Chelsea Wald writes: In his free time, Sven Laumer serves as a referee for Bavaria’s highest amateur football league. A few years ago, he noticed several footballers had quit Facebook, making it hard to organize events on the platform. He was annoyed, but as a professor who studies information systems, he was also intrigued. Why would the young men want to give up Facebook? Social scientists had been saying the social network was a good thing.
“At the time, the main paradigm in social networking research was that Facebook is a positive place, it’s a place of happiness, it’s a place where you have fun, you get entertained, you talk to friends, you feel amused, accepted,” says Hanna Krasnova, an information systems researcher at the University of Bern in Switzerland. Influential studies had shown that the social capital we earn on social media can be key to our successes, big and small. Our virtual connections were known to help us access jobs, information, emotional support, and everyday favors. “Everyone was enthusiastic about social media,” Laumer says.
Laumer, an assistant professor at Otto-Friedrich University in Germany, suspected that quitting Facebook was a classic response to stress. He knew other researchers had looked at something called “technostress,” which crops up in workplaces due to buggy interfaces or complex processes. But that didn’t really fit with Facebook, which is easy to use. Something else seemed to be stressing people out. “We thought there was a new phenomenon on social media in particular,” Laumer says.
Through probing interviews, surveys, longitudinal studies, and laboratory experiments, researchers have begun to shift the paradigm, revealing that Facebook, Twitter, Instagram, Snapchat, and their ilk are places not only of fun and success, but of dark, confronting, and primal human emotions—less Magic Kingdom and more creepy fun house. In many ways, researchers say, these platforms are giant experiments on one of our species’ most essential characteristics: our social nature. So it shouldn’t be a surprise there are unintended consequences. [Continue reading…]
Category Archives: internet
Why does Donald Trump tell so many lies?
The more lies Donald Trump tells, the larger the frustration grows — the greater the sense that Trump continues lying because he’s being allowed to get away with it.
The New York Times says:
Mr. Trump relies on social media to spread his views. This is convenient because there’s no need to respond to questions about his fabrications. That makes it imperative that other forms of media challenge him.
Instead, as Mr. Trump stays at the top of the Republican field, it’s become a full-time job just running down falsehoods like the phony crime statistics he tweeted, which came from a white supremacist group.
Yet Mr. Trump is regularly rewarded with free TV time, where he talks right over anyone challenging him, and doubles down when called out on his lies.
This isn’t about shutting off Mr. Trump’s bullhorn. His right to spew nonsense is protected by the Constitution, but the public doesn’t need to swallow it. History teaches that failing to hold a demagogue to account is a dangerous act. It’s no easy task for journalists to interrupt Mr. Trump with the facts, but it’s an important one.
MSNBC host Lawrence O’Donnell says “Donald Trump lies because he knows he can get away with it.”
O’Donnell also says Trump exploits the politeness of his interviewers and that they are afraid of challenging him because they are afraid he won’t show up for future interviews.
Trump’s antics are boosting the ratings of both supporters and critics in the media.
But I don’t think Trump continues lying simply because he can get away with it, or because the media is too polite to call him a liar, or because since he is a pathological liar he just can’t stop lying.
The reason he keeps on lying is because, paradoxically, among his supporters it reinforces his image as a truth-teller.
Since Trump supporters think that “the media” and “media lies” are synonyms, and since in a polls have shown “liar” (at least until recently) was a phrase more commonly linked to Hillary Clinton than Trump, and since the political establishment is widely viewed as being filled with liars, it matters much less to Trump that he is being called a liar than it does who is calling him that.
If each time Trump gets called a liar and Trump’s base see his accusers themselves as liars, the accusation not only loses its sting — it ends up looking like a vindication, proof that Trump is rocking the establishment.
What’s the solution?
For a start, the media needs to stop giving Trump so much free airtime. And that means refraining from following the currently irresistible impulse to profit from his notoriety.
A presidential election should be about issues, not antics, and it’s up to the media to cover the issues.
The endless recurrence of the clash of civilizations narrative
Marc Lynch writes: Jihadists have always sought to use terrorism to polarize politics, spread their ideas, discredit moderates and advance their preferred narrative of clashing civilizations. They have not always been so successful [as they are now] in winning mainstream acceptance for their narrative.
