will ultimately point clearly to the attacked process — and to the attackers. The attackers must know this. My conclusion is, they don’t care. They don’t fear going to jail.”
If Bushehr was indeed the target, it may have presented itself first and foremost as a target of opportunity. From the point of view of governments with an interest in sabotaging Iran’s nuclear program, Bushehr would not be the most attractive target, but access provided to Russian contractors may have made it the easiest target.
Last September, Reuters reported: “Israel has been developing ‘cyber-war’ capabilities that could disrupt Iranian industrial and military control systems.”
So let’s assume that using Stuxnet, Israel has indeed launched the world’s first precision, military-grade cyber missile. What are the implications?
1. Iran has been served notice that not only its nuclear facilities but its whole industrial infrastructure is vulnerable to attack. As Trevor Butterworth noted: “By demonstrating how Iran could so very easily experience a Chernobyl-like catastrophe, or the entire destruction of its conventional energy grid, the first round of the ‘war’ may have already been won.”
2. The perception that it has both developed capabilities and shown its willingness to engage in cyberwarfare, will serve Israel as a strategic asset even if it never admits to having launched Stuxnet.
3. When it comes to cyberwarfare, Israel ranks as a major global power. It’s own tiny infrastructure makes it much less vulnerable to attack than is the sprawling infrastructure of the United States. It’s highly developed military IT industry means that it not only has great domestic human resources but that Israeli IT specialists, through research and employment, have the best possible access to most of the leading development facilities and vendors around the world.
4. As a cyber arms race takes off, we should not imagine that it will be like other arms races where power resides more in capabilities than in the use of those capabilities. “Whereas nuclear weapons have been used twice in human history, cyber weapons are employed daily and there is therefore an existential need to create some form of regulatory system that allows more than implicit deterrence,” says Robert Fry.
5. If AQ Khan demonstrated the ease with which a nuclear proliferation network can operate, the fact that the raw material upon which cyberwarfare is based is arguably the most easily transferable object on the planet — computer code — means that in certain ways the era of cyberwarfare may prove to be more dangerous than the nuclear era.
6. In the strategic landscape of cyberwarfare the most dangerous player may turn out to be a small but highly developed fortress-state that feels threatened by much of the rest of the world; that neither trusts nor is trusted by any of its allies; that sees its own stability enhanced by regional instability; that has seen its own economic fortunes rise while the global economy suffers; and that views with contempt the notion of an international community.