I would highlight three possible explanations. One part of the answer may be the pervasive effects of social media. By this I do not mean the Islamic State’s use of social media for recruitment and propaganda, as impressive and interesting as this phenomenon has been. Instead, I mean the ways in which social media itself is structured, creating new openings for extreme ideas to gain traction with the broader public. Social media networks typically tend to encourage ideological clustering, in which self-selected communities of the like-minded cultivate shared narratives, identities and arguments. Today’s pervasive social media is organically interwoven with broadcast media and more traditional print publications in ways that facilitate the movement of these narratives from isolated clusters into the mainstream. The 9/11 attacks took place at a moment when blogs had only just begun to reshape the American political public sphere, but the Islamic State’s rise has occurred in an era of near complete social mediation of information and opinion. Such an environment seems highly conducive to the cultivation and nurturing of radical fringe ideas – and their transmission into the broader public arena.
A second strand is the absence of George W. Bush. For all his other foreign policy struggles, Bush was staunchly opposed to the demonization of Islam, and frequently argued — as Hillary Clinton does today — that America was not at war with Islam. He understood the importance of denying the al-Qaeda narrative of a clash of civilizations. Bush’s stance acted as a check on the anti-Islamic impulses of the right wing base. That obstacle has long since passed from the scene. President Obama’s invocation of the same themes invites the opposite response. The right wing now can be unified against this rhetoric, without Bush to restrain them. Meanwhile, the waning of the Obama presidency has encouraged a large portion of the policy community to position themselves against the outgoing administration, which typically means adopting more hawkish and interventionist positions. By the old political math, the majority of Democrats combined with the Bush Republicans to block the anti-Islamic trend. By the new political math, the vast majority of Republicans combines with enough Democrats to push the “center” well to the right.
A third factor is the real changes within the Islamist landscape, far beyond the Islamic State itself. Syria has generated a wide variety of jihadist groups, which often position themselves against the Islamic State. Local insurgencies that once took on the al-Qaeda label now embrace the Islamic State’s franchise. Above all, the 2013 Egyptian military coup and subsequent repressive campaign against the Muslim Brotherhood severely weakened one of al-Qaeda’s traditionally most powerful competitors. The destruction and demonization of the Brotherhood has likely contributed to eroding the idea of a mainstream Islamism buffering the jihadists. The political push by Egypt, Saudi Arabia and the United Arab Emirates to label the Brotherhood a terrorist organization has reshaped the politics of the issue as well. Propaganda from the region against the Muslim Brotherhood then refracts through the Western public discourse. Old debates revolving around the Brotherhood’s role as a firewall against extremism are now far less relevant, with its organization shattered and ideology of peaceful participation discredited. Analysts who follow Islamism closely are now in uncharted territory, creating openings for those peddling simple, well-rehearsed narratives about Islam. [Continue reading…]
New ISIS video threatening New York City uses stock images
The fact that a new ISIS video threatening New York City uses snippets from commercial videos available on YouTube, does not mean that the threat can be dismissed.
It does, nevertheless, indicate that the imagery in this video should not be taken at face value. This is not footage that was filmed on the ground by would-be attackers.
It’s reasonable to assume that ISIS produced the sections of the video showing a bomb being assembled, but they have then spliced these together with stock footage in a slick piece of editing that creates the appearance of a single production.
In one snippet of the ISIS video, we see a tracking shot showing taxis stopped at an intersection next to a Gap store:
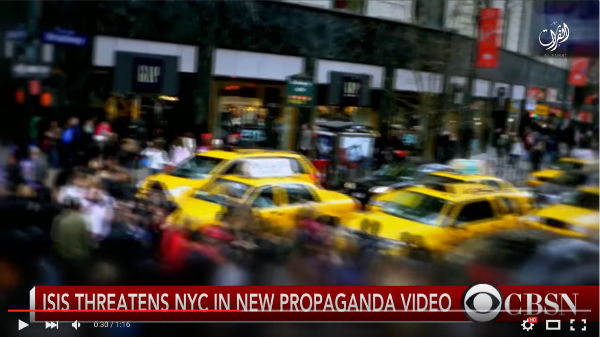
This comes from a video made by StockFootage.com “Fast tracking shot of crowded street in nyc.“:

The ISIS video shows a TGI Friday’s:
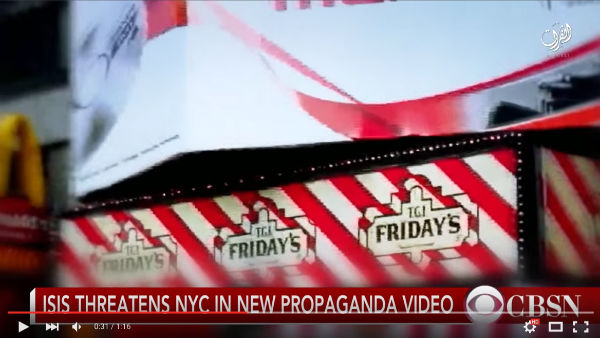
This comes from another StockFootage.com video, “Panning shots of signs in Times Square New York City“:

Can a bunch of hackers really take on ISIS?
writes: For John Chase, the breaking point came on Jan. 7, when al Qaeda-linked militants gunned down 12 people at the Paris office of Charlie Hebdo. Subsequent attacks by a gunman affiliated with the Islamic State would take five more lives. Watching triumphant jihadi messages bounce across Twitter, the 25-year-old Boston native was incensed. They needed to be stopped.
Although Chase’s formal education ended with high school, computers were second nature to him. He had begun fiddling with code at the age of 7 and freelanced as a web designer and social media strategist. He now turned these skills to fighting the Islamic State, also known as ISIS. Centralizing other hacktivists’ efforts, he compiled a database of 26,000 Islamic State-linked Twitter accounts. He helped build a website to host the list in public view and took steps to immunize it against hacking counterattacks by Islamic State sympathizers. He even assumed an appropriately hacker-sounding nom de guerre, “XRSone,” and engaged any reporter who would listen. In doing so, Chase briefly became an unofficial spokesman for #OpISIS — and part of one of the strangest conflicts of the 21st century.
For more than a year, a ragtag collection of casual volunteers, seasoned coders, and professional trolls has waged an online war against the Islamic State and its virtual supporters. Many in this anti-Islamic State army identify with the infamous hacking collective Anonymous. They are based around the world and hail from every walk of life. They have virtually nothing in common except a passion for computers and a feeling that, with its torrent of viral-engineered propaganda and concerted online recruiting, the Islamic State has trespassed in their domain. The hacktivists have vowed to fight back.
The effort has ebbed and flowed, but the past nine months have seen a significant increase in both the frequency and visibility of online attacks against the Islamic State. To date, hacktivists claim to have dismantled some 149 Islamic State-linked websites and flagged roughly 101,000 Twitter accounts and 5,900 propaganda videos. At the same time, this casual association of volunteers has morphed into a new sort of organization, postured to combat the Islamic State in both the Twitter “town square” and the bowels of the deep web.
Chase, who has since shifted his focus to other pursuits, boasts a story typical of those volunteers who work to track and counteract the Islamic State’s online propaganda apparatus. Few of these hacktivists are hood-wearing, network-cracking, Internet savants. Instead, they are part-time hobbyists, possessed of a strong sense of justice and a disdain for fundamentalists of all stripes. Many, but not all, are young people — some are more seasoned, former military or security specialists pursuing a second calling. The oldest is 50. These hacktivists speak of a desire to “do something” in the fight against the Islamic State, even if that “something” may sometimes just amount to running suspicious Twitter accounts through Google Translate.
This is something new. Anonymous arose from the primordial, and often profane, underground web forums to cause mischief, not to take sides in real wars. The group gained notoriety for its random, militantly apolitical, increasingly organized hacking attacks during the mid-2000s. Its first “political” operation was an Internet crusade against the Church of Scientology following its suppression of a really embarrassing Tom Cruise video.
In time, however, Anonymous operations became less about laughs and more about causes, fighting the establishment and guaranteeing a free and open Internet. [Continue reading…]
Our web history reveals what we think and do. Shouldn’t that remain private?
By Paul Bernal, University of East Anglia
An overlooked aspect of the draft Investigatory Powers Bill is the significance of demanding that service providers store 12 months’ internet connection records. A record of every website visited and internet service connected to, the government presents this as the online equivalent of an itemised phone bill. But this is a false analogy: internet connection records carry far more detail than a phone book, and the government’s move to claim them represents an unprecedented intrusion into our lives.
Supporters of the bill suggest that this data provides a way of checking that someone accessed Facebook at a particular time, just as phone records can reveal that a user called a particular number at a certain time. But while this is true, it misunderstands the role the internet has in our lives, and consequently underplays how much it can reveal.
The phone is a communications tool, but we have complex online lives and use the internet for many things other than “communication”. We do almost everything online: we bank online, we shop, find relationships, listen to music, watch television and films, plan our holidays, read about and indulge our interests.
Access to the websites we visit, for an entire year, is not at all comparable to having an itemised telephone bill. It’s more equivalent to tailing someone as they visit the shops, the pub, the cinema, listen to the radio, go to the park and on holiday, read books and magazines and newspapers, and much more.
It’s not just the data that’s revealing, it’s the sort of direct, logical inferences that can be made given a web browsing history. For example, from the fact that someone visits sites connected with a particular religion, one can infer that they follow that religion. If they visit sites regarding a particular health condition, it’s possible to infer that they may suffer from that condition, or are worried about their health.
ISIS has a new favorite social media network: Telegram
The Fiscal Times reports: Terror Jihadi groups like ISIS and al-Qaeda are now shifting much of their social media propaganda, recruiting and fund transferring from mainstream social media sites like Twitter to a service called Telegram, according to a new report by the Terrorism Research and Analysis Consortium (TRAC).
ISIS and other militant groups have been jumping from one social media service to another in their attempts to avoid anti-terrorism programs by governments and corporations. They appear to have settled on Telegram. “The Jihadis’ struggle to keep up with the relentless suspensions and removal of jihadi social media content may have finally run its course,” says Veryan Khan, the Editorial Director at TRAC. “The new frontier of jihadi communication is taking place on a recently launched tool, in a messaging platform that has revolutionized the social media sphere.”
Telegram was launched in August 2013 by the two Russian brothers, Nicolay and Pavel Durov, as a free encrypted instant messaging service. While reports of terror groups using Telegram surfaced months ago, a new feature called “Channels” was launched in September to let users broadcast to other members of the service. It quickly turned Telegram into the favorite social media hub of ISIS and other terror groups.
“It is this new feature that has been enthusiastically embraced by many militant groups, becoming an underground railroad for distributing and archiving jihadi propaganda materials,” the TRAC report says.
As of Nov. 2, TRAC has recorded more than 200 major jihadi channels. Half of them belong to ISIS. Other major players in the jihadi world, from al Qaeda in the Arabian Peninsula to Jabhat al-Nusra to Ansar al-Sharia in Libya to Jaysh al-Islam, are increasingly creating their own channels. The rate of membership growth for the channels has been staggering, quickly climbing to about 150,000 total members, the report concludes.
“The sheer scale and momentum of the Telegram migration is hard to fathom,” says Brian Watts, an author of the TRAC report. “The force of the numbers using Telegram channels is staggering, watching hundreds of new members in an hours’ time; thousands coming on in over a few days is commonplace for many channels.” [Continue reading…]
British government’s new plans for mass surveillance welcomed by opposition
The Guardian reports: New surveillance powers will be given to the police and security services, allowing them to access records tracking every UK citizen’s use of the internet without any judicial check, under the provisions of the draft investigatory powers bill unveiled by Theresa May.
It includes new powers requiring internet and phone companies to keep “internet connection records” – tracking every website visited but not every page – for a maximum of 12 months but will not require a warrant for the police, security services or other bodies to access the data. Local authorities will be banned from accessing internet records.
The proposed legislation will also introduce a “double-lock” on the ministerial approval of interception warrants with a new panel of seven judicial commissioners – probably retired judges – given a veto before they can come into force.
But the details of the bill make clear that this new safeguard for the most intrusive powers to spy on the content of people’s conversations and messages will not apply in “urgent cases” – defined as up to five days – where judicial approval is not possible.
The draft investigatory powers bill published on Wednesday by the home secretary aims to provide a “comprehensive and comprehensible” overhaul of Britain’s fragmented surveillance laws. It comes two-and-a-half years after the disclosures by the whistleblower Edward Snowden of the scale of secret mass surveillance of the global traffic in confidential personal data carried out by Britain’s GCHQ and the US’s National Security Agency (NSA).
It will replace the current system of three separate commissioners with a senior judge as a single investigatory powers commissioner.
May told MPs that the introduction of the most controversial power – the storage of everyone’s internet connection records tracking the websites they have visited, which is banned as too intrusive in the US and every European country including Britain – was “simply the modern equivalent of an itemised phone bill”.
Her recommendations were broadly welcomed by the shadow home secretary, Andy Burnham, but received a more cautious welcome from the former Conservative shadow home secretary David Davis, the former shadow home secretary Yvette Cooper and Nick Clegg, the former deputy prime minister. [Continue reading…]
The third dimension: Why Amazon just opened a bookstore
In all honesty, I don’t know why Amazon just opened a physical bookstore in Seattle.
Maybe they want to drive the last remaining independent bookstores out of business by stealing their employees. Maybe it’s a memorial to commemorate the form of brick-and-mortar retail the online corporation has been so successful in destroying — a nostalgic return designed to remind customers of its own obsolesce.
On the other hand, this could be a semi-conscious token recognition that online is not in all ways expansive. It’s not just bigger, faster, cheaper, better.
The price of using a screen is that through its surface we step away from three-dimensional space.
Although the physical internet exists in three-dimensional space, we can only connect through a two-dimensional display.
Even though the tool for navigating through digital space has traditionally been called a browser, a screen marshals attention in ways that physical browsing does not.
Wandering around a bookstore, scanning titles along bookshelves and leafing through pages, are physical actions that can only take place in physical space. And that space has fuzzy boundaries.
When we examine a book in our hands, we can feel its weight, see the font style and size, the quality of the binding, open pages at random and engage with this physical object in a much richer and more complex way than through a digital window.
This physicality points to an even more basic disjunction between corporeal existence and digital activity.
However entwined our lives have become with electronic devices, we remain creatures confined at any one moment to one place in the universe.
Increasingly, however, our lives are disconnected from where we are. People come together and then their phones step between them.
We are forever being beckoned to be some place else.
The end of all our exploring may never come if we fail to return where we started.
The dangerous consequences of routinized venomousness in public life
Pankaj Mishra writes: In the guise of hyper-patriotism, trash talk has gone mainstream in the world’s two biggest democracies. Donald Trump, the leading candidate in Republican primaries, set a new low in public discourse by calling Mexican immigrants “rapists.” The Hindu nationalist chief minister of one of India’s richest states recently underscored the deterioration in India’s political culture by declaring Muslims could only live in the country if they stopped eating beef.
One hopes that a dignified retort of the kind that defused the menace of McCarthyism — “Have you no decency, sir?” — terminates this season of demagogues. But public support for them suggests that a disturbingly broad assault is underway on democratic values — indeed, on civility itself.
People foaming at the mouth with hate and malice have become a common sight on both traditional and social media. Mobs in India and mass shooters in America have thrived in this climate of irrationalism. Many people, it seems, can think only in the categories of friends and foes, group loyalty or treason; their preference for abuse kills all possibilities of reasoned debate. [Continue reading…]
Everything you need to know about the vast network of undersea cables that makes the Internet global
The Washington Post reports: Russians submarines and spy ships are “aggressively operating” near the undersea cables that are the backbone of the global Internet — worrying some U.S. intelligence and military officials who fear the Russians may sabotage them if a conflict arises, the New York Times reports.
For all the talk about the “cloud,” practically all of the data shooting around the world actually relies on a series of tubes to get around — a massive system of fiber-optic cables lying deep underneath the oceans.
The network connects every continent other than Antarctica, carrying e-mails, photos, videos and emoji around the globe. Here’s what that looks like in the style of a vintage maritime map, courtesy of TeleGeography: [Continue reading…]
ISIS’s online recruitment strategy
J.M. Berger writes: Observers have focused, rightly, on the quality and quantity of Islamic State propaganda as a factor in its success, but passive material can only take the typical radicalization so far. Therefore, the organization deploys a wide variety of tailored online interventions to bring their targets into the fold.
Sometimes referred to as “grooming,” these interventions are conducted by small teams of prolific social media users who lavish attention on potential recruits in order to shape their worldview and encourage direct action in support of the Islamic State, ranging from lone wolf–style terrorist attacks to migration to Islamic State territories. Some interveners are more formally affiliated with the Islamic State while others appear to be informal volunteers.
Online interventions are more prevalent in countries where the social climate offers few opportunities to safely discuss an interest in the Islamic State in a face-to-face setting, but even in such environments, many cases incorporate activity that crosses over from online to real-world interactions. [Continue reading…]
How pro-Kremlin tweeps are framing the Syrian debate
RFE/RL reports: Support among Russians for military intervention in Syria has more than doubled, to 31 percent in early October from 14 percent in September, according to independent pollster Levada Center.
The increase comes with coverage of air strikes filling Russian state airwaves, press, and the Internet, and social-media salvoes fired from both sides of the debate.
On social networks like Twitter, expressions of support for Moscow’s air raids appear to fit into three distinct categories: perceived cultural and historical affinities between Syria and Russia; purported Western helplessness in the face of the continuing Syrian crisis; and the conflation of any armed forces opposing Syrian President Bashar al-Assad’s regime under the “terrorist” banner. [Continue reading…]
If you’re not paranoid, you’re crazy
Walter Kirn writes: I knew we’d bought walnuts at the store that week, and I wanted to add some to my oatmeal. I called to my wife and asked her where she’d put them. She was washing her face in the bathroom, running the faucet, and must not have heard me—she didn’t answer. I found the bag of nuts without her help and stirred a handful into my bowl. My phone was charging on the counter. Bored, I picked it up to check the app that wirelessly grabs data from the fitness band I’d started wearing a month earlier. I saw that I’d slept for almost eight hours the night before but had gotten a mere two hours of “deep sleep.” I saw that I’d reached exactly 30 percent of my day’s goal of 13,000 steps. And then I noticed a message in a small window reserved for miscellaneous health tips. “Walnuts,” it read. It told me to eat more walnuts.
It was probably a coincidence, a fluke. Still, it caused me to glance down at my wristband and then at my phone, a brand-new model with many unknown, untested capabilities. Had my phone picked up my words through its mic and somehow relayed them to my wristband, which then signaled the app?
The devices spoke to each other behind my back—I’d known they would when I “paired” them—but suddenly I was wary of their relationship. Who else did they talk to, and about what? And what happened to their conversations? Were they temporarily archived, promptly scrubbed, or forever incorporated into the “cloud,” that ghostly entity with the too-disarming name?
It was the winter of 2013, and these “walnut moments” had been multiplying—jarring little nudges from beyond that occurred whenever I went online. One night the previous summer, I’d driven to meet a friend at an art gallery in Hollywood, my first visit to a gallery in years. The next morning, in my inbox, several spam e-mails urged me to invest in art. That was an easy one to figure out: I’d typed the name of the gallery into Google Maps. Another simple one to trace was the stream of invitations to drug and alcohol rehab centers that I’d been getting ever since I’d consulted an online calendar of Los Angeles–area Alcoholics Anonymous meetings. Since membership in AA is supposed to be confidential, these e‑mails irked me. Their presumptuous, heart-to-heart tone bugged me too. Was I tired of my misery and hopelessness? Hadn’t I caused my loved ones enough pain? [Continue reading…]
When you develop the habit of distraction, it becomes harder and harder to think deeply
Huffington Post spoke to Nicholas Carr who five years ago wrote in his book, The Shallows: How The Internet Is Changing Our Brains, about the way technology seemed to be eroding our ability to concentrate:
Are you optimistic about any of the ways we currently seem to be adapting [to the constant flow of information through digital devices]?
No. It’s the ease with which we adapt that makes me most nervous. It doesn’t take long for someone to get used to glancing at their smartphone 200 times a day. We’re creatures of habit mentally and physically.
When you develop that habit of distraction, it becomes harder and harder to back away and engage our minds in deeper modes of thinking.
Is there anything we can do to keep our mental faculties intact, or is it pretty much hopeless at this point?
Well, you can use the technology less and set aside your phone and spend a good part of your day trying to maintain your focus and not be interrupted. The good thing about that — because of the plasticity of our brains — is that if you change your habits, your brain is happy to go along with whatever you do.
What makes me more pessimistic is that we’re kind of building our personalities and our entire societies around this new set of norms and expectations that says you need to be constantly connected. As long as we continue going down that path it’s going to be ever harder for us to buck the status quo. [Continue reading…]
The Red Web: Russia and the Internet
Steven Aftergood writes: The Internet in Russia is a battleground between activists who would use it as a tool of political and cultural freedom and government officials who see it as a powerful instrument of political control, write investigative journalists Andrei Soldatov and Irina Borogan in their new book The Red Web. For now, the government appears to be winning the battle.
Soldatov and Borogan trace the underlying conflict back to official anxiety in the Soviet era about the hazards of freedom of information. In the 1950s, the first Soviet photocopy machine was physically destroyed at the direction of the government “because it threatened to spread information beyond the control of those who ruled.”
With the introduction of imported personal computers in the 1980s and a connection to the Internet in 1990, new possibilities for free expression and political organizing in Russia seemed to arise. But as described in The Red Web, each private initiative was met by a government response seeking to disable or limit it. Internet service providers were required to install “black boxes” (known by the acronym SORM) giving Russia’s security services access to Internet traffic. Independent websites, such as the authors’ own agentura.ru site on intelligence matters, were subject to blocking and attack. Journalists’ computers were seized.
But the struggle continued. Protesters used new social media tools to organize demonstrations. The government countered with new facial recognition technology and cell phone tracking to identify them. Large teams of “trolls” were hired to disrupt social networks. A nationwide system of online filtering and censorship was put in place by 2012, and has been refined since then. [Continue reading…]
How Edward Snowden inadvertently helped Vladimir Putin’s internet crackdown
Andrei Soldatov and Irina Borogan write: In the 1990s the global nature of the Internet meant wires. When a user got connected, he could send his e-mail or visit a website anywhere in the world. In the 2000s the Internet meant the rise of global platforms that allowed users to share the same social networks, email services, search engines, and clouds. The Internet became more of a common ground for people from Argentina to Russia — they used the same Facebook, the same Twitter. That also meant that the information users exchanged was stored inside systems located far from the users — systems that could not be readily controlled by nations, their leaders, or their secret services. Most of the servers were located in the United States.
For Russian President Vladimir Putin, this was intolerable. In his mind the solution was simple: force the platforms — Facebook, Google, Twitter, and Apple among them — to locate their servers on Russian soil so Russian authorities could control them.
The challenge was how to do it.
The Kremlin obviously needed a pretext to put pressure on the global platforms to relocate their servers, and Edward Snowden’s revelations provided the perfect excuse to start the offensive. The members of the Russian parliament chosen by the Kremlin to define Internet legislation rushed to comment on his revelations. Legislation forcing global platforms to store Russians’ personal data in Russia was soon adopted, and came into force on Tuesday [Sept. 1], sending Western tech giants scrambling to comply. Russian censors announced plans to blacklist websites including Wikipedia, Github, the Wayback Machine, and BuzzFeed. Snowden had no say in the matter. [Continue reading…]
Ad industry may gripe about adblockers, but they broke the contract – not us
By Andrew McStay, Bangor University
The latest version of Apple’s operating system for phones and tablets, iOS9, allows the installation of adblocking software that removes advertising, analytics and tracking within Apple’s Safari browser. While Apple’s smartphone market share is only around 14% worldwide, this has prompted another outpouring from the mobile and web advertising industry on the effects of adblockers, and discussion as to whether a “free” web can exist without adverts.
It’s not a straightforward question: advertising executives and publishers complain that ads fund “free” content and adblockers break this contract. Defenders of adblocking point out that the techniques used to serve ads are underhand and that the ads themselves are intrusive. Who is right?

